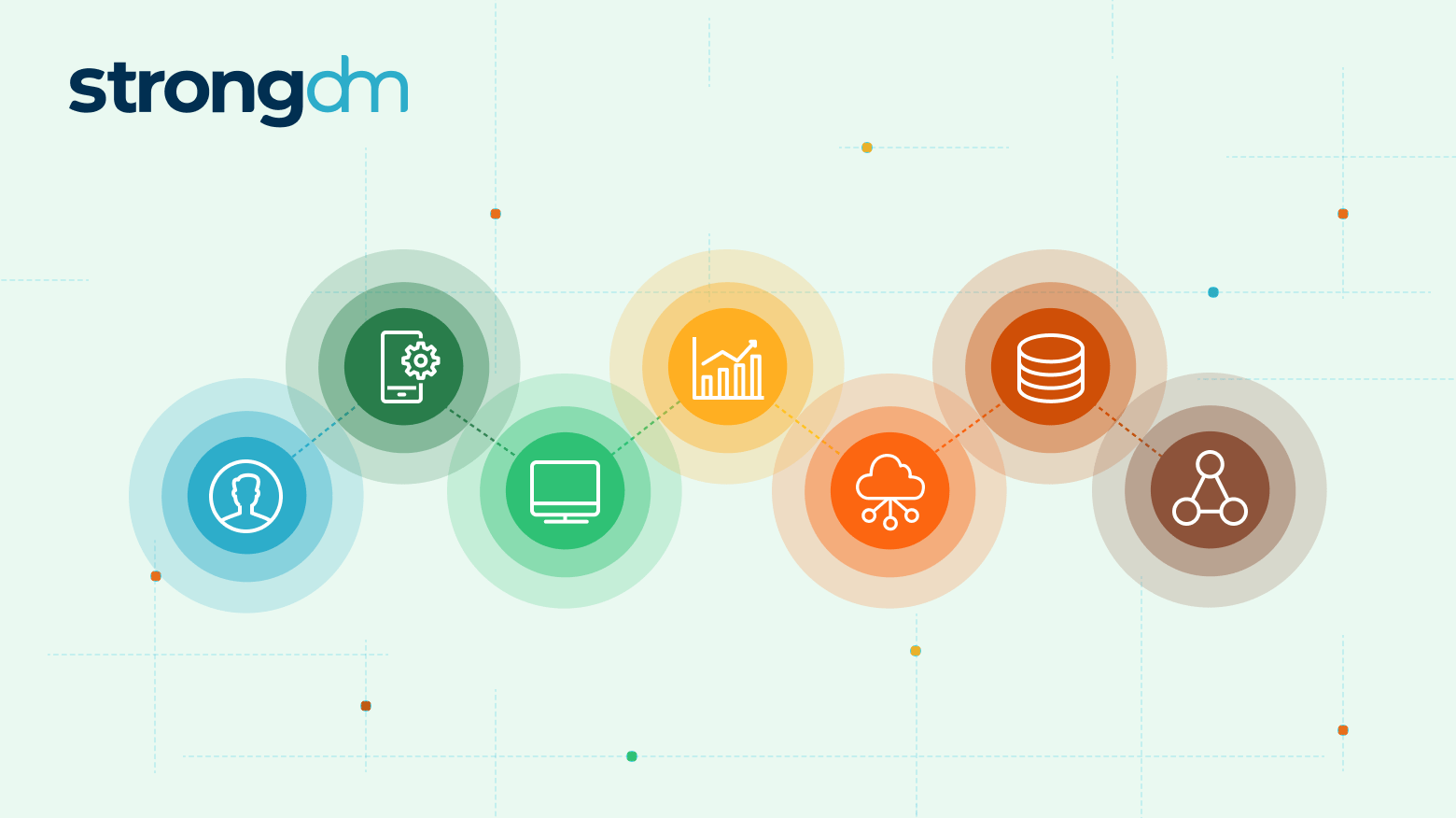
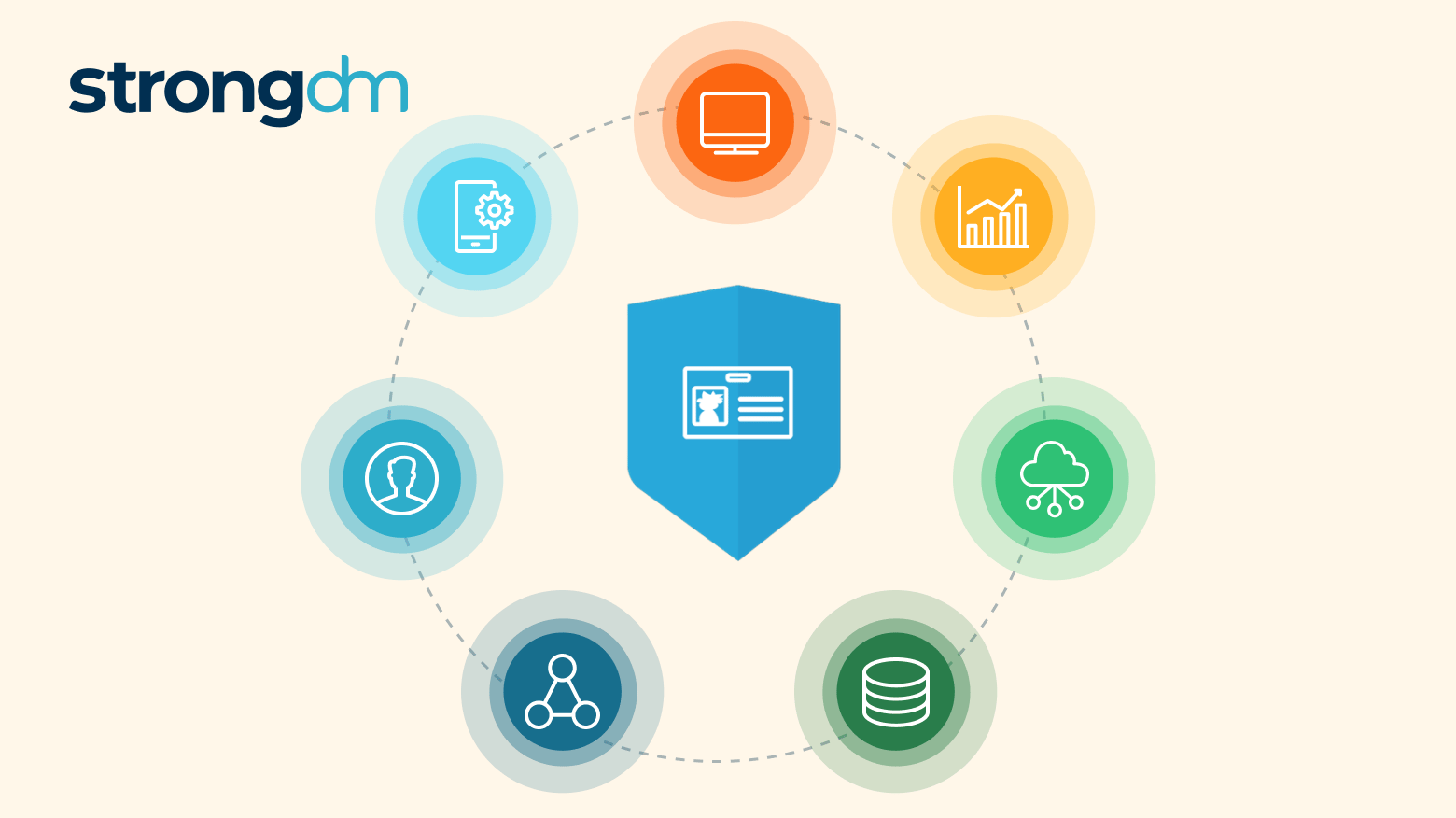
Vendor Access Management (VAM) is the systematic control and oversight of vendor access to an organization's systems, applications, and data. It involves processes such as onboarding and offboarding vendors, utilizing solutions for Just-in-Time access, ensuring security, and streamlining workflows to minimize operational inefficiencies.