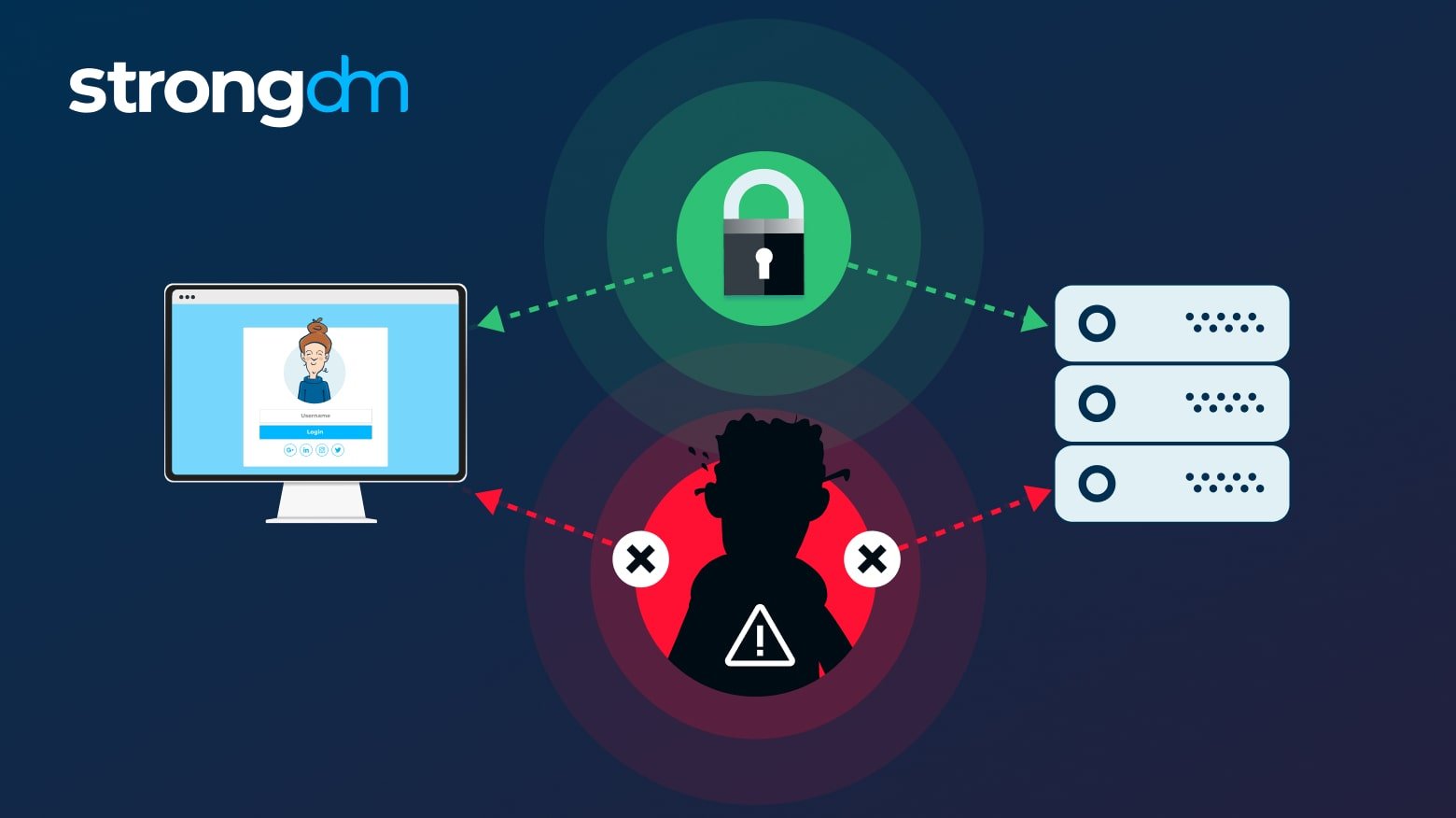
Context-based access controls refer to a dynamic and adaptive approach to managing security policies in modern infrastructure. Addressing challenges in enforcing consistent security across diverse platforms, these policies consider factors such as device posture and geo-location to adjust access controls dynamically. By narrowing access based on contextual parameters, they reduce the attack surface, enhance security, and streamline policy administration, ensuring compliance in evolving




![How to Prevent Credential Stuffing [9 Best Practices]](https://discover.strongdm.com/hubfs/credential-stuffing-prevention.png)