Non-human identities are fueling secrets sprawl, and vaults alone can’t stop it. Learn why NHIs are the primary source of leaked secrets, the limits of traditional secret stores, and how StrongDM governs access in real time without exposing credentials.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
Discover why traditional secrets management isn't enough. StrongDM Managed Secrets offers vault-agnostic, Zero Trust security with secretless access, dynamic policy enforcement, automated rotation, and unified audits—perfect for complex enterprise environments.
Secrets management is the practice of securely storing, accessing, and controlling digital authentication credentials such as passwords, API keys, certificates, and tokens used by applications and systems. It ensures that sensitive information is protected from unauthorized access, while supporting automation, compliance, and security across modern infrastructure.
As enterprises increasingly migrate workloads to the cloud, security strategies must adapt to meet evolving threats. Zero Trust, emphasizing identity verification and least privilege access, has become a critical framework for securing cloud environments. StrongDM’s recent survey of 600 cybersecurity professionals sheds light on the progress and challenges organizations face in adopting Zero Trust for the cloud.
I’ll spare you the “I drink your milkshake” tropes, but we all face a sobering reality: there will be breaches in 2025. Breaches aren’t a question of “if” anymore—they’re a question of “when” and “how bad.” It’s a foregone conclusion, like taxes or the 37th season of Grey’s Anatomy. But here’s the good news: knowing the inevitability of breaches gives us the perfect opportunity to prepare, if we have the will – and strategy – oh, and tools – to do it. And no, I’m not talking about the “build a

Discover how StrongDM's Zero Trust PAM and fine-grained authorization secure cloud data plane access and mitigate shadow access risks without hindering productivity.

Learn why Just-in-Time (JIT) access is essential for Zero Trust security in AWS environments. Discover how StrongDM's JIT access enhances security, optimizes workflows, and ensures compliance with Zero Trust principles.
Let’s talk about the unsung heroes of your on-premises infrastructure: network devices. These are the routers, switches, and firewalls that everyone forgets about…and takes for granted—until something breaks. And when one of those somethings breaks, it leads to some pretty bad stuff. If your network goes down, that’s bad, bad, bad for business. But if those devices lack the necessary security, well, that can leave you exposed in an incredibly dangerous way.
Zero Trust cloud security is a cybersecurity model that operates on the principle that no user, device, system, or action should be trusted by default — even if it's inside your organization’s own network. This approach minimizes the risk of breaches and other cyber threats by limiting access to sensitive information and resources based on user roles, device security posture, and contextual factors.
Zero Trust Data Protection isn't just the best way to safeguard your data — given today's advanced threat landscape, it's the only way. Assuming inherent trust just because an access request is inside your network is just asking for a breach. By implementing the latest tactics in authentication, network segmentation, encryption, access controls, and continuous monitoring, ZT data security takes the opposite approach.
As enterprises continue to modernize their IT environments, the need for a more advanced and adaptable approach to database authorization becomes increasingly apparent. Traditional models, with their reliance on static roles and broad permissions, are no longer sufficient to meet the demands of decentralized, dynamic infrastructures. StrongDM addresses this gap by offering a solution that emphasizes fine-grained, policy-based action control, enabling organizations to manage database access with
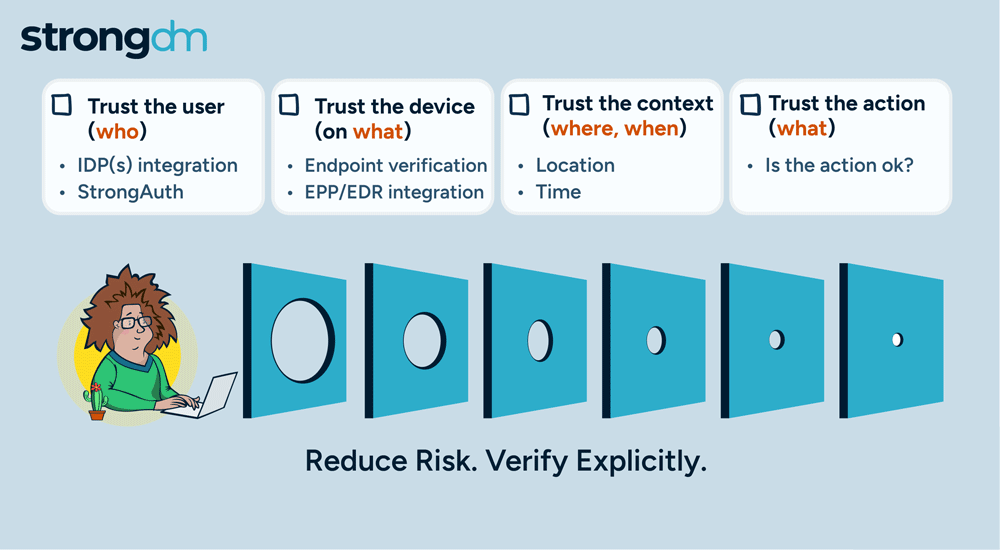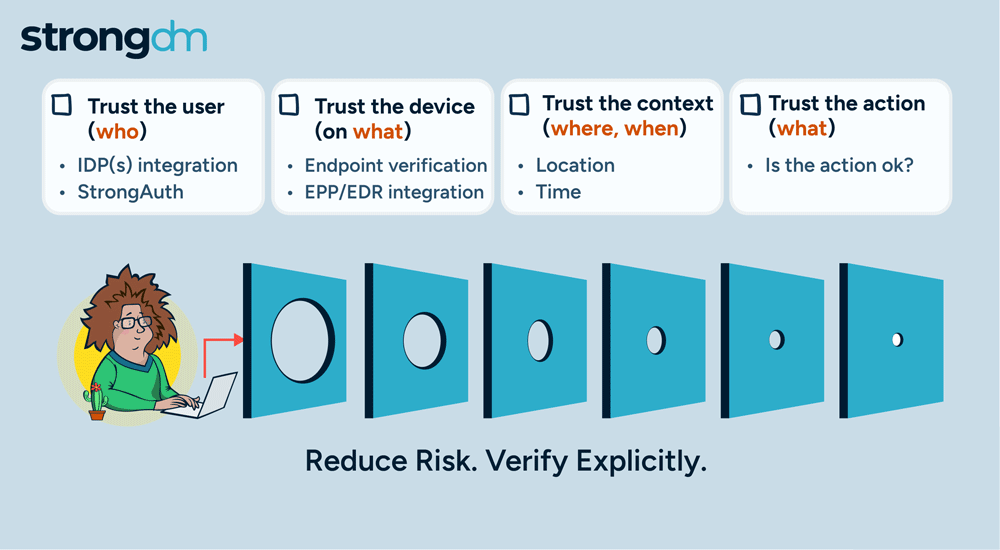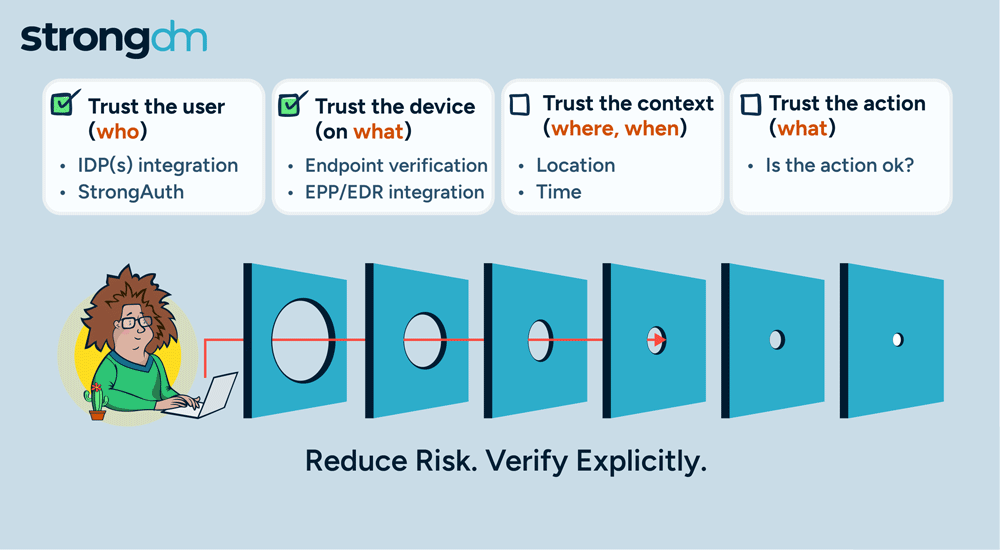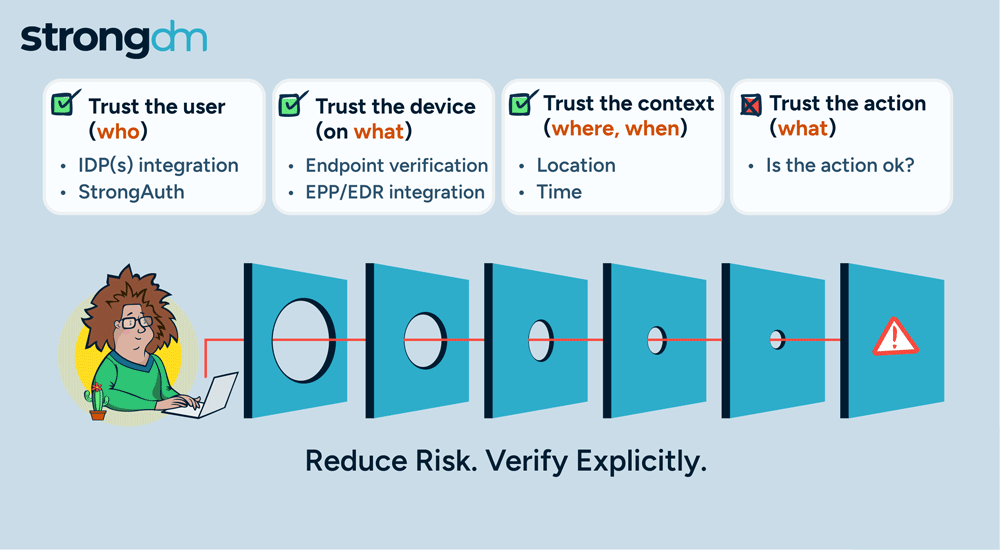
Access is no longer the primary challenge in enterprise security; it's the actions of users that are most aligned with managing risk. By focusing on how actions are authorized, StrongDM is giving customers a more effective approach to enterprise security. Our policy-based action control ensures that, in addition to access, every user action is scrutinized, delivering a higher level of security tailored to meet the complex demands of modern enterprises.
Understanding the core differences between a Zero Trust architecture and a Virtual Private Network (VPN) is an important step in shaping your organization’s cybersecurity strategy. Zero Trust and VPNs offer distinct approaches to security; knowing their functionalities and security philosophies helps you understand when to select one or the other to protect your data effectively—a strategic necessity for robust cybersecurity.

StrongDM is pleased to see that, in April 2024, the National Security Agency of the United States, has released a Cybersecurity Information (CSI) sheet that recommends why and how organizations, public and private, should adopt the Zero Trust (ZT) security model for their data tier of infrastructure. At the core of the recommendations, an organization needs to know what data it possesses, how that data is being accessed, and how to control access to that data.

