Unlocking Zero Trust: The Kipling Method for Policy Writing


Written by
Michaline ToddLast updated on:
October 17, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
In the dynamic world of cybersecurity, fortifying your defenses against evolving threats while maintaining operational agility is paramount. Today, it is no longer adequate to simply authenticate a user based on who they are and what they are trying to access. Bad actors have cracked that simple puzzle.
Instead, we need to consider additional attributes of the access request to assess whether we trust the user to continue on with their work. As such, our access policies need to evolve to meet this need. Enter the Kipling Method—the approach to crafting robust Zero Trust policies as recommended by John Kindervag, the creator of Zero Trust. By asking the quintessential questions of "who, what, where, when, why, and how," organizations can reinforce their security posture and maintain tighter control over their assets and data.
Understanding the Kipling Method
To embark on a successful Zero Trust journey, it's crucial to articulate and implement policies that align seamlessly with your business model. The Kipling Method serves as a guiding light in this endeavor. Let's discuss the six fundamental questions it poses:
1. Who
The first question is at the heart of identity verification in a Zero Trust environment. Who can access your assets? Are they who they claim to be? Identity verification forms the cornerstone of access control, ensuring that only authorized users gain entry.
2. What
What assets is the user trying to access, and what actions are they permitted to take? This question goes to the heart of permissions and privileges. Zero Trust mandates that users only have access to what they need to perform their duties—no more, no less.
3. When
Timing is an important consideration. When does permitted access begin, and when does it end? Are there specific hours during which access is allowed? Defining access windows minimizes the risk of unauthorized access during vulnerable periods.
4. Where
Geographical context is increasingly important in today's globalized digital landscape. Can assets only be accessed from certain locations, and are there forbidden territories? Restricting access based on location bolsters your defense against threats originating from unexpected quarters. Another consideration is where the asset itself resides, as there may be more friction in the process for resources that are part of a regulated environment in order to maintain compliance.
5. Why
Understanding the purpose behind access request is paramount. Why does a user need access to a specific asset? Is access necessitated by regulatory compliance, or is it tied to a specific job function? The 'why' informs the degree of sensitivity and protection an asset requires.
6. How
Lastly, consider the mechanisms through which assets can be accessed. Are there limited ways to interact with the asset? Is access only allowed through a particular VPN? Is device and device posture assessed? Adding additional context about how the user is going to interact with the systems and data into the access risk assessment increases security.
The Kipling Poem Connection
Rudyard Kipling's timeless poem I Keep Six Honest Serving-Men establishes the framework for the Kipling Method.
I keep six honest serving-men
(They taught me all I knew);
Their names are What and Why and When
And How and Where and Who.
This method of Zero Trust policy creation mirrors the essence of Kipling’s poetic wisdom. These six "serving-men" are the gatekeepers of a secure and compliant digital realm, ensuring that access is granted only to those who truly need it, when they need it, and in the manner that aligns with organizational objectives.
These questions serve as a framework for gathering information and understanding a situation comprehensively. While Kipling didn’t first create the concept of who, what, where, when, why and how, he managed to encapsulate them in a concise and memorable way.
Access Management: The Bedrock of Zero Trust
Access management is the bedrock upon which the fortress of Zero Trust is constructed. It dictates who is granted access, to what extent, and under what circumstances. Robust access management forms the foundation of a Zero Trust architecture, ensuring that trust is never implicitly granted but continuously verified.
Implementing Zero Trust in the Real World
While the Kipling Method offers a structured approach to Zero Trust policy writing, the challenge lies in translating theory into practice. This is where solutions like StrongDM come into play.
StrongDM provides Zero Trust Privileged Access Management (PAM) that seamlessly enforces policies derived from the Kipling Method. It ensures access is provisioned, de-provisioned, and monitored in real-time, adhering to the principles of least privilege and just-in-time access. Whether your organization operates legacy on-premises resources or modern cloud-native environments, StrongDM offers comprehensive coverage.
Continuous Trust Assessment with StrongDM
The StrongDM platform was architected from the start to never trust that once an access session starts, it should continue. Once it is determined that an authenticated user and his/her device are authorized to have access, there are continuous signals verifying that the user should still have access. If ever the answer is ‘no’ the session is shut off instantaneously. Over the years, the platform has matured to support additional measures of trust.
User Trust & Device Trust
When considering if the user is to be trusted, StrongDM takes into account several factors for every request.
- Can we trust who the user is? Have they authenticated properly?
- What are they trying to access? Is it something they should have access to?
- Where is the resource located? If it is in a regulated environment, should they have access to it?
- If it was a Just-in-Time access request, are they still within the window of time when access is allowed?
- Can we trust how the asset is being accessed? Is the device to be trusted?
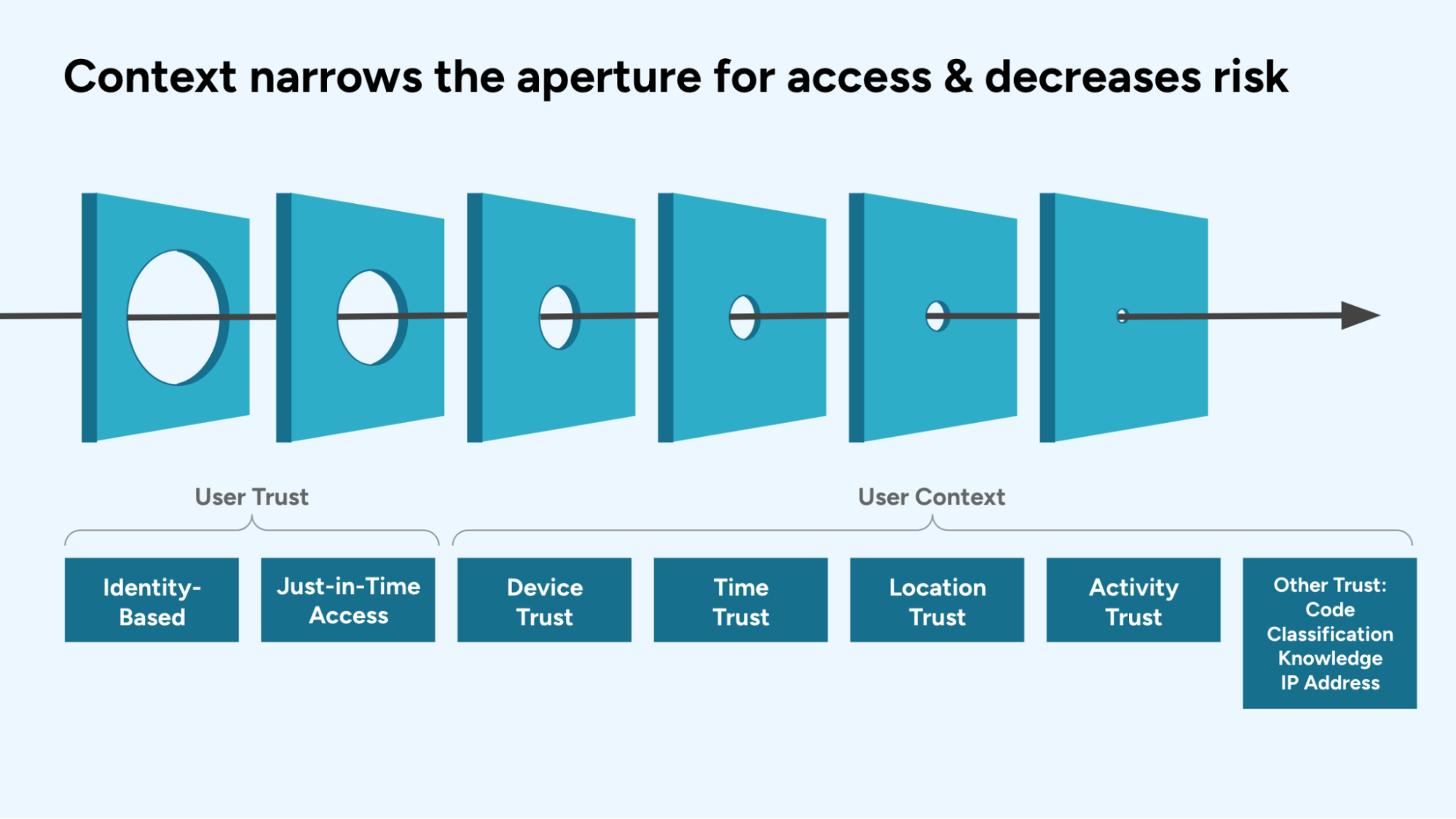
Additional Context for Determining User Trust
For more sensitive systems – like production environments or regulated data stores – it is recommended that additional access policies are added that consider the context of the access request and activity. Some examples of contextual trust assessments include:
- Device Trust - What type of device is the person using? When was the last time it was updated or scanned?
- Knowledge Trust - How has the person been trained? Have they completed the courses in the LMS necessary to access this system?
- Classification Trust - What level of security clearance does the person have? Is it the right level necessary for the system and data?
- Time Trust - Is the session being requested at a time when you’d expect the user to be working? Are they logging in at 3am their time, which is a first?
- Location Trust - Is the session being originated from where we’d expect? Iif their session an hour ago came from their hometown of Chicago, why is this session coming from Copenhagen?
- IP Trust - What is the user’s IP address and is it trustworthy?
- Activity Trust - What are the actions they are performing and should they be allowed?
- Code Trust - Is the software running validated code?
Another way to think about contextual access assessment
If privileged access management is like a security guard in an office building giving someone access to the 12th floor; then, dynamic access management would be like having the security guard by your side the entire visit making sure you didn’t go into an office you shouldn’t, talk to someone you shouldn’t, or write something on the white boards that was inappropriate.
In conclusion, the Kipling Method provides a robust framework for crafting Zero Trust policies that empower your organization to withstand evolving threats while maintaining operational agility. By partnering with StrongDM, you can translate these policies into reality, securing your digital assets with confidence. Make the shift towards a more secure, efficient, and agile future with StrongDM today, underpinned by the foundational strength of access management in the realm of Zero Trust.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Michaline Todd, Marketing Expert, is a distinguished marketing leader with a track record spanning over two decades in the software industry. With tenure of over 10 years as a Chief Marketing Officer, she has left an indelible mark on companies such as Oracle, Veritas, MarkLogic, Evident.io, Palo Alto Networks, and StrongDM. Michaline's expertise lies at the intersection of technology and marketing, driving strategic initiatives that fuel business growth and innovation.
You May Also Like




