Authorization isn’t just about who gets in, it’s about what they can do once they’re inside. And that’s where most breaches happen. Whether you're enforcing RBAC, ABAC, or context-based policies, effective authorization ensures users only access what they need, no more, no less. This post unpacks how authorization works, compares key models, and explores best practices for enforcing least privilege at scale.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

Workforce identity and access management (IAM) secures your internal users, employees, contractors, and engineers by verifying who they are, controlling what they can do, and monitoring how they interact with sensitive systems. It’s the foundation of Zero Trust in a cloud-first world. This guide breaks down everything from SSO and MFA to RBAC, JIT access, and directory services, and how they all work together to keep your workforce productive and protected.
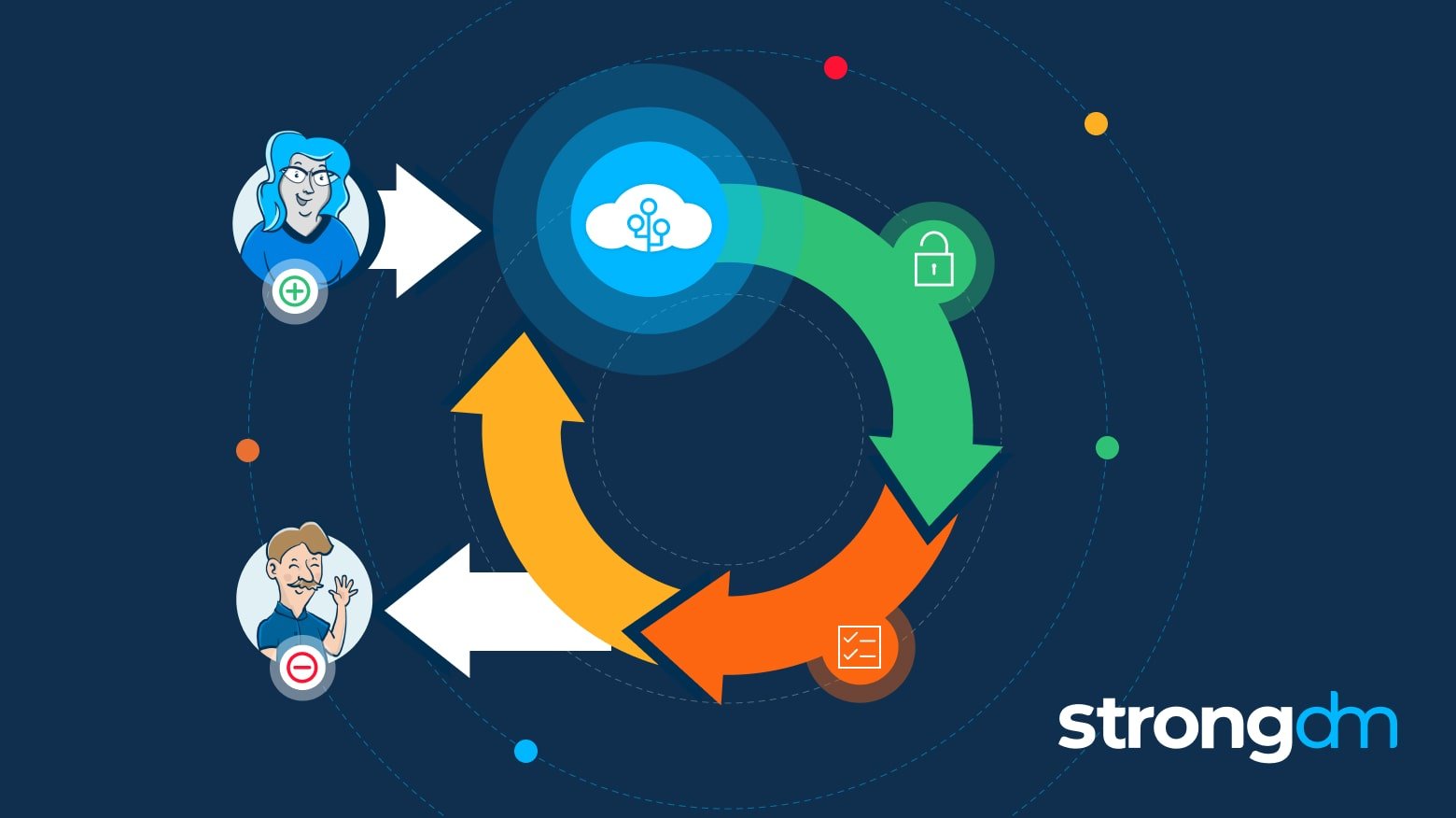
User provisioning is the process of managing user access within an enterprise. It involves creating, managing, and deprovisioning user accounts and access rights across various systems and applications. This includes setting up accounts, assigning roles and permissions, and managing identities.

Unauthorized access—the unauthorized entry or use of an organization's systems, networks, or data by individuals without permission—is a common way for bad actors to exfiltrate data, inject malicious code, and take advantage of all types of breaches, and can have severe consequences for an enterprise and its customers.

Identity and access management (IAM) is a collection of technologies, policies, and procedures designed to guarantee that only authorized individuals or machines can access the appropriate assets at the appropriate times. While it is an effective approach to enterprise security, IAM implementations are complex undertakings. If not done correctly, it can create security gaps that leave your organization at increased risk of a breach. Taking a measured approach will ensure your deployment is
Historically, finding an infrastructure access management solution that is secure while still being easy to use has been extremely difficult. Too often, ease of use and complexity end up at odds. StrongDM addresses this challenge–and does so by integrating with your existing identity-based security initiatives. This blog details how StrongDM enables organizations to level up their access management approach to meet the requirements of Dynamic Access Management (DAM), bolster security, and
This article is your map for taking the work you’ve done with identity and your identity provider (IdP) and using it as your launchpad for access management. Shifting from identity-based access to a more dynamic access approach is necessary for organizations looking to modernize their access management and better protect sensitive resources at scale and in the cloud.

When it comes to cloud security, AWS follows the Shared Responsibility Model. They secure the underlying infrastructure while you protect your data, applications, and systems—including the identities that access them. Integrating AWS with a dynamic access management tool like StrongDM is key to securing identities in the cloud. StrongDM centralizes access control, while AWS offers robust security measures, contributing to a solid defense against unauthorized access.
In this article, we will define SCIM and cover the basics of SCIM security. You’ll learn what SCIM stands for, how SCIM provisioning works, and why SCIM SSO is essential. By the end of this article, you will have a clear understanding of what SCIM means and how auto-provisioning via SCIM streamlines cloud identity management, increases employee productivity, and reduces IT costs.

In this article, we’ll compare the top IAM solutions: StrongDM, CyberArk Identity, Okta, BeyondTrust, ManageEngine AD360, Saviynt, and Twingate. We’ll explore what business needs identity and access management solutions address, and review the pros and cons of each. By the end of this article, you’ll know how to choose the right IAM solution for your organization.

Cloud data protection is an increasingly popular element in an organization’s security strategy. In this article, we’ll explore what cloud data protection is, why it’s important, and the best practices to follow when migrating to the cloud. By the end of this article, you’ll understand the benefits and challenges of adopting a data security strategy for cloud environments.

In this article, we’ll define centralized identity management and explain the difference between centralized and decentralized identity management models. We’ll explore what centralized access control is, how it works, and how centralized access management handles provisioning, authentication, and authorization. By the end of the article, you’ll know how to choose between centralized account management and decentralized models to prevent cybercrime and streamline provisioning workflows.

In this article, we’ll explain the concept of automated provisioning and how it's used in identity and access management. You'll learn about the importance of automated provisioning in an organization's IT management and its benefits to businesses and system administrators. By the end of this article, you'll have a deep understanding of automated provisioning and how it works.
Enterprises often have thousands of users to manage, and therefore unique requirements for their enterprise identity and access management software solutions. In this article, you’ll learn what enterprise IAM is and what to expect in a successful enterprise-wide IAM software implementation. By the end of this article, you’ll know the benefits and challenges of introducing enterprise IAM solutions in your organization.