Passwords alone don’t stop breaches anymore. Context-aware authentication changes the game by using real-time signals like device, location, time, and behavior to decide whether access should be granted.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
Single sign-on (SSO) gives users one login to access everything. SAML is one of the key protocols that makes that possible—passing identity data securely between identity providers and service providers. But while all SAML implementations are part of SSO, not all SSO solutions rely on SAML. Understanding how SAML fits into your authentication stack helps you choose the right tools for modern access control. This guide breaks down how SAML works, how it powers SSO, and how you can manage
The HIPAA Multi-Factor Authentication (MFA) requirement is a security measure that requires users to verify their identity using at least two different factors—such as something they know (a password), something they have (a smartphone or token), or something they are (a fingerprint)—to access systems containing electronic Protected Health Information (ePHI). This additional layer of security is designed to protect sensitive healthcare data from unauthorized access, even if one credential is

Network Level Authentication (NLA) is a security feature of Microsoft’s Remote Desktop Protocol (RDP) that requires users to authenticate before establishing a remote session. By enforcing this pre-authentication step, NLA reduces the risk of unauthorized access, conserves server resources, and protects against attacks like credential interception and denial of service. While effective in securing RDP sessions, NLA is limited to a single protocol, lacks flexibility, and can add complexity in
With so many advanced cyber attackers lurking on the threat landscape, a simple password is no longer enough to safeguard your sensitive data. There are many reasons to adopt MFA for your business. It supplements your security by requiring additional information from users upon their access requests—and it significantly reduces your risk of incurring a breach. Several multi-factor authentication methods are available, with varying strengths and weaknesses. Be sure to compare the differences
As enterprises continue to modernize their IT environments, the need for a more advanced and adaptable approach to database authorization becomes increasingly apparent. Traditional models, with their reliance on static roles and broad permissions, are no longer sufficient to meet the demands of decentralized, dynamic infrastructures. StrongDM addresses this gap by offering a solution that emphasizes fine-grained, policy-based action control, enabling organizations to manage database access with
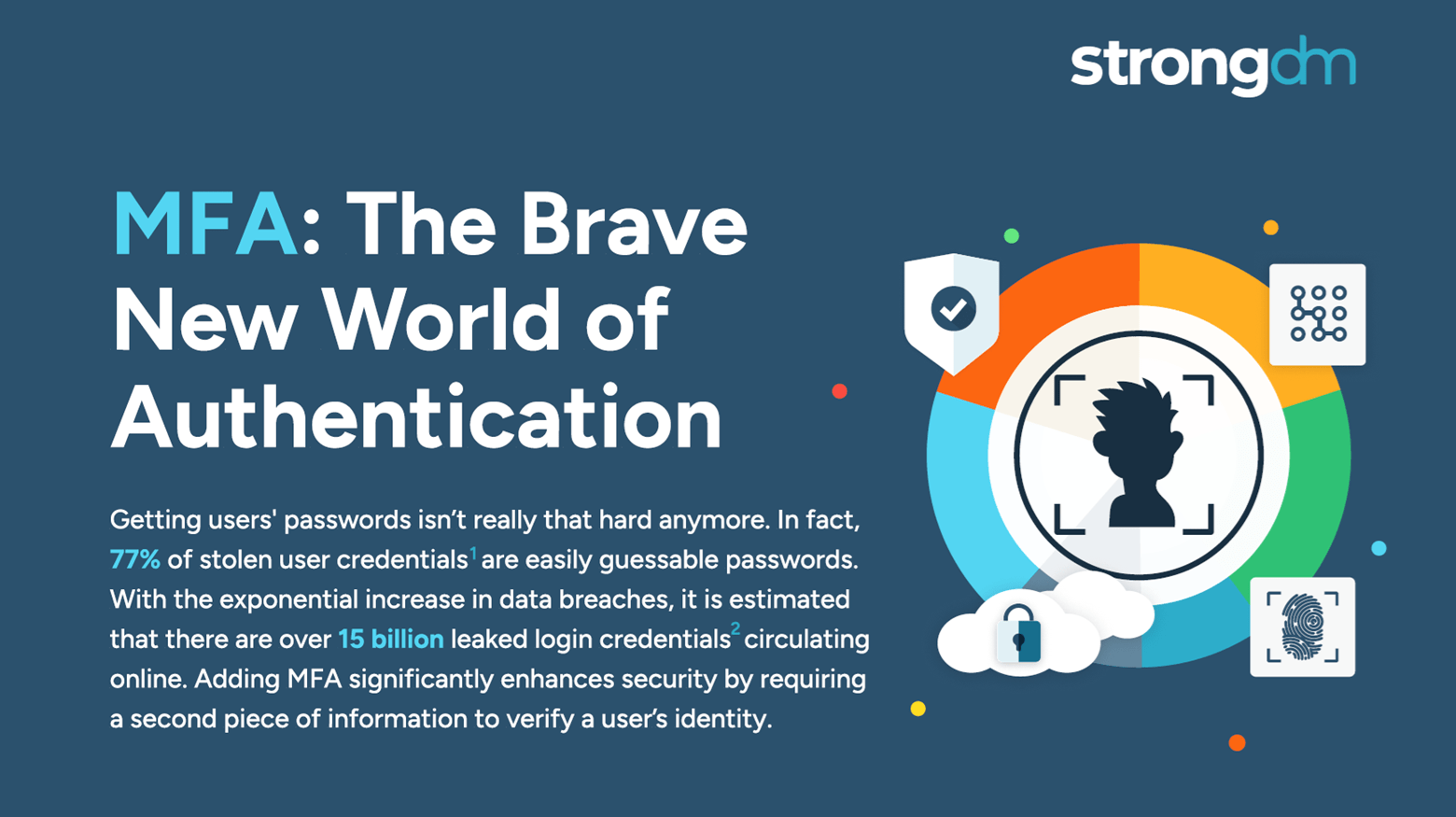
Get ready to secure everything and anything with MFA. Easily combine security checks such as device trust and geo-location. With StrongDM you can MFA all resources (e.g., multiple clouds, diverse databases, or critical applications, etc.) without changing your applications’ code or infrastructure.

This article investigates MFA fatigue attacks. We'll explain how they work, why they're effective, and who they typically target. We'll also provide real-life examples to help your team detect and prevent these threats. You'll leave with a clear understanding of MFA fatigue attacks and tips on how to shore up your cloud security to defend against them.

Recently, cloud computing company Snowflake issued a warning to its customers: hackers are actively targeting accounts that lack Multi-Factor Authentication (MFA). This warning comes amidst a rapidly unfolding saga that includes the high-profile Ticketmaster breach.

The world we operate in today is far different than it was even a couple years ago. More employees work from remote locations (as of late 2023, more than 12% of U.S. workers are fully remote), and more companies engage the services of freelancers and other outside workers. Organizations must recognize that the traditional physical boundaries no longer apply. They now need to secure a vast array of devices used by employees spread across various locations.

Getting users' passwords isn’t really that hard anymore. In fact, bad actors employ advanced technology that allows them to snowshoe (test billions of password combinations per second), rendering 90% of user-generated passwords susceptible to attacks. MFA significantly enhances security by requiring a second piece of information to verify a user’s identity. The additional 20 seconds a user spends receiving a code via SMS provides a level of protection that a password alone cannot offer.

User authentication plays an essential role in securing networks and ensuring that only authorized users can access sensitive data. As our infrastructure transitions from traditional on-premises setups to cloud and hybrid environments, our authentication methods must continue evolving.
The way that people work continues to evolve, and as a result, so do the ways that they must authenticate into their organization’s resources and systems. Where once you simply had to be hardwired into the local office network, now you must expand your perimeter to include remote and hybrid workforces, on-prem and cloud environments, and take into account a growing list of factors that impact how and where people access critical company resources.
![How to Prevent Credential Stuffing [9 Best Practices]](https://discover.strongdm.com/hubfs/credential-stuffing-prevention.png)
