Audit logging is essential for maintaining a secure and compliant IT infrastructure. By capturing detailed records of system activities, audit logs provide insights into user actions, system events, and potential security threats. Understanding audit logging helps you identify and address vulnerabilities, ensure regulatory compliance, and enhance overall system integrity.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
A cybersecurity audit is a comprehensive assessment of your organization's information systems, networks, and processes that identify vulnerabilities and weaknesses that cybercriminals could exploit. The audit also evaluates the effectiveness of your security controls, policies, and procedures and determines if they align with industry best practices and compliance standards.

Want a secure and compliant AWS environment? Then you need to audit access. Keeping tabs on who has accessed what—as well as the whens, wheres, and whys—helps you spot suspicious activities and address them promptly. Without this kind of access control, your sensitive data could be exposed to malicious actors, putting you at risk of data breaches and subsequent regulatory nightmares or service interruptions.

Two of the most important questions in security are: who accessed what, and when did they access it? If you have any Linux or Unix machines, you’ll likely find answers in the sshd log. sshd is the Secure Shell Daemon, which allows remote access to the system. In this article, we’ll look at how to view ssh logs.
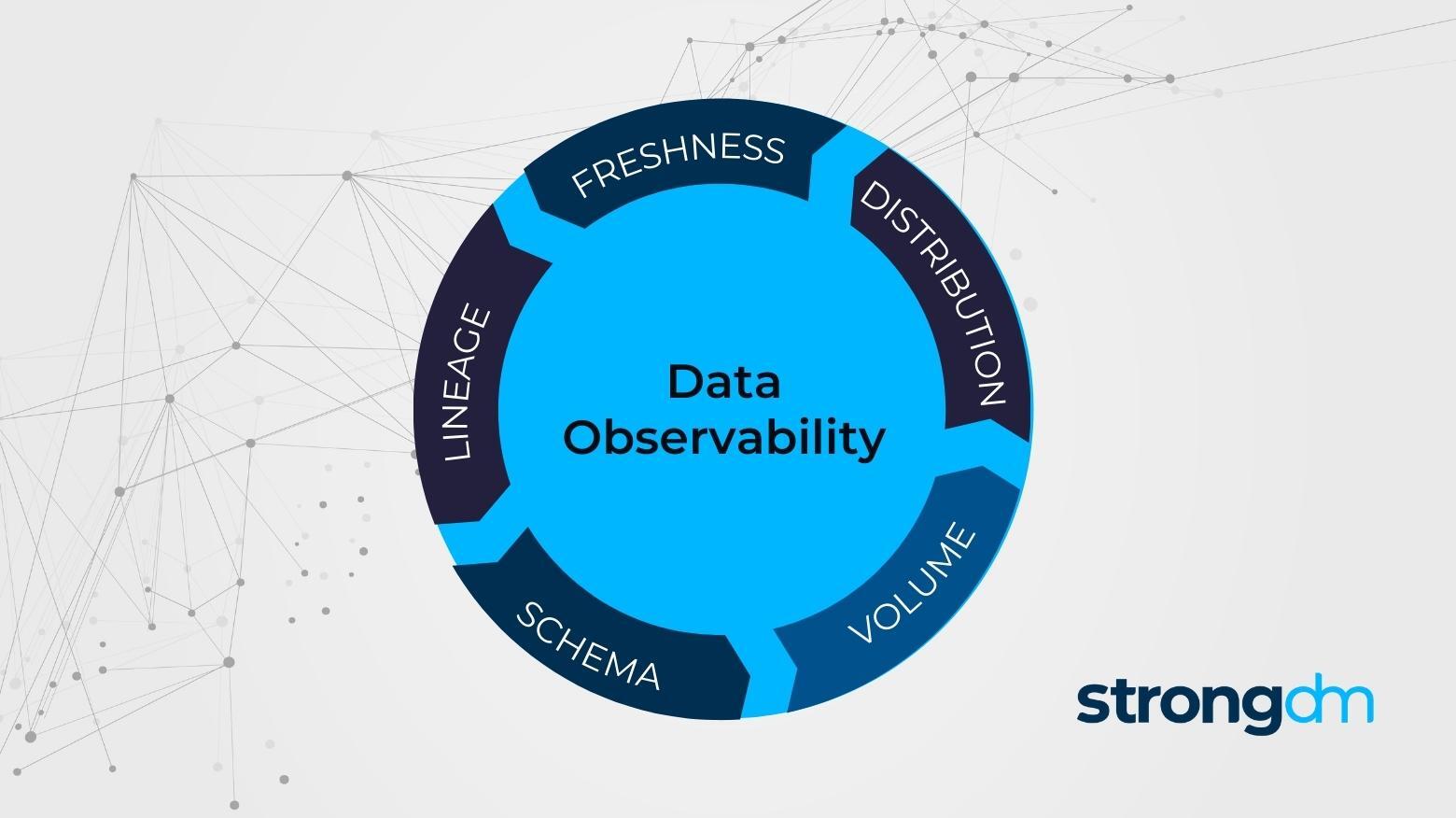
Data observability can help companies understand, monitor, and manage their data across the full tech stack. In this article, you’ll learn what data observability is, the differences between data observability, monitoring, and data quality, and what information you can track with data observability. By the end of this article, you’ll discover how to implement data observability and find the right data observability tools for your organization.

In this article, we’ll focus on the three pillars of observability. You’ll learn about the definitions, strengths, and limitations of each pillar. By the end of this article, you’ll know about their individual contributions and typical real-world challenges, tying them together for an overall view of your system.
Observability and monitoring are often used interchangeably, but there are key differences you should know between these two IT terms and the tools that enable them. In this article, we’ll explore the relationship and differences between observability vs. monitoring. Plus, you’ll learn about what makes observability and monitoring different from telemetry and application performance monitoring (APM).

We recently completed our own SOC 2 audit, so we thought we’d review how we dogfooded our own product. We’ll share tips and tricks to make the audit process a little easier, whether you’re wrapping up your own or about to dive into the coming year’s audit. Here are the questions auditors asked us during our own SOC 2 audit and the commands and strongDM tooling we used to gather the evidence they requested.
During a featured session at this year’s DevOps Experience, Olive AI CloudOps Engineer Kellen Anker spoke with Justin McCarthy, strongDM CTO & Co-founder, about his company’s journey towards achieving one-click onboarding access and the resulting radical improvements in workforce efficiencies.

Offboarding technical employees can be a complex and arduous process with a lot of moving parts. The key to successful offboarding is to have a clear understanding of what needs to be done, who does it, and how to monitor for any shenanigans from former employees.
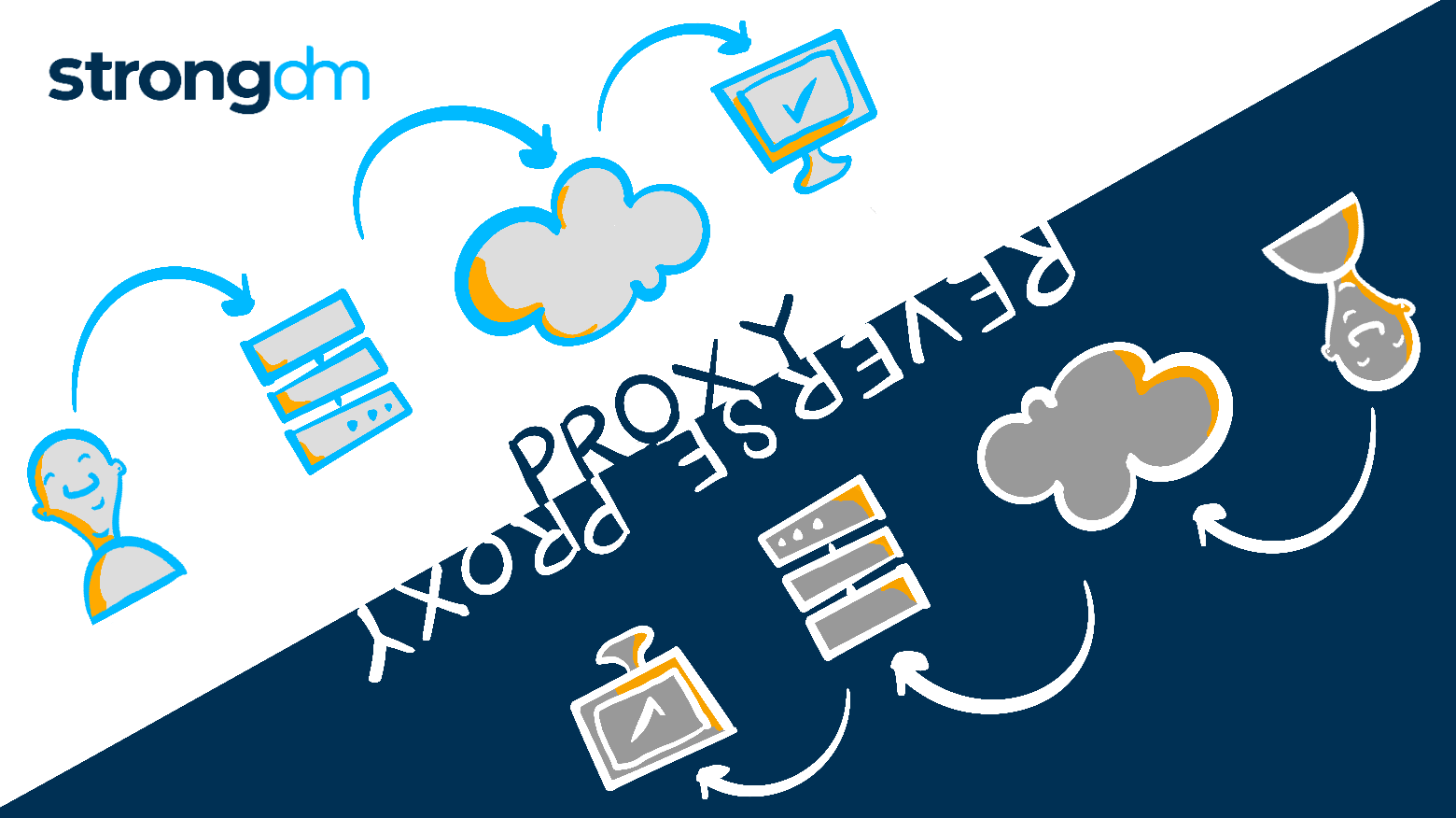
In this post, we’ll dissect the two concepts and explain how administrators can use a reverse proxy for easy access management control.

Consider this when you choose to integrate Active Directory (AD) with your databases and applications using their native APIs, connectors, or toolkits.

SSH audit logs allow you to determine, either retroactively or in real-time, when an unauthorized or destructive action was taken, and by whom.

As your organization pursues your SOC 2 certification, organization is critical. You will be busy actively managing dozens of ongoing daily tasks, which can bury you in minutiae. But at the same time, you need to keep your high-level compliance goals in focus in order to successfully move your certification over the finish line.