

Written by
Dominic GarciaLast updated on:
September 21, 2023Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Standing Credentials. They’re a problem that seems to persist despite the latest security and access innovations. They’re also one of the main reasons that achieving zero trust is so hard–and enough of a problem that two strategic security initiatives have come to the forefront: Just-in-Time (JIT) access and Zero Standing Privileges (ZSP).
The risk presented by standing credentials is very straightforward: always-on credentials equals always-on risk. It can be ransomware, credential stuffing, insider threats, or any other attack that uses credentials to gain access to your organization. That’s why eliminating standing privileges is critical to eliminating your surface of attack. Fewer credentials that exist in perpetuity are fewer opportunities for bad actors to gain access to your organization.
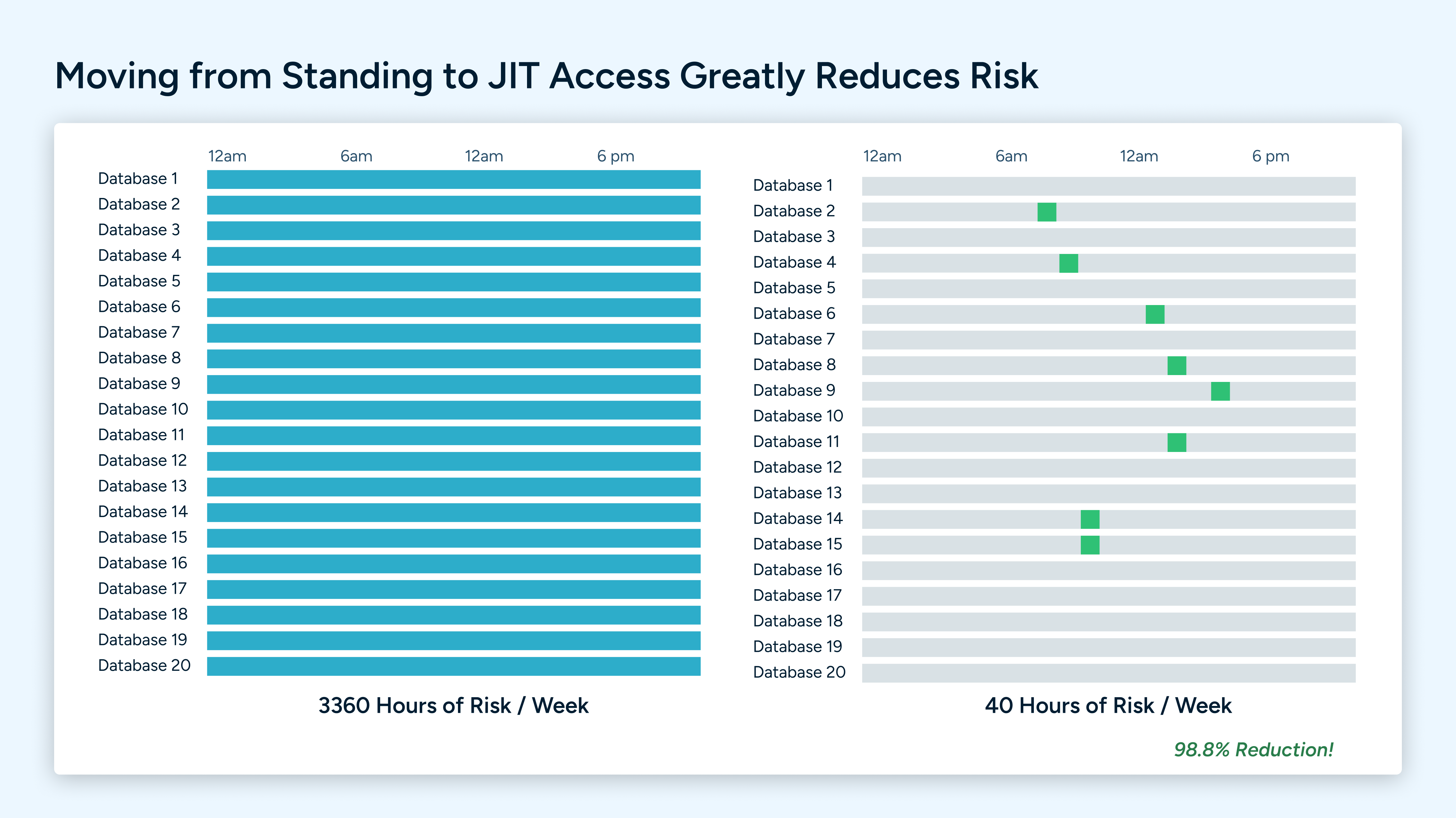
In fact, a StrongDM study showed that, on average, 85% of credentials had not been used in the last 90 days. And all of those credentials represent an attack vector for bad actors–that's a risk that you don’t need to take on, much less maintain perpetually.
Unfortunately, achieving Zero Standing Privileges (ZSP) has significant challenges. These include:
- Lack of simplicity for end-users to request access and have it provisioned
- The inability for admins to easily track and manage new and existing permissions
- Admins are unable to easily de-provision access across multiple tools and environments at scale
While the three points above may seem simple, that impact is significant.
- Users get over-provisioned due to the complexity and overhead of provisioning systems
- Over-provisioned access becomes over-provisioned standing access, increasing your attack surface
- The complexity of audits and investigations is increased
The leading blocker for reducing this risk is simple: there’s no easy way to grant just-in-time access at scale across your organization. The overhead incurred from access requests and the delays in productivity from dev teams makes it prohibitively expensive and time-consuming to address this problem manually. That’s why we built StrongDM Access Workflows.
StrongDM Access Workflows
StrongDM Access Workflows ensures that your team can get access to the tools they need when they need it and also makes it possible to remove that access just as quickly. This approach eliminates standing credentials by streamlining access requests that meet security policies. StrongDM Access Workflows delivers:
- Enhanced Security: Access is only granted for a specified duration eliminating the need for standing access and reducing the overall attack surface.
- Improved Efficiency: Easier to manage user rights with JIT access; no need to keep track of who has standing permissions.
- Reduced Insider Threats: No more persistent access to sensitive data. With JIT, the potential damage an insider can cause is confined to a narrow access window.
Furthermore, StrongDM Access Workflows significantly improve the end-user experience. End-users have an individualized Access Catalog to resources available based on their role or resource attributes (i.e., environment tags, geo-location, etc.). Users request access and connect based on human or automated approval. Here’s an example of a workflow in StrongDM:
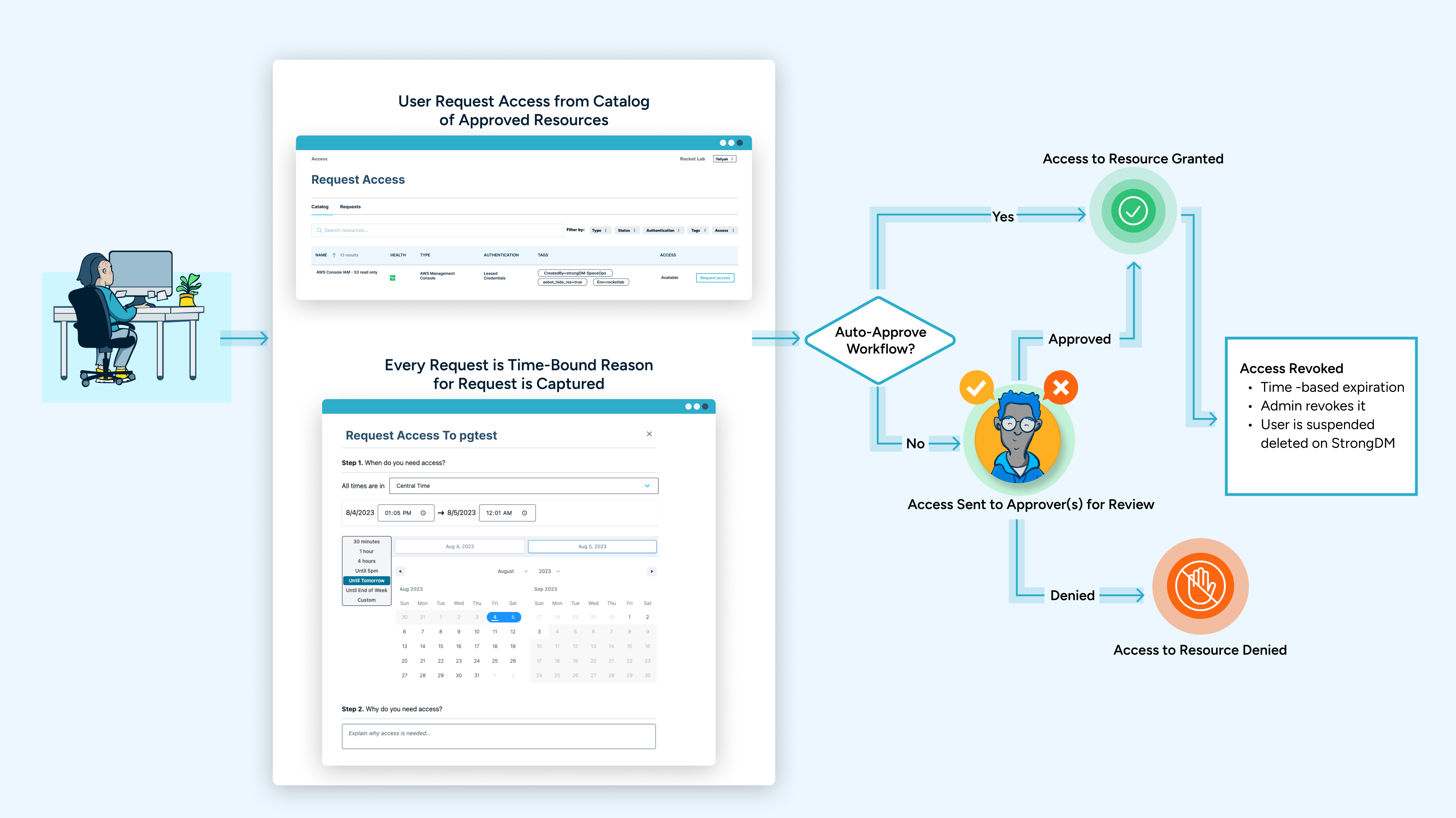
By implementing workflows that streamline access requests, grants, and revocation, you can ensure that access only exists when it’s needed and automatically expires. The result is the inability of bad actors to use standing credentials (because they’ve been eliminated), and your overall threat surface has also been reduced.
Access requests can also be made via common tools in your stack or via ChatOps and service desks. For example, StrongDM Access Workflows for Slack enables your team to request and approve workflows through direct integration with Slack, limiting context switching and helping your team to continue to use everyday tools while securing access. Check out the video below as an example:
Trying to reach Zero Standing Privileges? We can help.
When standing access is reduced, your attack surface is as well. StrongDM was designed to help you achieve true Just-in-Time access and reach Zero Standing Privileges while making your end-users life easier. Implement Just-in-Time access across all your resources on-premises and in the cloud and meet your security policies. StrongDM’s Access Workflows improve the management of access requests at scale while maintaining the highest security standard. To see StrongDM in action, sign up for a demo here.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Dominic Garcia, Technical Marketing Expert, has held marketing leadership roles for Silicon Valley technology companies specializing in database, data management, and data analytics solutions. As head of content marketing at Splunk, Dominic contributed to boosting the company’s market visibility and its growth from a $100M to a $1.3B company. He brings relentless creativity to the task of connecting people with technical products to improve their lives. Dominic holds a B.S. degree in Public Relations from the University of Texas at Austin. To contact Dominic, visit him on LinkedIn.
You May Also Like




