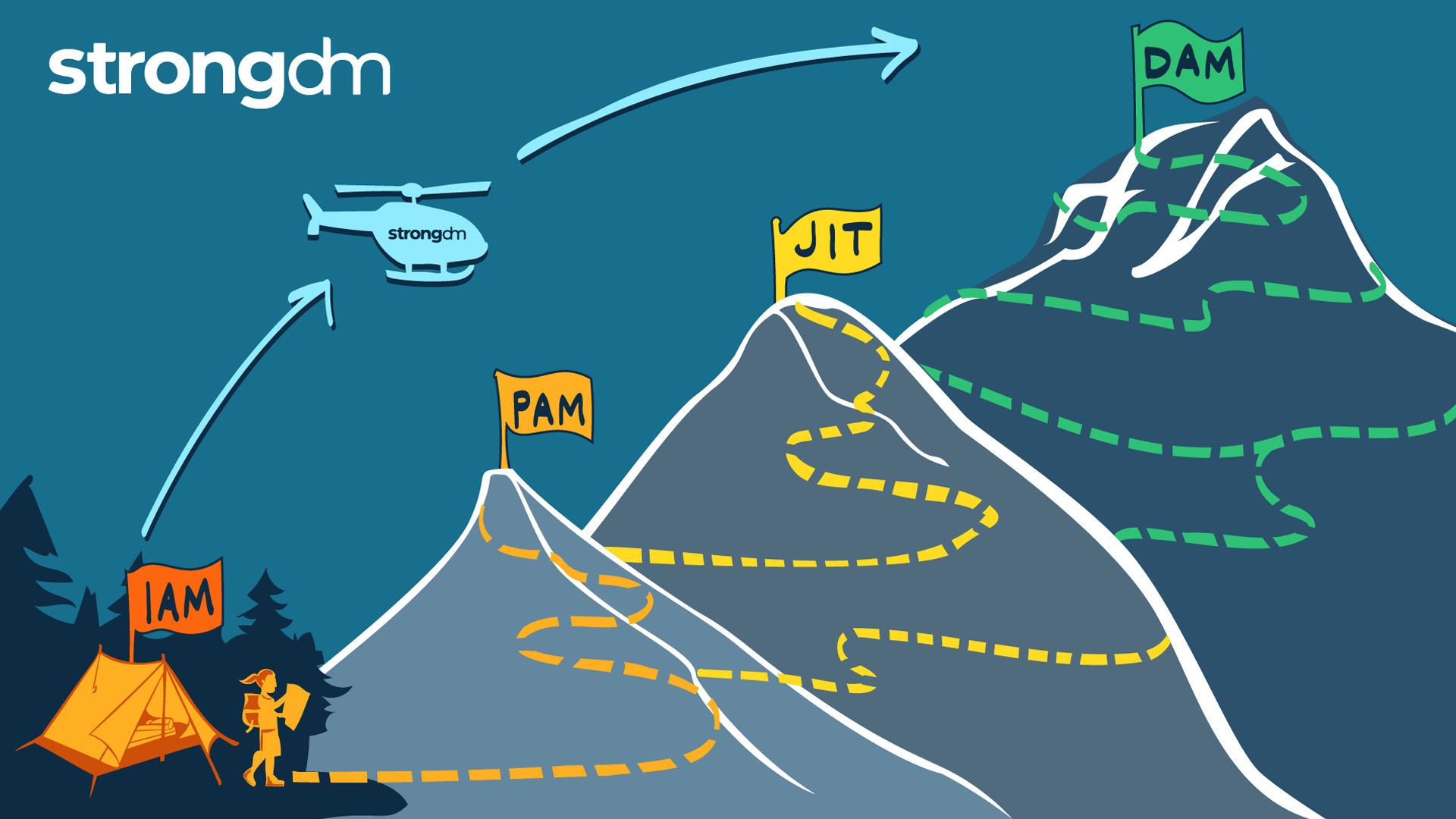
Spring has sprung and the audits will come. How efficient are you at audit preparation? At StrongDM we reduce the administrative load and help customers get answers to the questions they need to reach regulatory compliance for internal and external audits.