Written by
John MartinezLast updated on:
September 11, 2024Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
If you’re Kuberntes admin and you’re not familiar with the tactics outlined in the MITRE ATT&CK framework, this blog post is for you. MITRE ATT&CK framework is an extensive knowledge base of tactics and techniques employed by bad actors that defensive security experts use to help defend their organizations against attack, and many times, used by their offensive security counterparts to test their weaknesses.
Like any other complex system, Kubernetes is not immune from attacks and should be protected.
How Can a Kubernetes Admin Leverage MITRE ATT&CK Framework Containers Matrix?
Unlike a security best practices framework that sets out to give you guidelines for how to architect your systems or systematically configure settings in a prescriptive way for optimal security hygiene, MITRE puts you in the mind of the attacker. Specifically, how they’ll attack your Kubernetes clusters and underlying containers, otherwise known as tactics and techniques. That’s why they’ve mapped these tactics into the Containers Matrix.
The Containers Matrix outlines tactics along 9 areas, with many of the techniques overlapping between the tactics, because they’re relevant for more than one tactic. In other words, it’s a matrix as opposed to a checklist.
The 9 tactics of Containers Matrix
1. Initial Access
Techniques for gaining an initial foothold in your environment
2. Execution
Techniques for running malicious code on a compromised system
3. Persistence
Techniques for maintaining access on compromised systems
4. Privilege Escalation
Techniques for elevating privileges of compromised identities
5. Defense Evasion
Techniques used to avoid detection
6. Credential Access
Techniques used to steal credentials
7. Discovery
Techniques for gaining knowledge about your environment
8. Lateral Movement
Techniques used to enter and expand control of your environment
9. Impact
Techniques used to disrupt the availability and integrity of your environment
What I like most about the tactics is the way they set the tone, and how I describe it above: think like an attacker. Privilege Escalation, for example:
The adversary is trying to gain higher-level permissions.
Privilege Escalation consists of techniques that adversaries use to gain higher-level permissions on a system or network. Adversaries can often enter and explore a network with unprivileged access but require elevated permissions to follow through on their objectives. Common approaches are to take advantage of system weaknesses, misconfigurations, and vulnerabilities. Examples of elevated access include:
- SYSTEM/root level
- local administrator
- user account with admin-like access
- user accounts with access to specific system or perform specific function
These techniques often overlap with Persistence techniques, as OS features that let an adversary persist can execute in an elevated context.
They then get into the details of the techniques used to escalate privilege on your clusters and containers. These techniques are very detailed and reveal the common ways an attacker will test your security and try to find the hole that allows them to gain access.
Once you read the matrix and test these on your own environment, you can use your new-found knowledge to validate the security posture of your environment, and stay one or many steps ahead of a would-be attacker.
Of course, the techniques used to find vulnerabilities and compromise your systems grows every day. That’s why it’s better to not be lax on security, and be proactive, even if it’s not part of your “day job” as a Kubernetes admin in a DevOps/SRE/Platform/Cloud engineering role.
How Can StrongDM Help You Be Proactive About Kubernetes Security?
It’s all about taking a proactive and preventative defense posture. Why not thwart the attack before it even happens? In today’s world of blurred network perimeters, it’s hard to keep up with where exactly your infrastructure is, and the traditional world of network firewall defenses are less effective against identity and access attacks. Microsegmentation goes a long way to reduce the attack surface, but you also need a robust IAM proactive defense strategy.
Learn more about Kubernetes security best practices.
StrongDM's direct support for Kubernetes clusters and Zero Trust PAM platform capabilities maps to strong defenses against the techniques used by attackers:
Just-In-Time and Dynamic Access
We take the stance that access should only be given to a user for the period of time that they need access to a specific resource. For this reason, we give you the ability to provide access to specific resources only when it’s needed, and allow you to map requests into dynamic workflows using our in-built role mappings and resource tagging. This helps eliminate issues with persistence and privilege escalation attacks.
Zero Standing Access or Privileges
We recommend that at no point should access to resources be permanent. It’s not enough that you’ve implemented “least privilege” and only give access to the minimal number of resources, coupled with Justin-in-Time access above, you have to restrict the time and duration, and should challenge when a user requests privileged access to a resource. This will help you with initial access, persistence and privilege escalation attacks.
No exposed credentials
One of the favorite things attackers love to do is obtain valid user credentials as covered in credential access techniques. At no point in time does StrongDM expose any credentials to users. Period. We employ a network of customer-deployed and protocol-aware relay systems that handle fully encrypted and secure client connections from their users to their target infrastructure, including Kubernetes clusters. These relays also handle credentials exchange from your vault of choice: use our built-in credentials vault, or bring your own. This has the side benefit of simplifying access for end-users: no need to remember or store passwords and continue using the dev tools you already know and love.
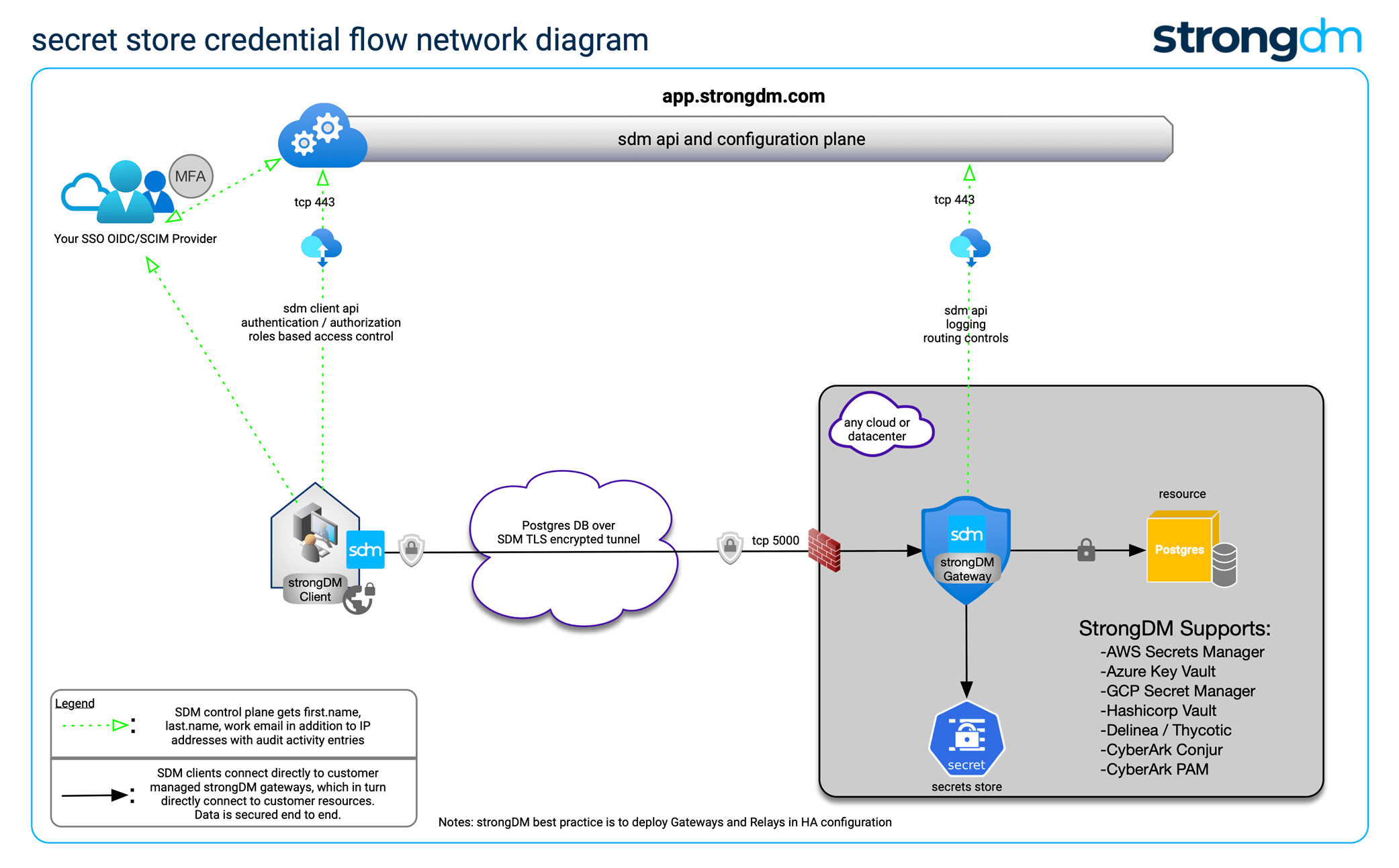
Fully observable audit data
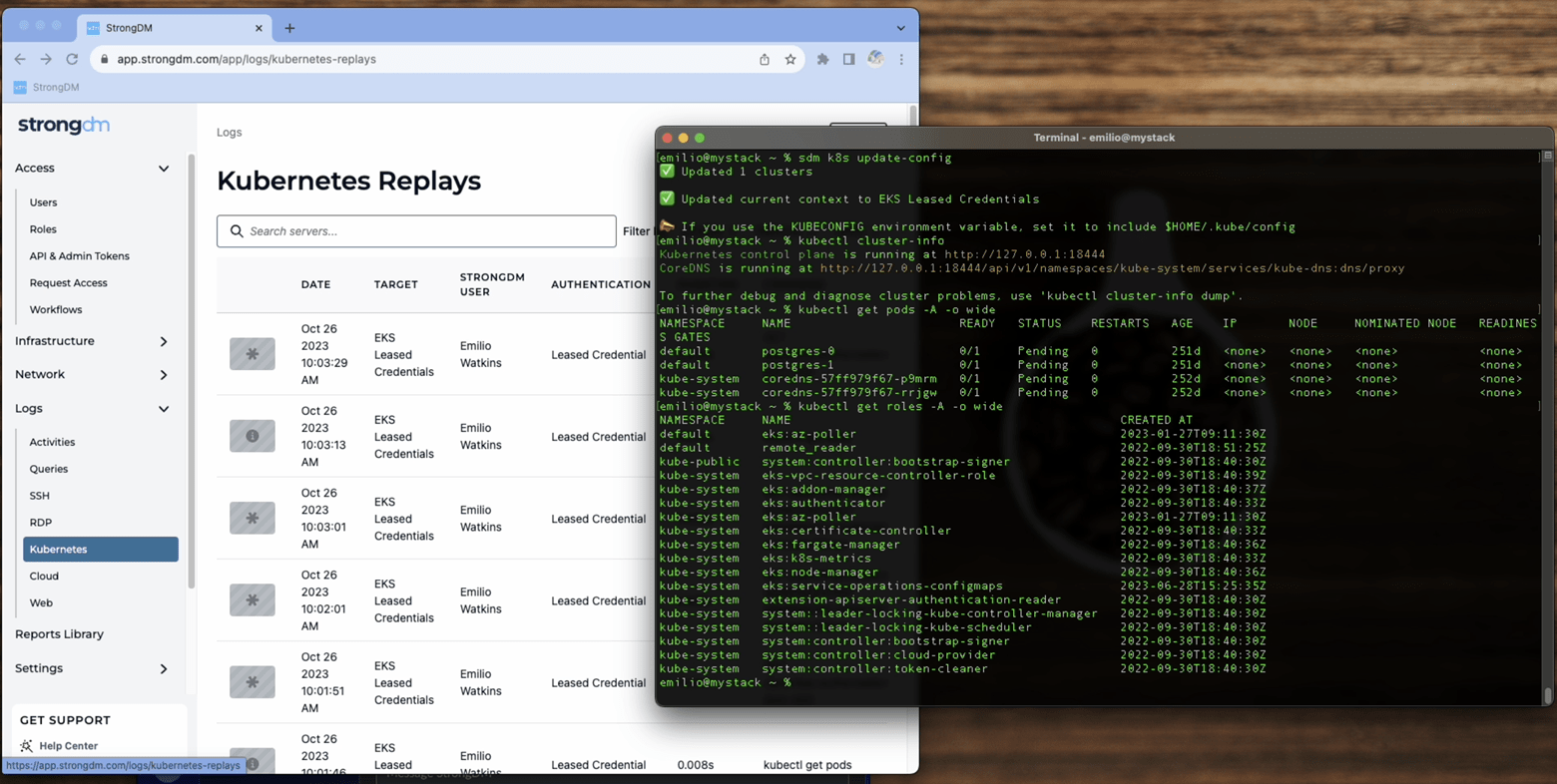
Attackers almost always try and cover their tracks: this is called defense evasion. Or worse, obfuscate logs to further confuse you and look somewhere else, anywhere, so you don’t see where they are or what they’re doing in your environment. We have full audit capabilities of Kubernetes API calls and kubectl commands, SSH session replays, database queries and many others so that you can audit and review activity happening in your environment in real-time.
StrongDM Enhances Your Kubernetes Security Using MITRE ATT&CK Containers Matrix
The MITRE ATT&CK Containers Matrix will become one of your favorite resources that you refer to for your proactive and preventative defense posture strategy, and StrongDM is critical to cover much of that strategy for identity attack and privilege escalation techniques.
For much more detailed mappings of what Containers Matrix techniques we cover, refer to our MITRE ATT&CK Containers Matrix Solution Guide.
Support of Kubernetes is just one component that makes up our Zero Trust PAM platform. Knowing that Kubernetes hosts and is adjacent to a myriad of applications and services critical to your business, we also support resources such as databases and cloud accounts, legacy as well as cloud-native applications, and we centralize access to every one of those resources.
Want to see StrongDM in action? Book a demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like