This guide lays out a clear framework for evaluating database security tools, focusing on the risks they mitigate, the controls they deliver, and the outcomes they enable. From access and auditing to encryption, posture management, and recovery, we’ll highlight the best solutions and how they fit together
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

This guide breaks down the top cloud database solutions reshaping how organizations store, manage, and scale data. From relational databases to NoSQL options, we’ll cover what matters most when choosing the right solution for your needs. By the end, you’ll understand how modern cloud databases drive scalability and performance—and which one is the best fit for your organization.

By simplifying the ability to enforce granular policies, Cedar has set a new benchmark for access control in Kubernetes, and we’re thrilled to be part of this journey. This evolution is a milestone for anyone dedicated to securing cloud infrastructure.

We are pleased to announce that Amazon has accepted StrongDM's native Go implementation of Cedar into the Cedar Policy Organization's official GitHub repository. This allows Go developers to use Cedar, a security and authorization framework built to be fast, secure, and analyzable natively in their Go programs.

Today, we’ll take a look at what just-in-time access (JIT) means and what types there are. You’ll also learn about what a JIT access solution can do for your organization. By the end of this article, you’ll understand how just-in-time access works, the best practices to ensure secured implementation, and how strongDM comes to the rescue.
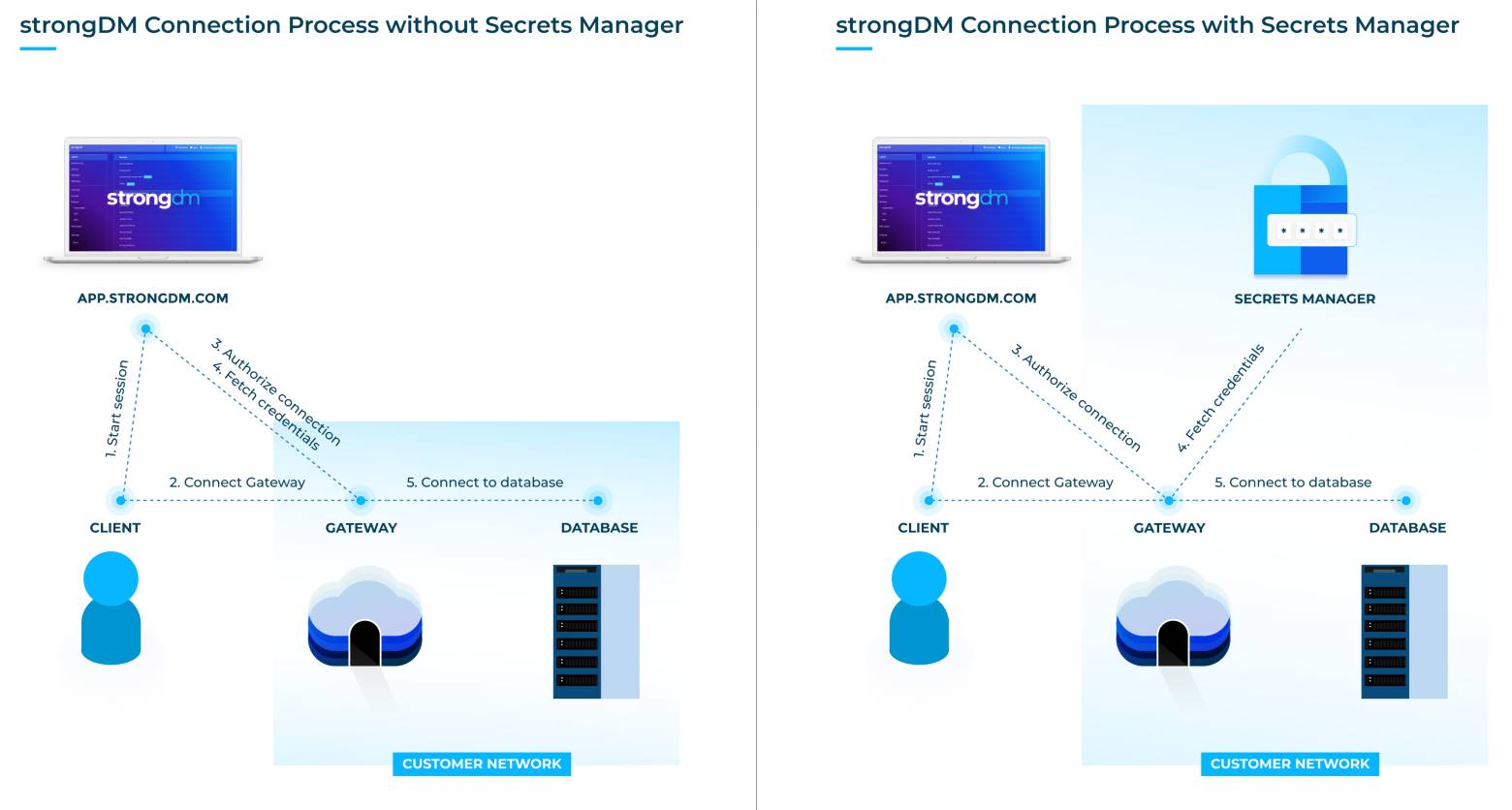
We’re pleased to announce public beta support for the use of third-party secrets managers with StrongDM to store your credentials. And the best part? There are zero changes to your workflow.

Terraform, we are a go for launch on the StrongDM provider! We are happy to announce that StrongDM has officially launched as a Terraform provider. That means that in one single configuration, you can spin up a fleet of servers, import them into StrongDM, and provision your users' access in a matter of minutes.

There are a number of ways to automate user provisioning but the real challenge lies in keeping track of those credentials.

On an unmodified MySQL install, the root user account does not have a password. This is extremely insecure! As a systems administrator, we know that the easiest way to compromise a system is using the default unchanged password with admin privileges.
Abstract-away usernames and passwords and allow the systems administrator to keep the master passwords safe under lock & key.

Should application developers have access to production database systems? This is a question as old as Vampires and Werewolves.

Gone are the days of sharing AWS root account credentials in a shared 1Password vault or worse, via email. With this in mind, one of the first steps to securing our AWS account is setting up AWS IAM.

It has never been easier for your company to build new infrastructure. In just a few clicks, you can spin up shiny new servers and databases in the cloud and start using them in seconds. However, in the rush to deploy new services so quickly, companies often let information security be an ...