What is Just-in-Time (JIT) Access? Meaning, Benefits & Pains


Written by
John MartinezLast updated on:
August 14, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
As the number and complexity of IT systems and applications continue to grow, security professionals and CISOs are facing increasing challenges when it comes to managing access to critical infrastructure. With traditional Privileged Access Management (PAM) solutions, the risks associated with standing access and overprovisioned access are still significant.
According to a Forcepoint report, it was found that as many as 44% of employees can share their privileged access with others, which can compromise organizational security.[1] The moment attackers get access to these privileges, they can alter your organization’s security posture dramatically.
Legacy PAM solutions, like CyberArk, fail to meet the demands of implementing just-in-time access across cloud resources, posing a substantial challenge and significantly elevating security risk.
What is Just-in-Time Access?
Just-in-Time (JIT) Access is a feature of privileged access management (PAM) solutions to grant users access to accounts and resources for a limited time when they need them. It reduces the risks associated with giving users more privileges than they require by providing this access only when it’s required.
Just-in-time access applies the principle of least privilege (PoLP) to reduce the risk of standing privileges (also called “always-on access”), where users have unlimited access to accounts, resources, and servers.
The Pains of Not Supporting Just-in-Time Access
Without the ability to support just-in-time access, security teams struggle to balance security and productivity. On the one hand, security teams must ensure that access to critical systems and data is restricted to authorized users to prevent data breaches and other security incidents. On the other hand, they must also ensure that legitimate users have access to the resources they need to do their jobs. This means that security teams must balance the need for strong access controls with the need for agility and flexibility.
The inability to support just-in-time access can have a number of negative impacts.
- Slow down productivity: When users have to wait for access to be granted, it can slow down productivity and reduce efficiency.
- Increase the risk of errors: Manual provisioning of access can increase the risk of errors and inconsistencies, which can lead to security breaches.
- Cause frustration: Employees may become frustrated when they can't access the resources they need to do their jobs, which can lead to low morale and reduced job satisfaction.
- Increase security risks: When access is granted for too long or to the wrong users, it can increase security risks and the likelihood of a data breach.
✨ Are you looking to automate just-in-time access for AWS, Azure, GCP, and more? It's easier than you think.
The Benefits of Adopting Enterprise-Wide Just-in-Time Access
To overcome these challenges, organizations are turning to enterprise-wide just-in-time access. This approach allows security teams to grant access to resources on an as-needed basis, ensuring that users have access to the resources they need when they need them, without compromising security. When no one has permanent access to a system, unauthorized access, malware, and other security risks drop dramatically.
Some of the benefits of adopting enterprise-wide just-in-time access include:
1. Reduces the Attack Surface
Just-in-time access control improves the security posture of an organization by reducing the threats caused by standing privileges. Several security risks emerge when malicious users exploit privileged accounts. By providing JIT access, you reduce the attack surface. Once a privileged user is done with a task, the account is disabled and privileges expire, improving the company’s security posture.
2. Simplifies Access Workflow
When users make requests for privileged access, the JIT approval process can be automated. This provides a seamless workflow for the administrators, operations team, and end-users without affecting productivity levels.
System administrators don’t have to wait days for review cycles, and users are granted access as needed. Operational efficiency is not affected in any way since privileged access requests can be approved automatically from anywhere.
💡Make it easy: Just-in-Time Access works best when it is easy for the end user to request and receive access. It should also be auditing to map the end to end chain of events, who is requesting access, why they are requesting it, and for how long. Play the video below to see how easy StrongDM makes Just-in-Time access and try it for yourself.
Through the web application, a user can see all the resources available to them based on their role or certain attributes. A user can request access, this can be configured to be automated or require human approval, once access is granted the user can start their session.
3. Enhances Compliance and Auditing
Implementing JIT access improves the compliance of your organization. You’re able to meet internal and external regulatory compliance requirements by enforcing least-privilege access and providing accurate audit reports.
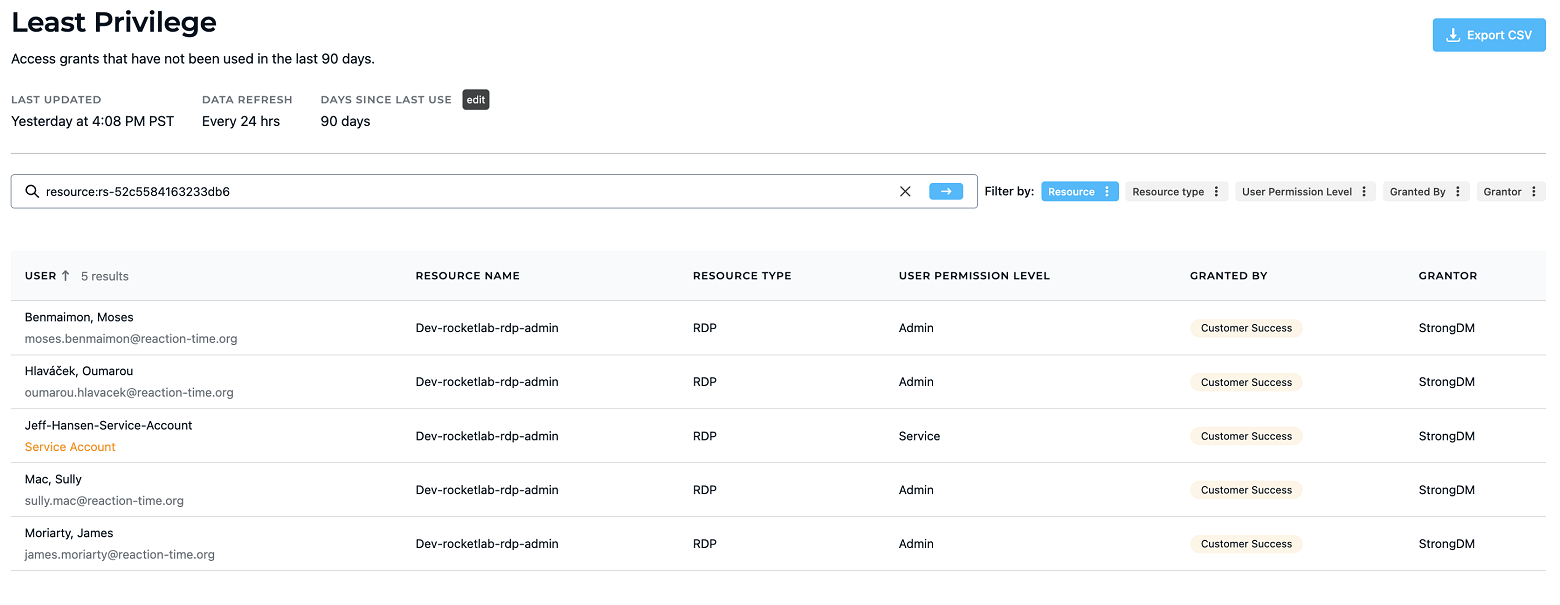
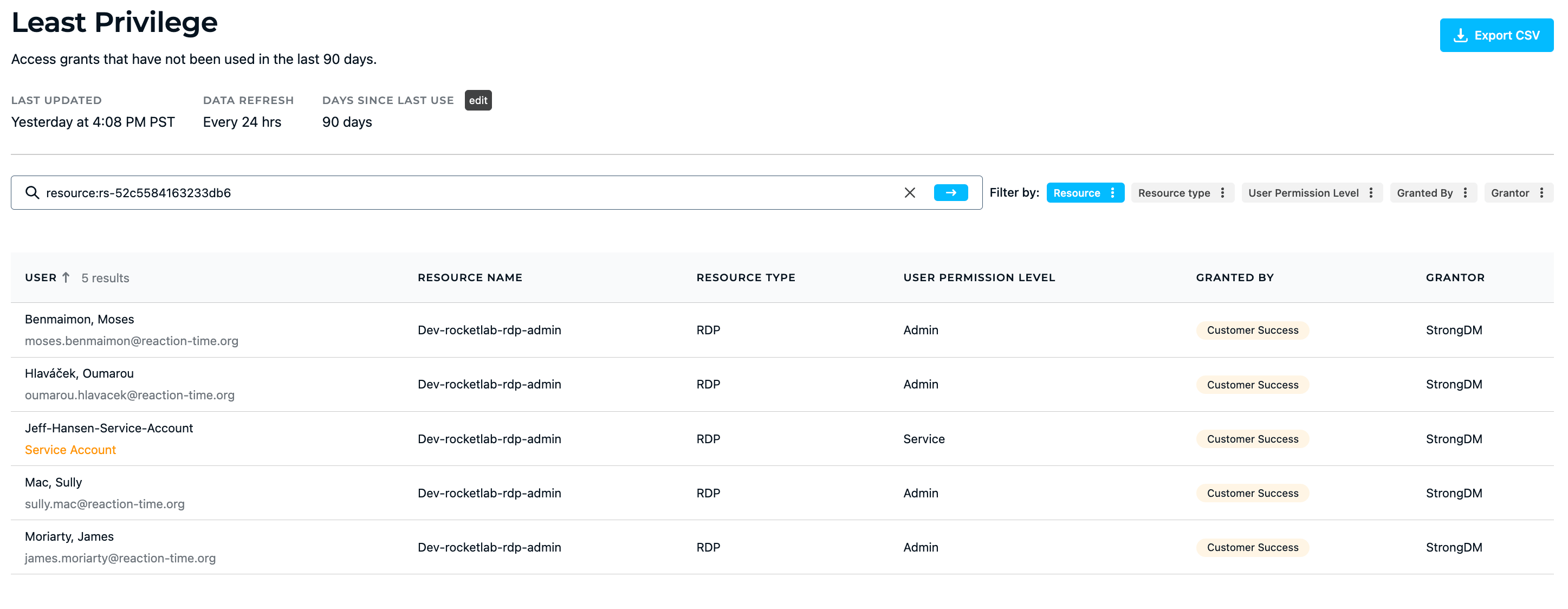
StrongDM has Advanced Insights which include reports that quantify access implementation. This can be used for compliance requirements and is also a resource to assess access hygiene.
Just-in-time access allows you to eliminate standing privileges and control privileged sessions. It allows you to simplify audits by logging privileged-access activities in a central location and providing complete audit trails and a granular view of all these activities.
4. Defines Third-Party Access
Providing access to third-party users can be a struggle. But, with just-in-time privileged access management (JIT PAM), administrators can provide contractors and application vendors time-bound access to a system.
You can create one-time accounts or grant third parties temporary privilege elevation to perform certain tasks such as testing, troubleshooting, and maintenance.
5. Allows Automated System Tasks
Service accounts and other non-human accounts, require just-in-time access to perform automated system tasks.
You can create these accounts and allow them to perform automated tasks without delay by defining specific timeframes and actions they can perform once approved for privileged access.
6. Eases Management of Privileged Accounts
When organizations implement JIT access, privileged account management becomes easier. Since there are no accounts with standing privileges, this eliminates the constant need for password reset and recovery processes.
Also, a lot of tasks are automated such as credential rotation, privileged access expiration, and account deletion. The process of request approval can also be automated such that the system reviews user requests and grants them privileged access without an administrator being manually involved.
Through the web application, a user can see all the resources available to them based on their role or certain attributes. A user can request access, this can be configured to be automated or require human approval, once access is granted the user can start their session. Try it yourself.
How StrongDM Makes Just-in-Time Access Possible
StrongDM is a platform that makes just-in-time access possible for all infrastructure, whether it's on-premise, hybrid, or in the cloud. The platform provides a centralized platform for managing access control across all infrastructure, making it easy to grant and revoke access on an as-needed basis.
With StrongDM, security teams can:
- Automate access control: StrongDM automates access control, ensuring that users only have access to the resources they need when they need them.
- Monitor access: StrongDM provides real-time monitoring and auditing of all access, making it easy to detect and respond to security incidents.
- Streamline provisioning and deprovisioning: StrongDM streamlines the provisioning and deprovisioning of access, reducing the risk of errors and inconsistencies.
StrongDM makes just-in-time access possible for all infrastructure, providing organizations with the flexibility and agility they need to remain productive and secure. Want to see it action? Book a demo.
Just-in-Time Access Frequently Asked Questions
How many types of Just-in-Time Access are there?
Standing privileges increase attack surfaces for bad actors to exploit. But, by implementing a just-in-time access solution, you can significantly eliminate these risks.
Here are the three types of JIT access:
1. Justification-Based Access
This is also called the “broker and remove” access. This JIT access approach demands that users justify why they need privileged access. Once justified, these users are then able to connect to a specific resource for a limited period.
The credentials for these accounts are managed and rotated in a central vault and unknown to users even after using them to reduce the risk of privilege abuse.
2. Ephemeral Accounts
This just-in-time access solution mitigates risks through the provision of short-lived or one-time accounts. In this case, you create a temporary account to give a user limited access to complete a specific task.
If a low-level or third-party user needs access to a resource, rather than creating a standard account, an ephemeral account is the best solution. This is because giving them access to a business-sensitive infrastructure for a long time can become a risk that malicious users can exploit.
You create dynamic access using a one-time account that gives the user temporary privileges until the task is done. After completing the task, the account is automatically disabled or deleted.
3. Privilege Elevation
This is also known as “temporary elevation.” A user makes a request if they need a higher level of privileged access to perform a task. This approval is either granted by an automated system or manually approved by the administrator with specifics on how long the task will take.
This JIT access is designed to reduce the amount of time a user spends on a critical system. Once the time allocated to complete the task elapses, the system takes away the user’s privilege to access the system.
What are the benefits of Just-In-Time Access?
There are several advantages of using a just-in-time privileged access solution to manage organizational processes and security.
Here are the top eight benefits of JIT access:
1. Improves Cybersecurity Posture
Just-in-time access control improves the security posture of an organization by reducing the threats caused by standing privileges. When no one has permanent access to a system, unauthorized access, malware, and other security risks drop dramatically.
Several security risks emerge when malicious users exploit privileged accounts. By providing JIT access, you reduce the attack surface. Once a privileged user is done with a task, the account is disabled and privileges expire, improving the company’s security posture.
2. Simplifies Access Workflow
When users make requests for privileged access, the JIT approval process can be automated. This provides a seamless workflow for the administrators, operations team, and end-users without affecting productivity levels.
System administrators don’t have to wait days for review cycles, and users are granted access as needed. Operational efficiency is not affected in any way since privileged access requests can be approved automatically from anywhere.
3. Evaluate Tasks and Privilege Control
By implementing just-in-time access, you can specify what a user gets privileged access to, what types of actions they can perform, and how long that privileged access lasts for.
Through privilege elevation, users can perform certain tasks, such as basic troubleshooting and app installation and updates, without getting access to a high-level administrator account.
Also, you can use just-in-time access for developers to create vaults that support DevOps workflows and give them access to the resources they need to build, test, and launch products when they need this privilege.
4. Enhances Compliance and Auditing
Implementing JIT access improves the compliance of your organization. You’re able to meet internal and external regulatory compliance requirements by enforcing least-privilege access and providing accurate audit reports.
💡Make it easy: StrongDM has several reports to quantify access implementation. This can be used for compliance requirements and is also a resource to assess access hygiene. With the ability to see outstanding access grants that have not been used in the past 90 days, admins can revoke these grants. Try it yourself.
Just-in-time access allows you to eliminate standing privileges and control privileged sessions. It allows you to simplify audits by logging privileged-access activities in a central location and providing complete audit trails and a granular view of all these activities.
5. Defines Third-Party Access
Providing access to third-party users can be a struggle. But, with just-in-time privileged access management (JIT PAM), administrators can provide contractors and application vendors time-bound access to a system.
You can create one-time accounts or grant third parties temporary privilege elevation to perform certain tasks such as testing, troubleshooting, and maintenance.
6. Provides Credential Protection
Once a user gets access to an account and completes a task on a JIT basis, the system automatically rotates and generates credentials in a secret vault. This way, the credentials are unknown to the user who used them.
The JIT access system can rotate passwords or create new accounts and disable them once the checkout window closes. This JIT security ensures that in cases where attackers steal passwords to user accounts, the accounts and privileges are invalidated.
7. Allows Automated System Tasks
Service accounts and other non-human accounts, require just-in-time access to perform automated system tasks.
You can create these accounts and allow them to perform automated tasks without delay by defining specific timeframes and actions they can perform once approved for privileged access.
8. Eases Management of Privileged Accounts
When organizations implement JIT access, privileged account management becomes easier. Since there are no accounts with standing privileges, this eliminates the constant need for password reset and recovery processes.
Also, a lot of tasks are automated such as credential rotation, privileged access expiration, and account deletion. The process of request approval can also be automated such that the system reviews user requests and grants them privileged access without an administrator being manually involved.
How does Just-in-Time Access work?
When an organization decides to implement a “zero standing privileges” approach with just-in-time access, here’s how it works:
For JIT access to work, the company defines the parameters of privileged access to reduce the attack surface. These are:
- Location: Where users make use of privileges
- Actions: What users do with their privileges
- Time: When these privileges can be used
Just-in-time access gives you monitoring control to see who or what has access to which resource, what tasks they performed, and for how long.
So, after your company sets up a just-in-time access solution, how does it work?
Let’s say John, who is an end-user, needs privileged access to perform certain operational tasks. Here’s what the typical JIT workflow looks like:
- John requests privileged access to what he needs, which can be a network, server, or resource.
- The request goes through an approval process. This is best automated to reduce friction and simplify workflows. However, requests can be manually approved by the admin who has the right to accept or revoke the request for privileged access.
- Once approved, John is given the level of privilege he needs to perform the required task. This access only lasts as long as he needs to complete the task.
- After John has completed his task and logs out, his privileges expire or the account is disabled until he needs it again.
This JIT-enabled workflow reduces the attack surface since his privileges expire once his task is complete.
In a just-in-time access implementation, attackers can’t steal passwords since there are no standing privileged accounts. Even in cases where malicious users manage to compromise passwords to systems, JIT access mitigates the risk from this due to either the privilege or account being disabled.
What are Just-in-Time Access best practices?
There are certain steps to take when implementing a just-in-time access solution.
Here are six best practices for enforcing JIT access:
1. Set Up Control Policies
Use attribute-based access control (ABAC) and role-based access control (RBAC) policies in tandem with JIT access to specify what tasks and actions users can perform.
Start by categorizing accounts to differentiate the rights accorded to each. Identify administrative tasks and separate admin accounts from end-user accounts. Then, set up control policies for accounts that need least privilege access and for what tasks.
With a just-in-time access solution, you can approve and monitor what privileged access every user has at any point in time.
2. Begin With High-Risk Use Cases
When implementing the JIT PAM solution, it’s more efficient to start with high-risk use cases. Thoroughly audit your cybersecurity system to discover high-risk accounts and vulnerability issues. These use cases might include high-level accounts (such as an admin account or service account) and third-party access.
Then, begin your JIT access implementation for existing vulnerabilities with the highest risks. After you’ve resolved the high-risk vulnerability issues, you can broaden the path of your just-in-time access implementation.
3. Create Granular Justification-Based Policies
Instead of allowing standing privileged access and giving room for cyberattacks over a broad surface area, you can create a just-in-time access policy that grants users access only by request.
Implement granular policies that ask users to request and provide justification for why they need access to a system, resource, or tool for a defined period.
4. Keep Credentials in a Secret Vault
When you create a centralized secret vault and keep all credentials and secrets there, you make security management more effective. The JIT access system rotates credentials in this vault so that they’re unknown to the privileged users and cyberattackers.
Also, a just-in-time access solution makes it easy to fully audit privileged access activities and discover vulnerabilities in systems.
5. Enable Temporary Access
Just like creating justification-based policies, you should implement procedures for temporarily elevating the privileges of users when they need to perform certain tasks.
Enable this JIT solution for human and non-human users that require access to privileged accounts or credentials.
6. Record and Audit JIT Privileged Activities
The JIT PAM system logs privileged access activities across all temporary accounts within the central vault for consistent and accurate logging and auditing.
Conclusion
You can significantly reduce security risks of your company by implementing a just-in-time access system to enforce zero standing privileges.
Start by identifying and implementing JIT access for your high-risk use cases. Then, expand the scope of your implementation after you’ve addressed the most critical vulnerabilities.
Looking to implement just-in-time access for your infrastructure? Check out our just-in-time access solution or get a no-BS StrongDM demo today.
References:
1. The State of Privileged User Abuse in United Kingdom and United States Government Organizations
2. Remove Standing Privileges Through a Just-in-Time PAM Approach
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like