Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
We’re pleased to announce public support for the use of third-party secrets managers with StrongDM to store your credentials. And the best part? There’s zero changes to your workflow.
Integrate and automate
We’ve designed StrongDM to work with any environment, no matter how diverse. And of course, we want to automate it all.
One of the important aspects of your infrastructure is secret management, so we’ve applied our philosophy to this key (pun intended :)) area of your network security. The goal is to provide more control for those of you that prefer to store your own credentials. In order to do that, StrongDM needs to support your existing secret store workflow and credential rotation without disruption to your developer workflow.
Works the way your organization does
Our integration with secrets management tools enables organizations to easily manage and automate the storage and rotation of credentials using these providers (with more to come in the future):
- HashiCorp Vault is an API-driven secret manager that integrates with many cloud architectures and platforms.
- AWS Secrets Manager is a highly utilized tool for protecting IT resources and app from unauthorized access.
- GCP Secret Manager stores API keys, passwords, certificates, and sensitive data pertaining to Google Cloud.
Some organizational security policies forbid the storage of credentials outside of a designated secret store provider. In other cases, there are specific features of a secret store that are key to your workflow, or you are just used to using your specific tool. With the integration of your secrets manager with StrongDM, you can meet all of these needs. When using your secrets manager with StrongDM, your gateway servers request credentials directly from your secret store and use them for authentication--that means those credentials are never recorded on our servers.
Gain control and custody
With these integrations comes the ability for StrongDM customers to:
- Decide where your credentials are stored, with us or your existing secrets manager.
- Plug a third-party secrets manager right into your StrongDM deployment without any workflow change.
- Create a separation of duties between access and authorization such that no credentials ever touch StrongDM hosted infrastructure.
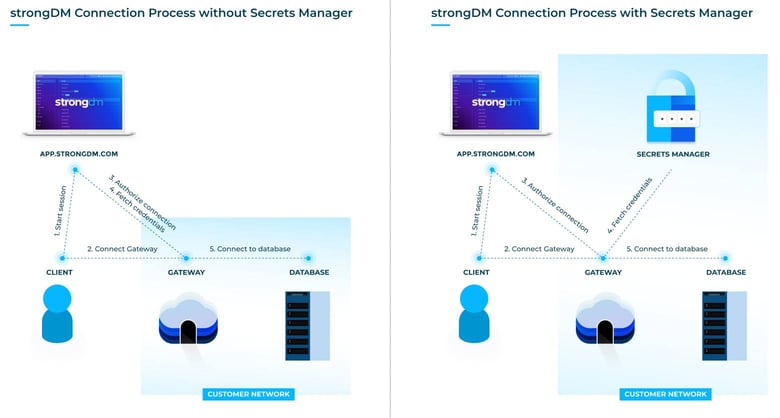
How it works
Whenever a user connects to a resource, the gateway/relay authenticates to your secrets manager provider and fetches credentials for the resource from the secret store. Those credentials never leave your gateway/relay and are never recorded by StrongDM.
To integrate with a secret store provider, you will need to follow these three basic steps:
- Configure your existing secret store for use with StrongDM (and populate it with the credentials for your resources).
- Set up your gateway/relay servers to be able to authenticate with the secret store.
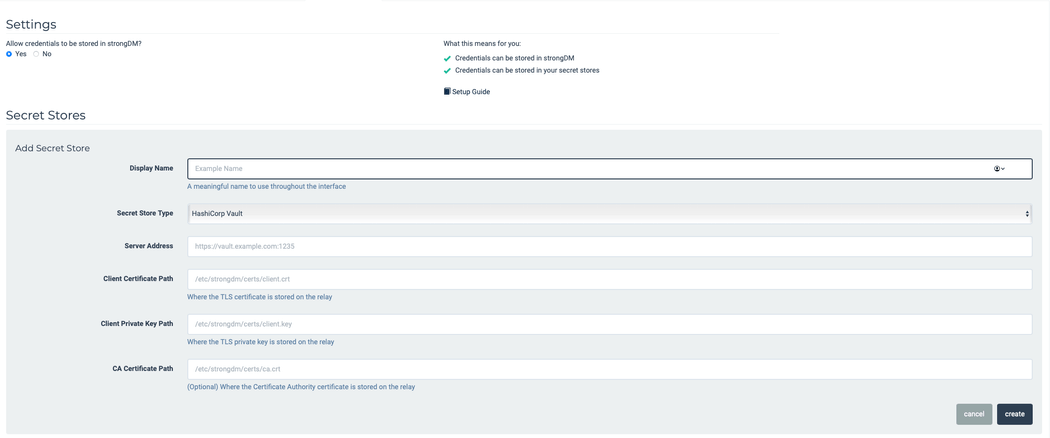
- Set up the secret store integration in StrongDM.
Then, each time you set up a new resource, you can point to the specific paths within the secret store where the credentials can be accessed instead of saving those credentials in StrongDM. For further detail about the setup process for these integrations, please choose from the following configuration guides:
- HashiCorp Vault
- AWS Secrets Manager
- GCP Secret Manager
- Azure Key Vault
- CyberArk Conjur
- Delinea Secret Server
Getting Started
If you’re already a StrongDM customer, check out the links below to get started. If not, you can set up a demo and get the ball rolling.
- Secret Stores Reference
- Secret Stores Configuration Guides
- Secret Stores Settings/Admin UI Guide
- Configure SDM & HashiCorp Vault Documentation
- Configure SDM & AWS Secrets Manager Documentation
- Configure SDM & GCP Secret Manager Documentation
- Configure SDM & Azure Key Vault Documentation
- Configure SDM & CyberArk Conjur Documentation
- Configure SDM & Delinea Secret Server Documentation
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Jeff Smith, Lead Technical Writer, has led projects and teams working on documentation in access and security for more than six years. Learning these technologies and helping other people do the same is his passion. Jeff contributes occasionally to various technical blogs and publications and sometimes writes on non-software topics such as productivity, project management, and tech news. To contact Jeff, visit him on LinkedIn.
You May Also Like




