Creating Postgres users isn't just a routine step in the complicated world of database management; it's a critical strategy that has a significant impact on how PostgreSQL databases operate and remain secure. An increasing number of organizations depend on sophisticated data systems, so it's critical to recognize the value of Postgres users. This blog post walks you through the steps of creating a Postgres user, as well as, explores the significance of these users in database administration,
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

The number and complexity of databases that every organization must manage has skyrocketed. If you need access - or need to provide it - it can sure be a pain in the access to manage.

Today, we’ll take a look at what just-in-time access (JIT) means and what types there are. You’ll also learn about what a JIT access solution can do for your organization. By the end of this article, you’ll understand how just-in-time access works, the best practices to ensure secured implementation, and how strongDM comes to the rescue.

Database sprawl is a lot like expanding into the suburbs: your house may be empty at first, but before you know it, you’re having to stuff things into your attic.
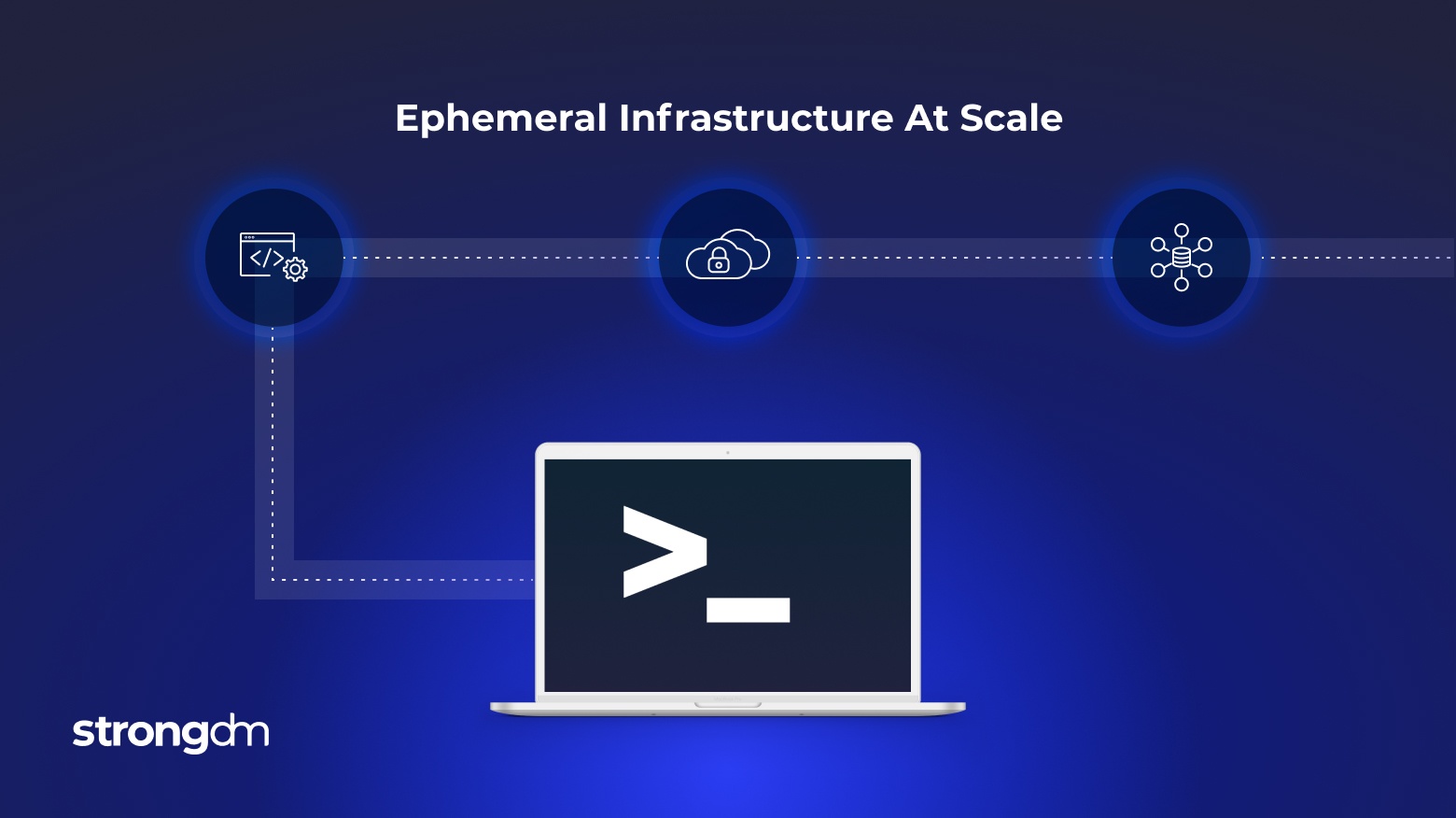
Managing a static fleet of strongDM servers is dead simple. You create the server in the strongDM console, place the public key file on the box, and it’s done! This scales really well for small deployments, but as your fleet grows, the burden of manual tasks grows with it.

In our last post, we discussed some of the challenges that are inherent to management of SSH keys across your infrastructure as you scale the number of team members and servers. In this post, we will dig into some of your options and the trade-offs that they provide.
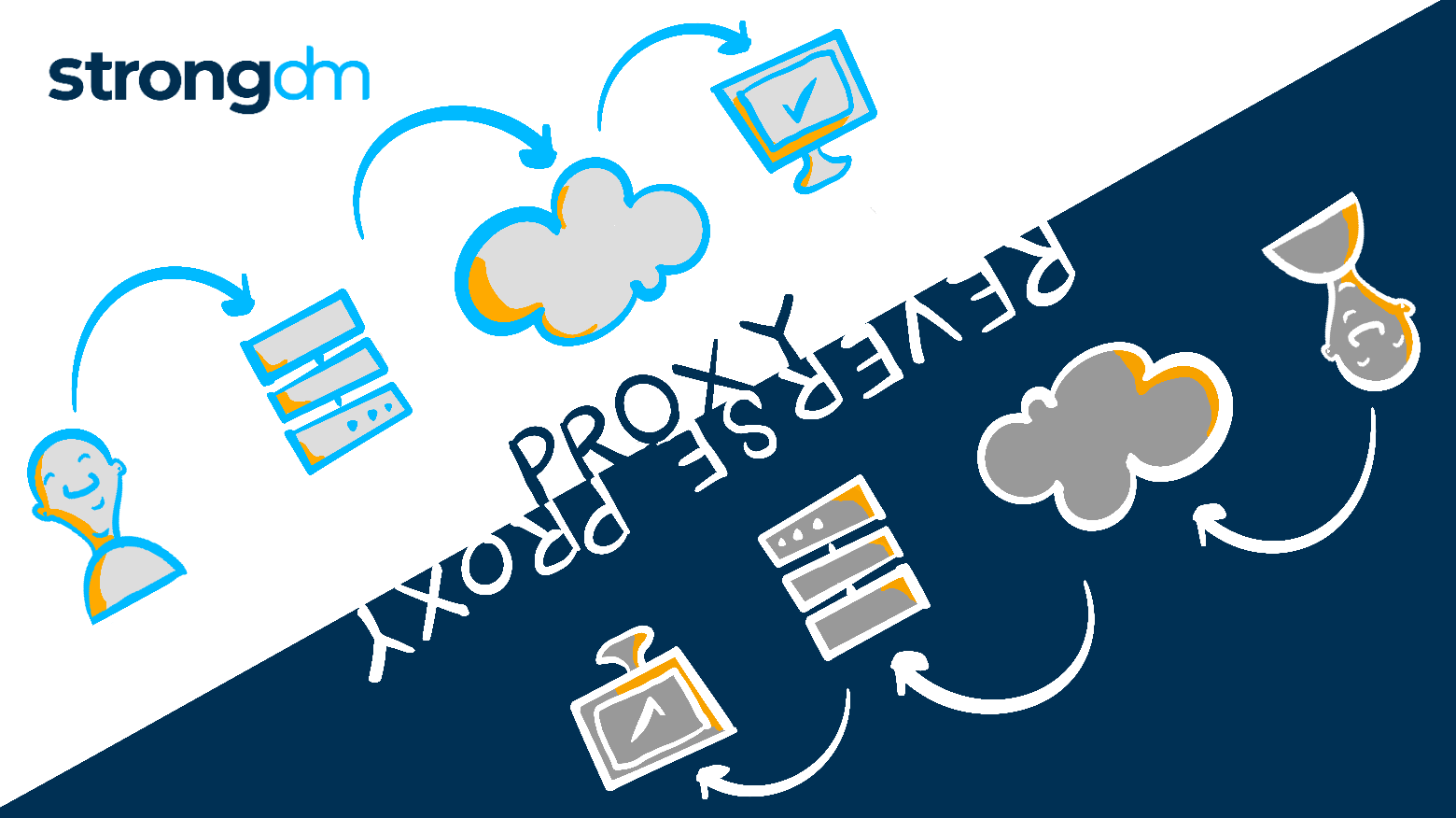
In this post, we’ll dissect the two concepts and explain how administrators can use a reverse proxy for easy access management control.

Consider this when you choose to integrate Active Directory (AD) with your databases and applications using their native APIs, connectors, or toolkits.

Find an easier way to manage access privileges and user credentials in MySQL databases. Reduce manual, repetitive efforts for provisioning and managing MySQL access and security with strongDM.

On an unmodified MySQL install, the root user account does not have a password. This is extremely insecure! As a systems administrator, we know that the easiest way to compromise a system is using the default unchanged password with admin privileges.

Configure the hosts for logging verbose data, and then send the logs to a cloud provider for long-term storage and access.
Abstract-away usernames and passwords and allow the systems administrator to keep the master passwords safe under lock & key.



