Should application developers have access to production database systems? This is a question as old as Vampires and Werewolves.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

Gone are the days of sharing AWS root account credentials in a shared 1Password vault or worse, via email. With this in mind, one of the first steps to securing our AWS account is setting up AWS IAM.

It has never been easier for your company to build new infrastructure. In just a few clicks, you can spin up shiny new servers and databases in the cloud and start using them in seconds. However, in the rush to deploy new services so quickly, companies often let information security be an ...
While primarily geared towards developers, PostgreSQL is also designed to help system administrators safely and robustly store information in databases. In this post, we will demonstrate how to install a PostgreSQL database and then configure Active Directory users to authenticate to it.
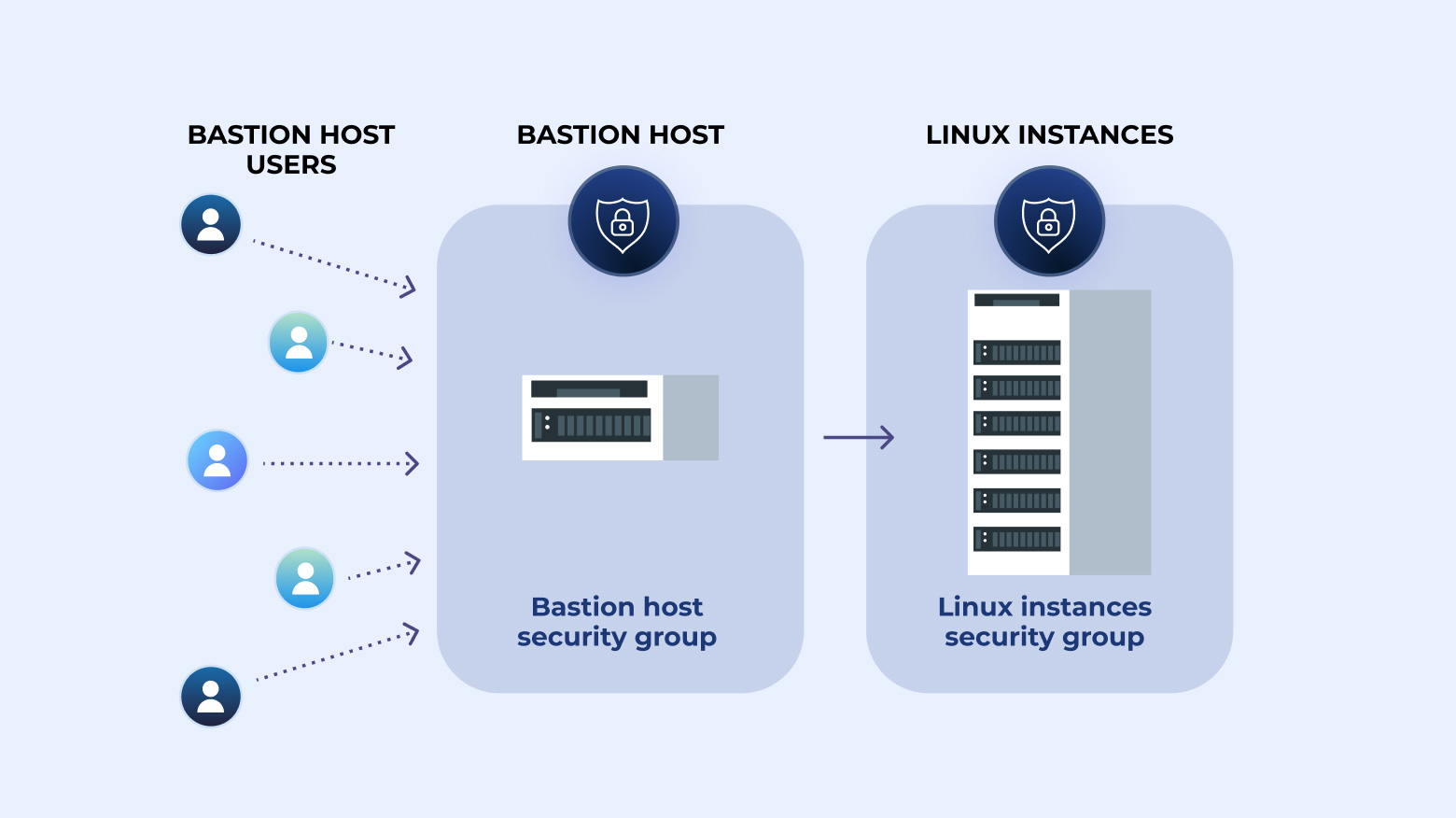
Step-by-step instructions on how to create a bastion host plus how to create an audit trail by logging SSH commands.

A staggering amount of cybersecurity breaches are caused by software vulnerabilities. From the early worms of the 1980s through the early 2000s - like Blaster, Code Red, and Melissa - to the notable Petya and WannaCry of the past few years, these vulnerabilities are all rooted in software flaws that allowed systems to be exploited. A software development lifecycle (SDLC) policy helps your company not suffer a similar fate by ensuring software goes through a testing process, is built as securely
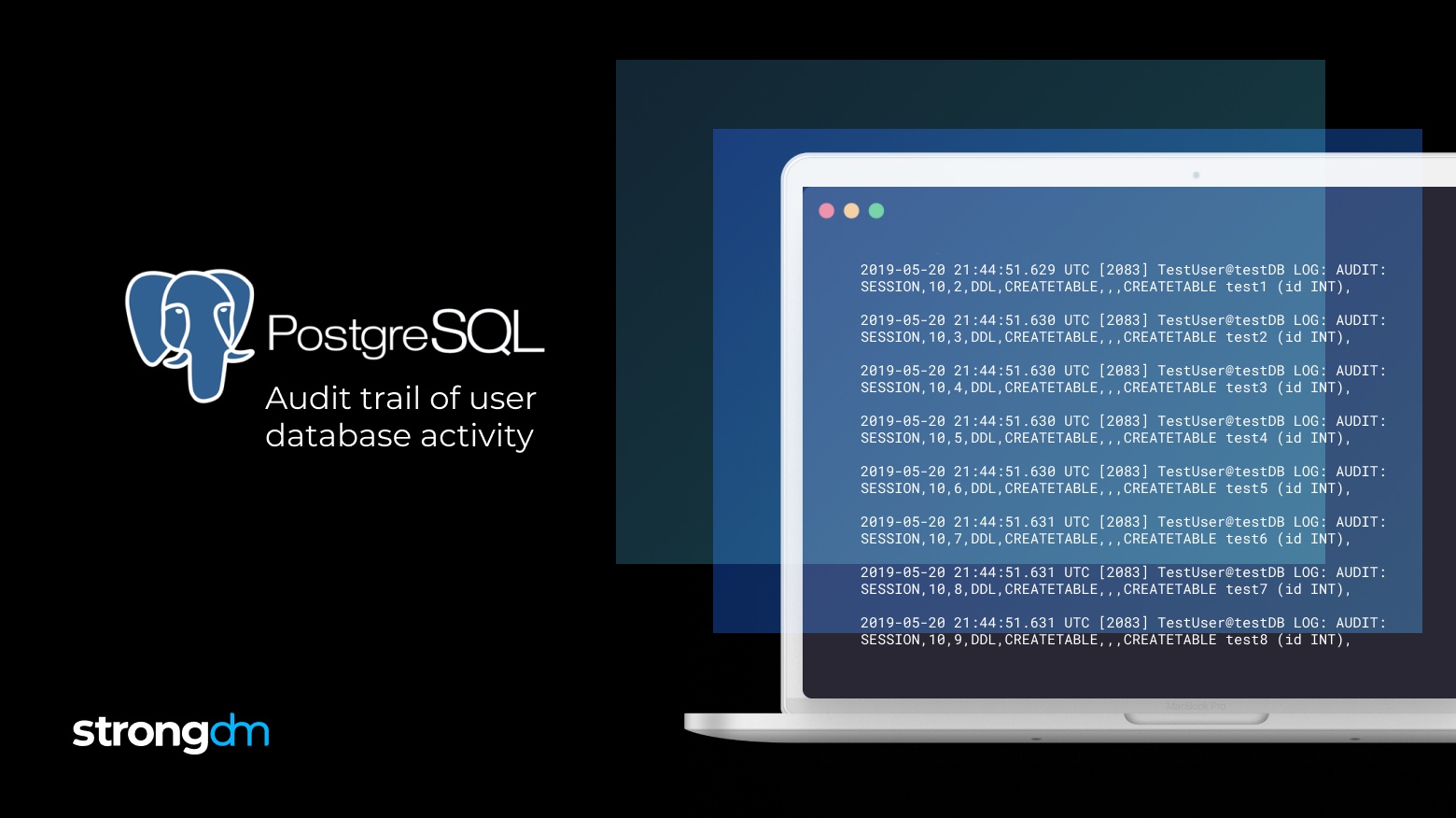
This is the first step to create an audit trail of PostgreSQL logs. Postgres can also output logs to any log destination in CSV by modifying the configuration.


