Here’s the scenario: On one side, you’re inundated with requests to provide access to critical infrastructure in order to enable teams to do their jobs; on the other side, you’re tasked with auditing access and ensuring that security to those systems is solid.
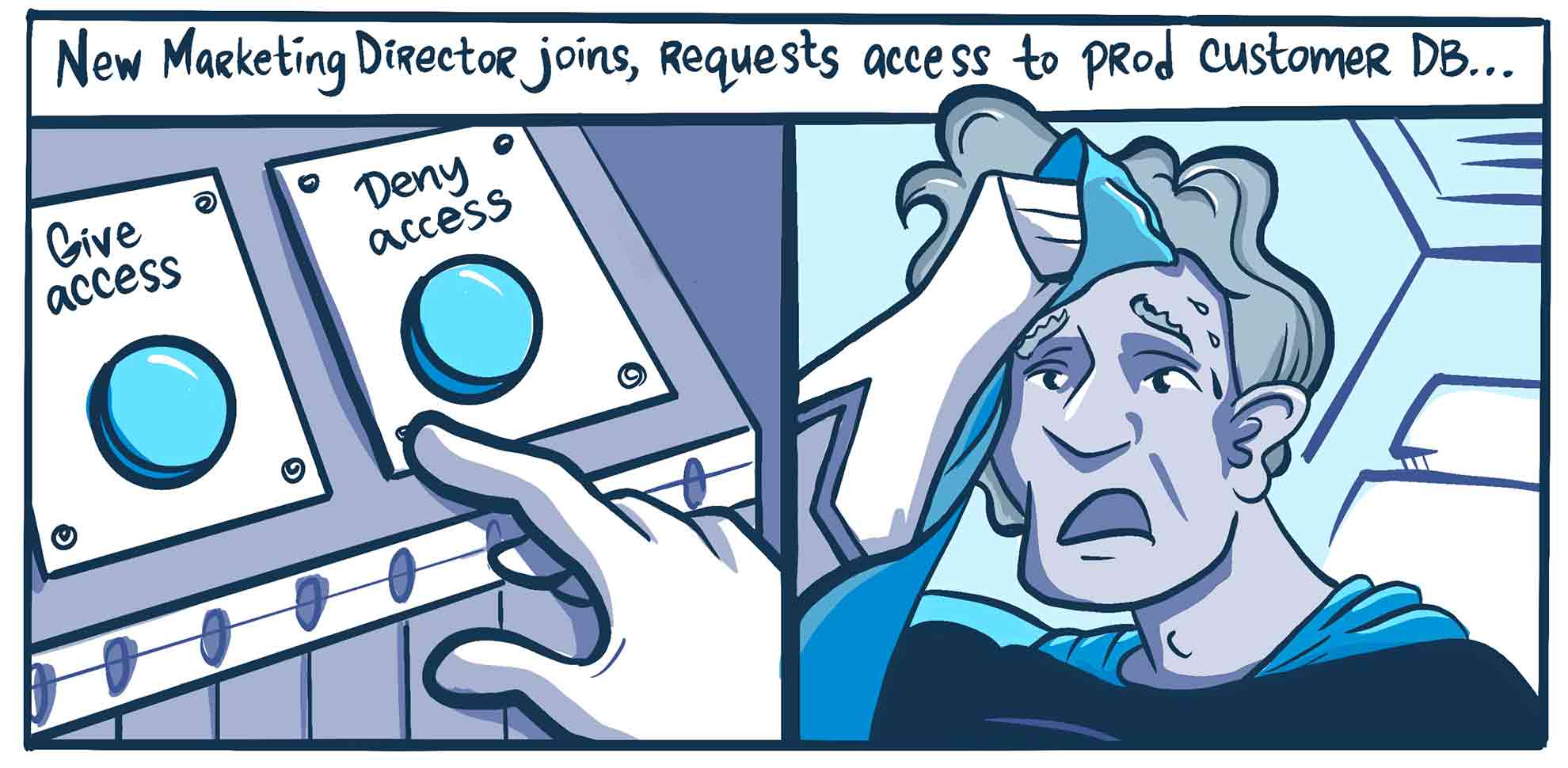



_optimized-3.png)