

Written by
John MartinezLast updated on:
September 29, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
HashiCorp Vault is a powerful secrets management tool that is well suited to automating the creation, distribution, and destruction of secrets. However, if your goal is to secure access to sensitive systems, a secrets store is not the only approach. In this blog post, we’ll look at a few HashiCorp Vault alternatives, with my take on the strengths and weaknesses of each approach.
HashiCorp Vault Overview
Brief product summary
Vault is a complete secrets management product, allowing end users to interact with a secure vault (server) to store, retrieve, and generate credentials for a wide variety of systems, including databases, various cloud providers, and SSH. It is built on a client-server model and is accessible via a command-line tool, a REST API, and a web interface. Its capability of creating and deleting ephemeral credentials allows users to build secure automation functionality with minimal risk of leaking credentials.
Use Cases
- Storing sensitive credentials that can be accessed manually, via a CLI, or an API.
- Generating ephemeral credentials for one-time access to databases, cloud environments, and a variety of other secure environments.
- Securing automated processes that require secrets to connect to secure environments.
Pluses
- Because it has a fully functional API, it is well-suited for integrating with automated tools and processes.
- Ephemeral credentials increase security by existing only long enough to be used and then discarded.
- Any form of data can be stored via the API, CLI, or web UI, making it a very flexible method of protecting a wide variety of secrets: credentials, API keys, tokens, and even binary data via Base64 encoding.
Minuses
- API and command-line utility, not user-transparent.
- Not suitable for end-user credential management.
- Requires custom integration work to fit into existing workflows.
- Complex pricing model.

1. StrongDM
Brief product summary
StrongDM is a control plane that makes it easier for organizations to secure access to databases, servers, and Kubernetes. Instead of distributing access across a combination of VPN, individual database credentials, & SSH keys, StrongDM unifies management in your existing SSO and keeps credentials hidden. Neither credentials nor keys are accessible by end users. Because StrongDM deconstructs every protocol, it also logs all database queries, complete SSH and RDP sessions, and kubectl activity.
Use Cases
- Faster onboarding - no need to provision database credentials, ssh keys, VPN passwords for each new hire.
- Secure offboarding - suspend SSO access once to revoke all database, and server access.
- Automatically adopt security best practices - least privilege, just-in-time access, ephemeral permissions, audit trail.
- Comprehensive logging and reporting- log every permission change, database query, ssh & kubectl command.
- Vendor privileged access management-connect third-party vendors to resources with project-based access that automatically expires.
- Security and compliance teams-simplify HIPAA, SOC 2, SOX, ISO 27001 compliance certification.
- Modern Cloud PAM solution-built to support a variety of cloud networks, including public, private, multi-cloud, and hybrid.
Pluses
- Easy deployment - self-healing mesh network of proxies.
- No change to workflow- use any SQL client, CLI, or desktop BI tool.
- Standardize logs across any database type, Linux or Windows server.
- Secret store support - fills in the gaps and offers the benefits of Vault alongside the benefits of StrongDM.
- Simple, straightforward pricing.
Minuses
- Requires continual access to StrongDM API for access to managed resources.
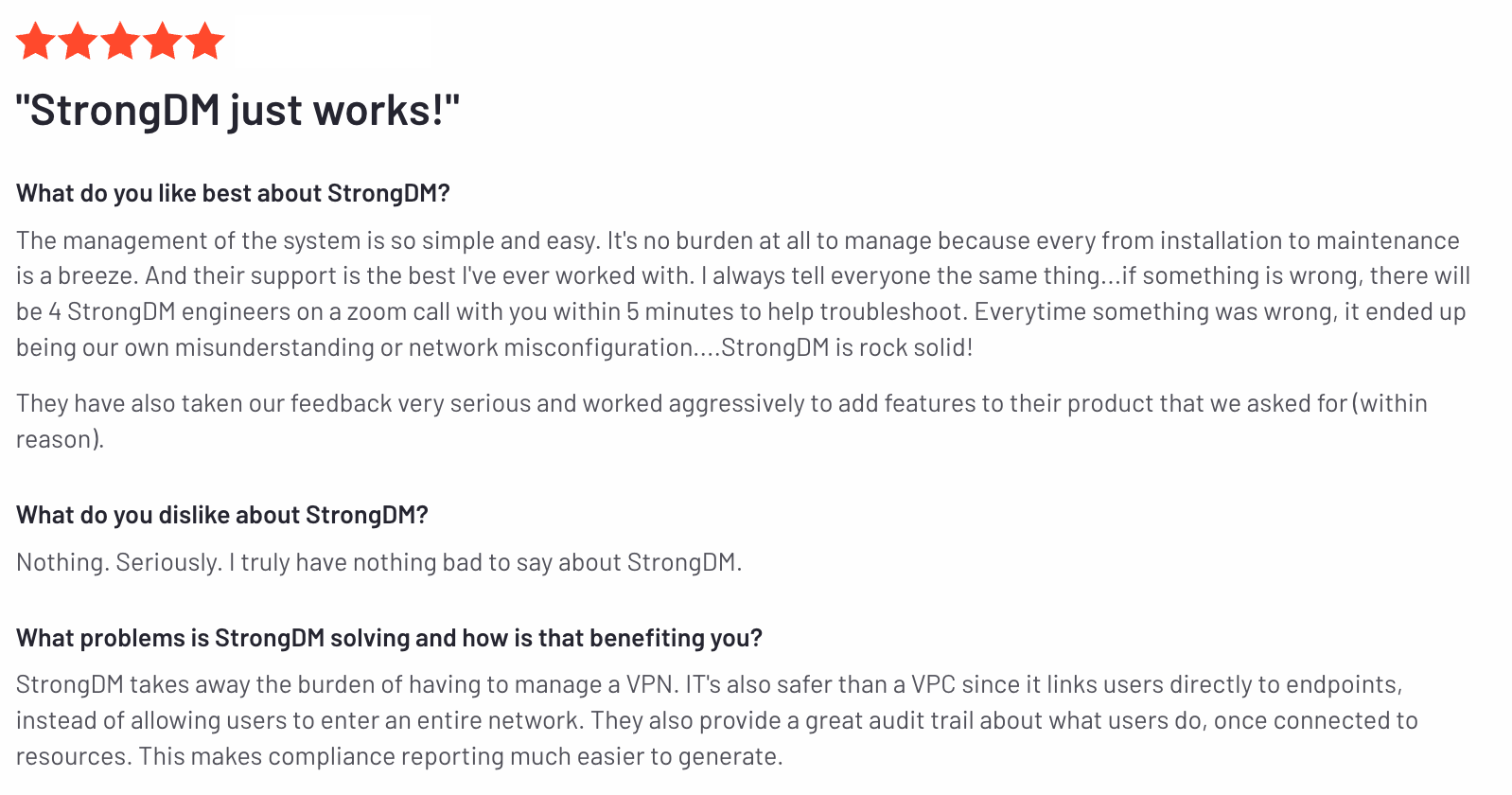
StrongDM’s G2 Reviews
- 4.8 / 5 stars
Read all of StrongDM’s G2 reviews here.
Pricing Information
StrongDM offers simple pricing, including support for all resource types.
Users have the option to sign up for a free 14-day trial.
2. HashiCorp Vault Open-Source
Brief product summary
The open-source version of HashiCorp Vault is the same as the enterprise version, though it is missing several enterprise features, including:
- MFA integration for client authentication.
- Vault replication and disaster recovery workflows.
- Namespaces for multi-tenancy.
- Support for hardware security modules.
Use Cases
Because this is a version of the enterprise Vault product, much the same use cases apply here. However, because it does not have numerous enterprise-level features, this product will require additional local modification to be suitable for enterprise deployment.
Pluses
- It’s free!
- Community resources available for configuration and troubleshooting.
Minuses
- Lacks enterprise-friendly features such as replication and disaster recovery capability.
- No formal support or SLA.
3. Homebrew (In-house)
Brief product summary
If you lack the budget for a commercial product, or if your use case does not fit neatly within the feature sets offered by commercial products, you always have the option of building a homebrew solution using in-house resources. Typically this will involve a significant engineering effort, both to scope and build the solution and to maintain it going forward. Not only that, but auditors may look askance at your homebrew solution unless it has been tested and validated by an outside authority such as a penetration test or white-box code analysis. The benefit, of course, is that you will be able to produce a tool that matches your specific needs.
Use Cases
Because a homebrew secrets management system is entirely developed in-house, it can be designed and built to accommodate any specific required use cases for the organization. In order to build a functional and secure homebrew secrets management tool, you will need to have significant in-house security engineering expertise.
Pluses
- It’s free (at least, in dollars).
- Fully customized to required use cases.
Minuses
- Extensive time investment for development and maintenance.
- In-house security engineering expertise required.
- No external support available.
- Extensive testing, including external testing, will be needed to verify solution from an auditing perspective.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like



