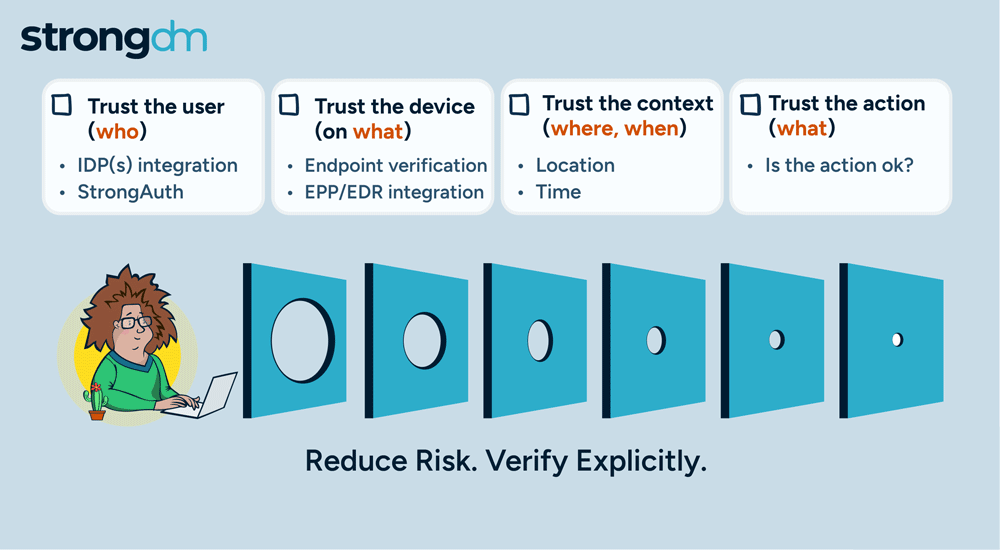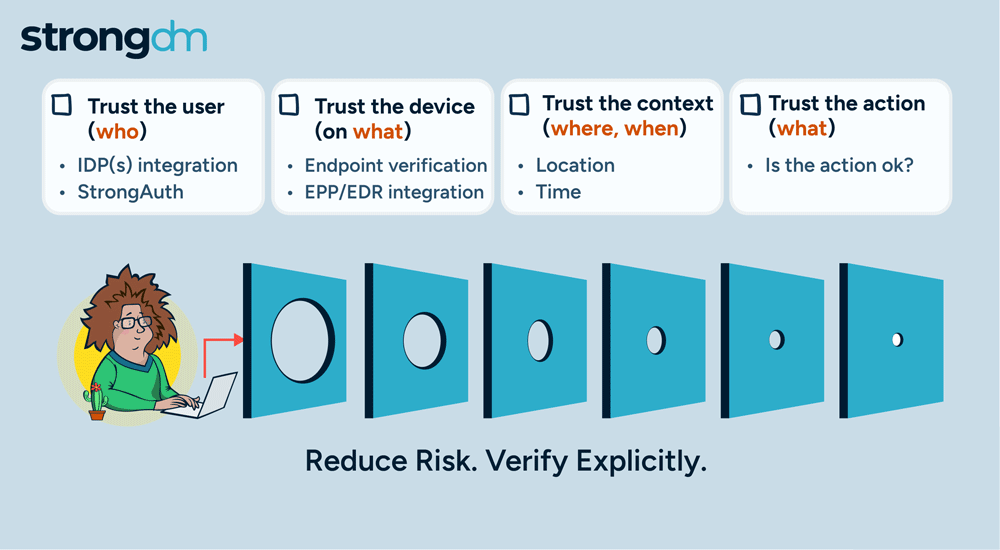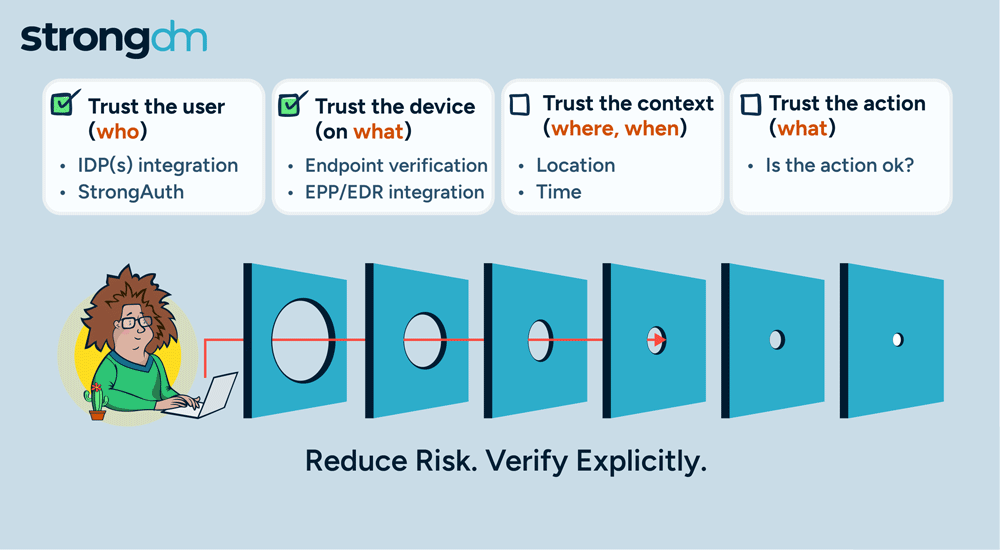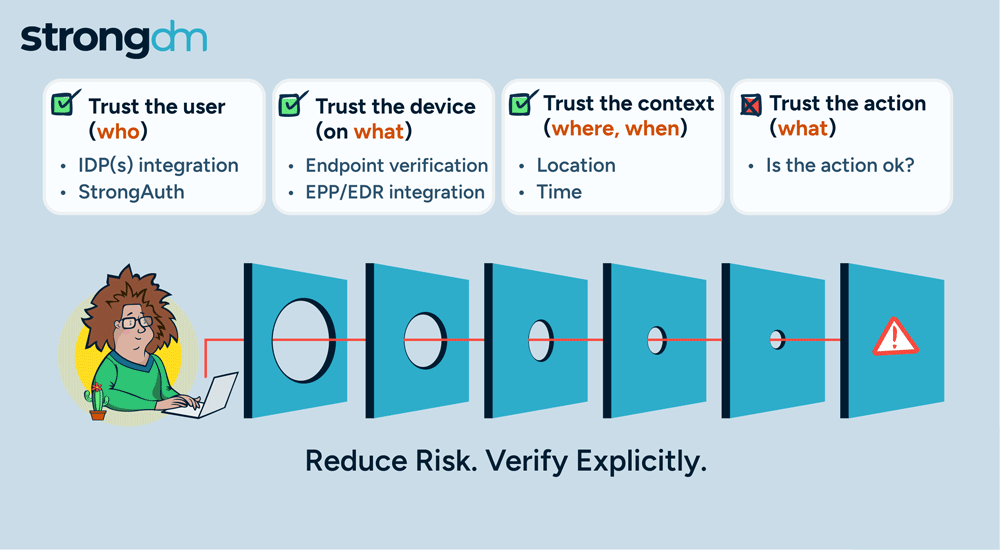
SQL injection attacks remain one of the most prevalent and dangerous threats to database security. These attacks can compromise sensitive data, disrupt operations, and cause significant financial and reputational damage. Understanding how to prevent SQL injection attacks will help you foster a security-conscious organizational culture.