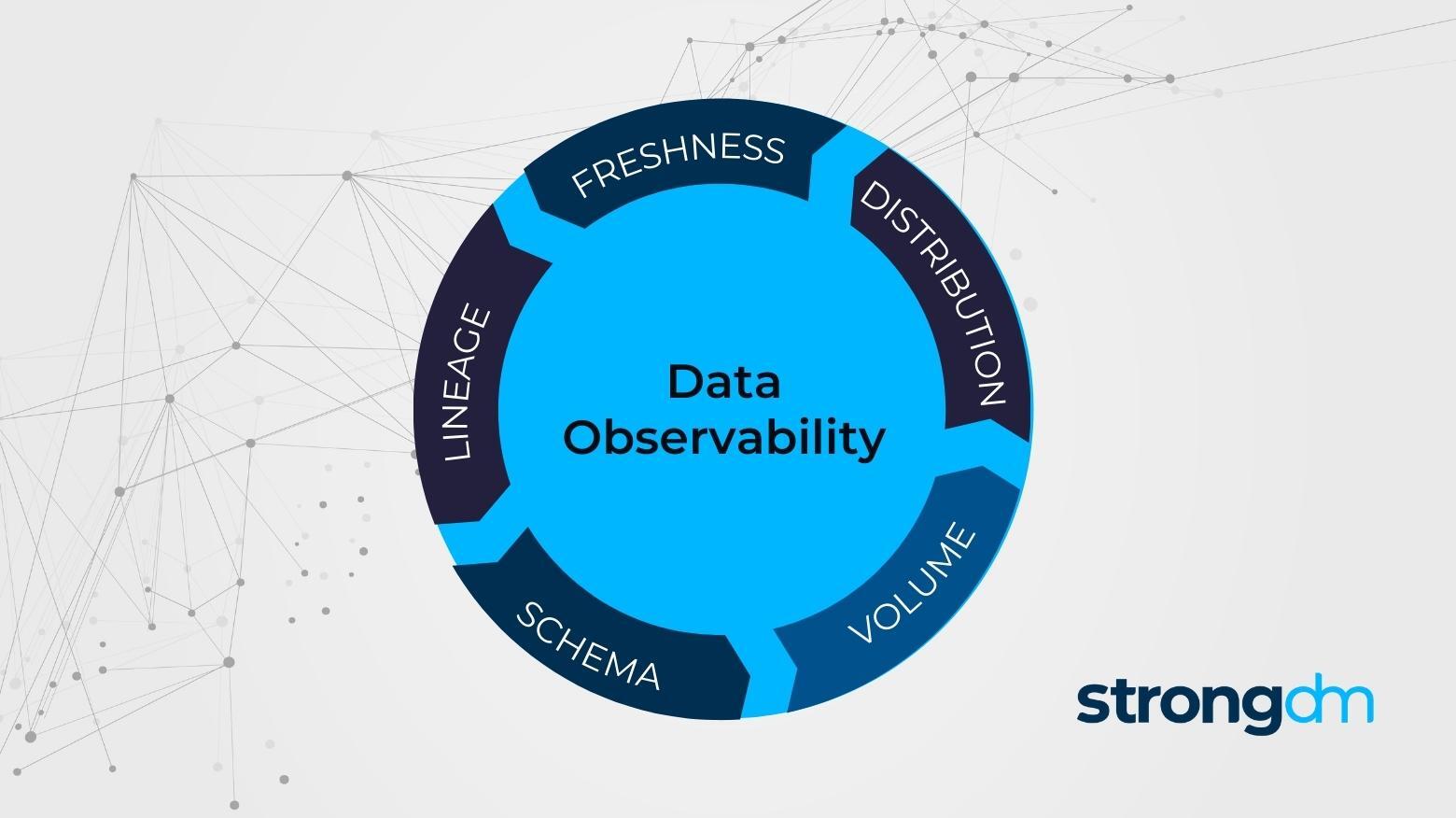
DevOps is a set of practices meant to integrate software development and IT operations—reducing the Systems Development Life Cycle (SDLC) and ensuring continuous delivery with high software quality. In this article, we share a list of excellent DevOps tools to improve the efficiency and agility of software development within your team.