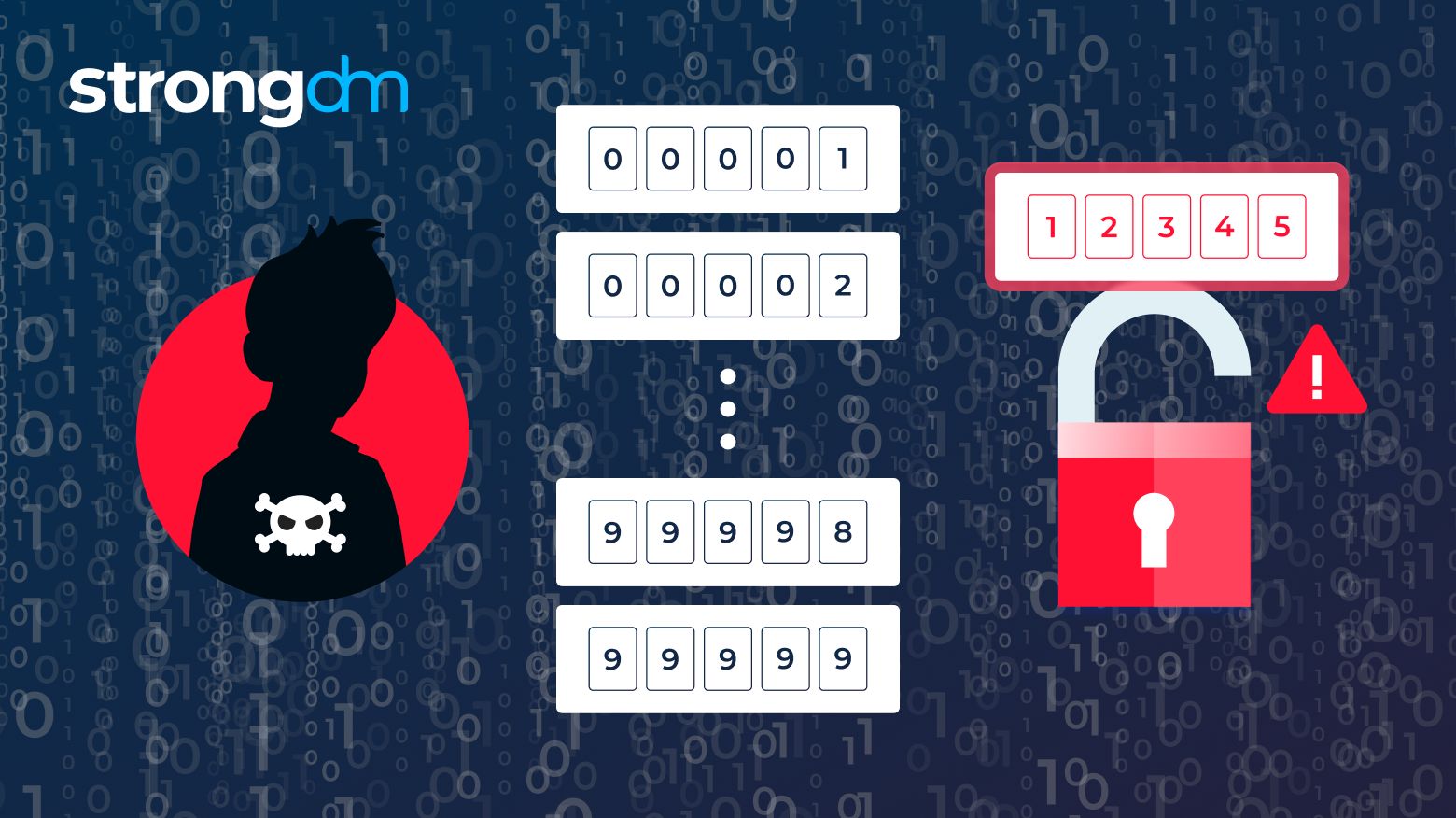
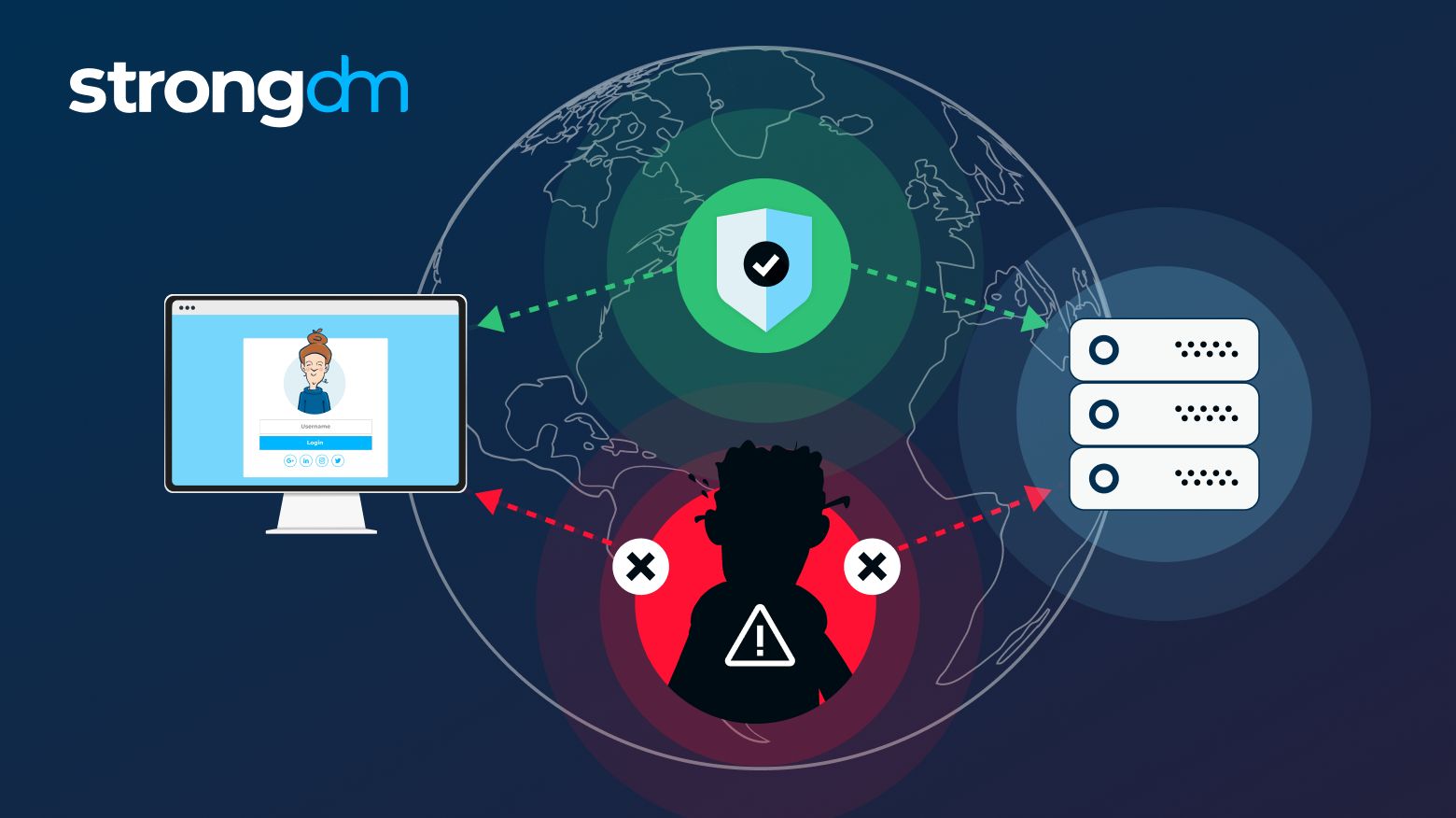
In this article, we’ll take a comprehensive look at brute force attacks: what they are, how they work, and the different shapes they can take. You'll learn about popular tools utilized by hackers and examples of brute force attacks in action. By the end of this article, you'll be able to understand critical prevention measures for brute force attacks.