ISO 27001 vs. 27002 vs. 27003: What’s the Difference?

Written by
John MartinezLast updated on:
October 17, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Summary: Organizations around the world rely on the standards set in the ISO 27000 series for information security management best practices. In this article, we’ll compare the first three standards in the ISO/IEC 27000 family: ISO 27001 vs. 27002 vs. 27003. By the end, you’ll have a better understanding of what each standard covers, how they differ from one another, and when to use them.
What is ISO 27001?
Originally published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), ISO 27001 makes up the core framework for the ISO 27000 series—a collection of documents outlining standards for information security management.
ISO 27001, also known as ISO/IEC 27001, is the central set of certification standards for planning, implementing, operating, monitoring, and improving an information security management system (ISMS).
An ISMS is a documented set of security controls designed to protect the confidentiality, availability, and integrity of assets from threats and vulnerabilities. While not all organizations pursue certification, many use ISO 27001 as a guiding framework for developing and implementing information security best practices.
What is ISO 27002?
ISO 27002, or ISO/IEC 27002:2022, provides guidance on the selection, implementation, and management of security controls based on an organization's information security risk environment.
In other words, it is a supplementary standard supporting ISO 27001 that goes into greater detail about the information security controls an organization may apply from the ISO 27001 list.
ISO 27002 organizes the controls into 14 main groups, described under clauses 5-18:
- A.5 Information security policies
- A.6 Organization of information security
- A.7 Human resource security
- A.8 Asset management
- A.9 Access control
- A.10 Cryptography
- A.11 Physical and environmental security
- A.12 Operations security
- A.13 Communications security
- A.14 System acquisition, development, and maintenance
- A.15 Supplier relationships
- A.16 Information security incident management
- A.17 Information security aspects of business continuity management
- A.18 Compliance
According to the International Organization for Standardization, ISO 27002 is designed to be used by organizations that intend to:
- Select controls within the process of implementing an Information Security Management System based on ISO/IEC 27001;
- Implement commonly accepted information security controls;
- Develop their own information security management guidelines.
What is ISO 27003?
ISO 27003, also called ISO/IEC 27003:2017, provides guidance for implementing an ISMS based on ISO 27001.
ISO 27003 covers the process of ISMS specification and design from inception to planning. It describes how to:
- obtain management approval to implement an ISMS
- define an ISMS implementation project
- plan the ISMS project
As a result, organizations that follow ISO 27003 will produce a final ISMS project implementation plan.
Clauses 4 through 10 mirror the organization of ISO 27001, making them easy to compare and reference. The descriptions follow the same structure throughout:
- Required activity: Outlines key activities required in the corresponding subclause of ISO/IEC 27001.
- Explanation: Explains what the requirements of ISO/IEC 27001 imply.
- Guidance: Provides additional details and supporting information to implement the “required activity,” with examples.
- Other information: Supplies further information that can be considered.
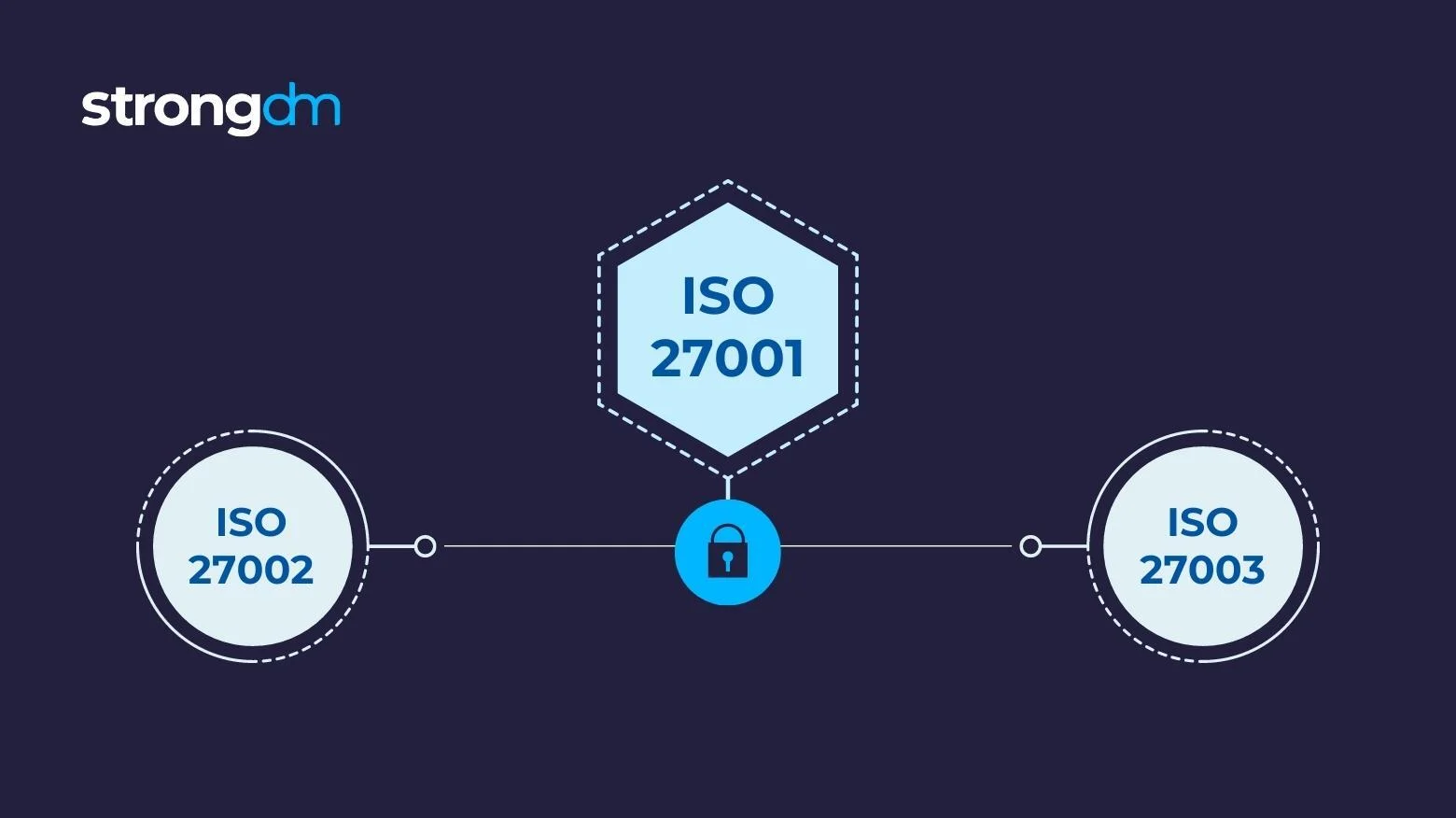
ISO 27001 vs. ISO 27002
The main difference between ISO 27001 and ISO 27002 is that ISO 27002 is a detailed supplementary guide to the security controls in the ISO 27001 framework.
ISO 27002 provides best-practices guidance on selecting and implementing the controls listed in ISO 27001. These controls are referenced in ISO 27001 documentation in Appendix A, which includes 114 security controls divided into 14 control sets.
But where ISO 27001 provides a brief outline of key information security controls, ISO 27002 describes them in depth, explaining how each control works, its purpose and objectives, and how it can be implemented. In other words, ISO 27002 is a supporting document and should be read alongside ISO 27001.
ISO 27001 vs. 27002 certification
It is also worth noting that ISO 27002 is not a certification standard—you can only certify to ISO 27001. ISO 27002 operates simply as a supporting guide while ISO 27001 provides the full list of compliance requirements for ISMS management.
ISO 27001 vs. ISO 27003
ISO 27003 provides basic but comprehensive guidance for all the requirements of an information security management system described under ISO 27001. This includes recommendations (‘should’), possibilities (‘can’), and permissions (‘may’) related to those requirements.
However, ISO 27003 is not a certification standard like ISO 27001—organizations are under no obligation to follow the guidance in ISO 27003. Additionally, as a supporting document, ISO 27003 does not add any new requirements or definitions outside of ISO 2001. Instead, it is intended to be used alongside ISO 27001 to provide further guidance and context surrounding the requirements listed.
The guidance provided in ISO 27003 is generic and designed to be applicable to all organizations, regardless of size, type, or nature. Instead, organizations should use ISO 27001 to identify which guidance is most relevant based on its specific context.
ISO 27002 vs. ISO 27003
Like ISO 27002, you can’t get certified under 27003, but both provide valuable support to organizations trying to meet ISO 27001 requirements.
ISO 27002 focuses its guidance on “determining and implementing controls for information security risk treatment in an information security management system (ISMS) based on ISO 27001.” ISO 27003 focuses its guidance more broadly on the overall requirements for an ISMS, based on ISO 27001.
Together, ISO 27002 and ISO 27003 help organizations better understand, identify, and implement the standards outlined in ISO 27001.
When to Use Each Standard?
How and when you use each standard will depend on your goals and current security posture.
When to use ISO 27001
ISO 27001 makes up the foundation for a robust information security management system, focusing on two key objectives:
- Risk assessment (identifying potential risks and vulnerabilities to data in the organization) and
- Risk mitigation (determining what steps to take to safeguard that data).
Organizations should use ISO 27001 when they:
- Want to achieve certification to international security standards
- Don’t have an ISMS and want to develop one based on best practices
- Want to assess and mitigate security risks in the organization
- Need to comply with business, legal, or regulatory requirements
When to use ISO 27002
ISO 27002 expands on the information in Annex A in ISO 27001 to provide further detail and guidance to organizations looking to implement security controls from the ISO 27001 list. Organizations should use ISO 27002 after they’ve identified the security controls they plan to implement from ISO 27001.
When to use ISO 27003
ISO 27003 provides additional guidance for all the requirements outlined in ISO 27001. Organizations should use ISO 27003 as a supplemental guide to define and plan an ISMS implementation project.
ISO 27002 and ISO 27003 help organizations successfully apply the framework they developed in ISO 27001. Therefore, they should be used in tandem with the ISO 27001 initiative.
How StrongDM Can Help Achieve ISO Compliance?
ISO 27001 provides the building blocks for a secure data management system.
Between ISO 27001 and its supporting ISO 27002 and ISO 27003 documents, organizations that follow ISO standards enjoy many benefits, including:
- Comply with business, legal, and regulatory requirements
- Mitigate the risk of a data breach
- Avoid costly financial penalties and losses
- Increase competitive advantage
- Strengthen your reputation
- Reduce the number of audits required
- Gain actionable insight to improve your security posture
Certification is the next step toward a more secure organization, but with over 100 security controls across 14 requirement groups to manage, achieving ISO compliance is no small feat.
That’s where StrongDM comes in. StrongDM is a proxy that helps organizations manage and audit access to their infrastructure.
Use StrongDM to help you comply with ISO 27001 requirements:
- Enforce segregation of duties through role-based, attribute-based, or just-in-time access control policies—all least privilege by default.
- Authenticate and authorize users to access critical infrastructure, with credentials safely stored in StrongDM or third-party secret stores of your choice.
- Enforce access control policies through network segmentation that prevents unauthorized horizontal access across the StrongDM architecture.
- Document events through comprehensive audit logs for all access to configured data sources—supporting investigations of security incidents and root cause analyses.
With StrongDM, you can simplify compliance while speeding up the audit process for faster certification and reliable security across all your systems.
Get the benefits of ISO compliance without the hassle.
Cyber incidents are among the top risks for businesses in 2022, according to the Allianz Risk Barometer. In recent years, the rise of remote work has expanded organizations’ risk exposure and an increase in ransomware attacks has led to millions of dollars in losses across industries. As a result, organizations are looking to strengthen their security postures to shore up key vulnerabilities and create sustainable business models going forward.
Achieving ISO compliance can not only increase global business opportunities, but also tighten security policies and practices throughout your organization.
Move forward with confidence with StrongDM. StrongDM is your partner in developing compliant systems with more protection and less hassle.
Get started today and try it free for 14 days.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like
![Understanding ISO 27001 Controls [Guide to Annex A]](https://discover.strongdm.com/hs-fs/hubfs/iso-27001-controls.jpg?width=300&height=168&name=iso-27001-controls.jpg)



