In essence, legacy PAM solutions over-index on access. StrongDM uses the principles of Zero Trust to evaluate and govern every action, no matter how minor - where each command, query, or configuration change is evaluated in real-time against dynamic policies that adapt to the context of the user, the sensitivity of the action, and the prevailing threat landscape.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

Zero trust is a security and authentication model that eliminates the assumption of trust and shifts the focus from a traditional security parameter, like a VPN or firewall, to the individual user. Nearly all (92 percent) cybersecurity professionals agree that it’s the best network security approach that exists. In this article, we’ll evaluate the top nine zero trust solutions and help you decide which is right for your organization.
Last week, Red Hat issued a warning regarding a potential presence of a malicious backdoor in the widely utilized data compression software library XZ, which may affect instances of Fedora Linux 40 and the Fedora Rawhide developer distribution. CISA, or Cybersecurity & Infrastructure Security Agency, confirmed and issued an alert for the same CVE.
Context-based access controls refer to a dynamic and adaptive approach to managing security policies in modern infrastructure. Addressing challenges in enforcing consistent security across diverse platforms, these policies consider factors such as device posture and geo-location to adjust access controls dynamically. By narrowing access based on contextual parameters, they reduce the attack surface, enhance security, and streamline policy administration, ensuring compliance in evolving
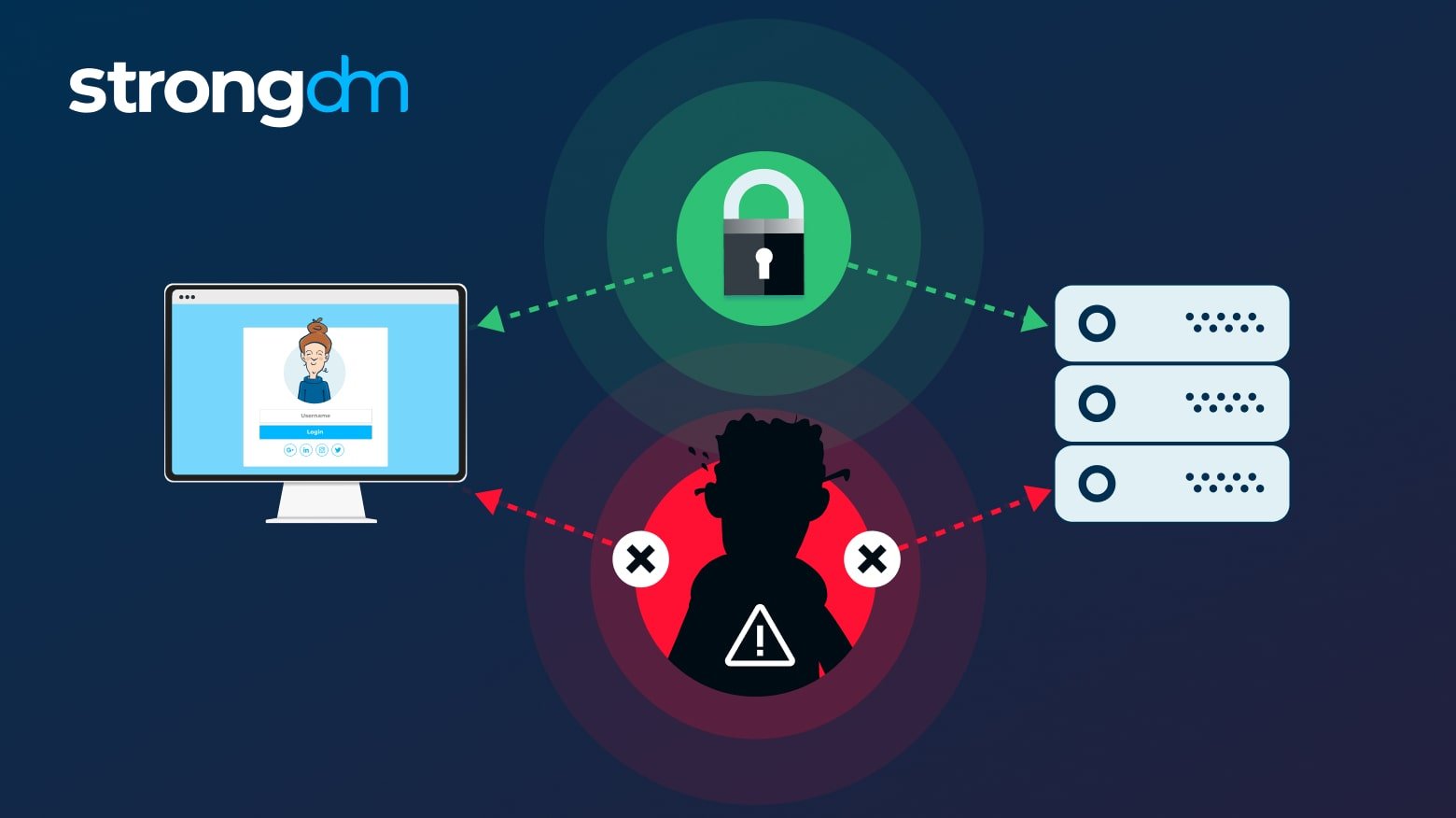
It’s difficult to detect MITM attacks, and attackers can target anyone online. Hackers can capture user credentials from customers by attacking sites or apps that require login authentication. They may also target businesses with sites or apps that store customer or financial information.Want to know how to prevent man-in-the-middle attacks? Follow these 10 proven strategies.

Cozy Bear specializes in targeting governments, diplomatic entities, non-governmental organizations (NGOs), and IT service providers, primarily in the U.S. and Europe. These state-sponsored groups aim to clandestinely gather strategic and sensitive information for Russia, maintaining prolonged access without raising suspicions.
The way that people work continues to evolve, and as a result, so do the ways that they must authenticate into their organization’s resources and systems. Where once you simply had to be hardwired into the local office network, now you must expand your perimeter to include remote and hybrid workforces, on-prem and cloud environments, and take into account a growing list of factors that impact how and where people access critical company resources.
Adherents to the Zero Trust security model, live according to a policy of “never trust, always verify.” It requires all devices and users to be authenticated, authorized, and regularly validated before being granted access, regardless of whether they are inside or outside an organization's network. But the catch is that authentication and authorization don’t just happen at the first touch.
In this blog, we’ll offer a blueprint for how to implement Zero Trust security effectively to help your organization initiate and manage access management for all your users, devices, and resources.
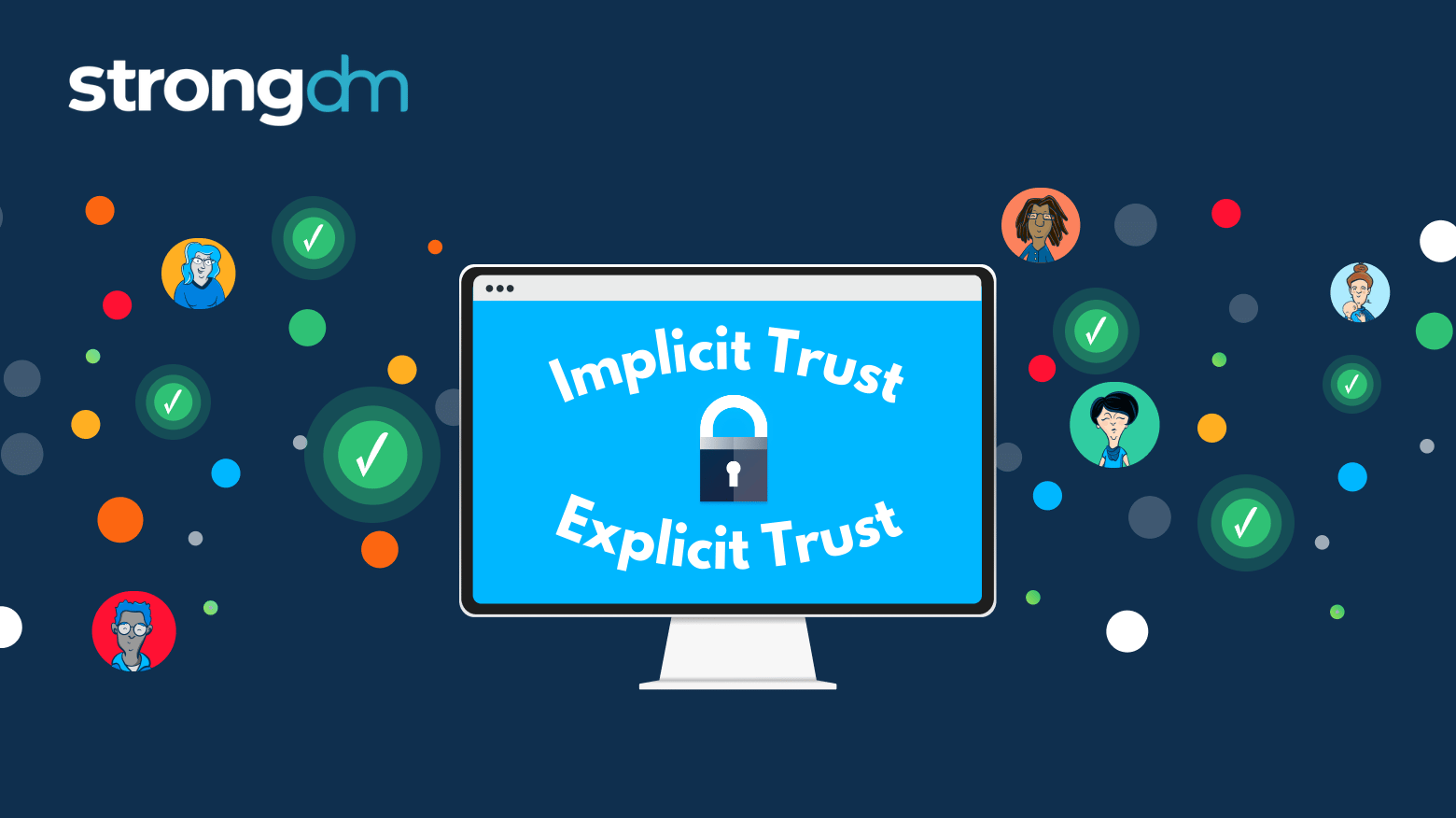
Trust is an essential cornerstone in access management. However, not all trust is created equal. When it comes to how you approach access, two types of trust stand out: implicit trust and explicit trust.
We are thrilled to announce an exciting new addition to the StrongDM Dynamic Access Management (DAM) platform: Continuous Zero Trust Authorization. This powerful capability can help organizations leap forward in the Zero Trust journey by enabling continuous, contextual, and granular authorization and control over resources and data

To embark on a successful Zero Trust journey, it's crucial to articulate and implement policies that align seamlessly with your business model. The Kipling Method serves as a guiding light in this endeavor. Let's delve into the six fundamental questions it poses.

In the 1990s, the TV series “The X-Files” made the phrase “Trust No One” popular. Now, with cybercrime increasing at an alarming rate, “trust no one” – or Zero Trust – is a phrase echoing through enterprises. In 2021, the average number of cyberattacks and data breaches increased by 15.1%. That same year, the U.S. government spent $8.64 billion of its $92.17 billion IT budget to combat cybercrime. It also released the CISA Zero Trust Maturity Model.

On the heels of President Joe Biden’s Executive Order (EO) 14028, the memo recommending Zero Trust Architecture to protect US government computers, the US Department of Defense (DoD) issued its own Department of Defense Zero Trust Strategy. Published in October 2022, the DoD Zero Trust Strategy addresses the rapid growth of cyber threats and the need for an enhanced cybersecurity framework.

