Context-Based Access Controls: Challenges, Importance & More


Written by
Fazila MalikLast updated on:
July 11, 2024Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Struggling to maintain a consistent security posture across your organization's diverse infrastructure? You're not alone. The challenges of policy enforcement in the era of on-premises systems, multiple cloud environments, and ever-changing compliance requirements can lead to security gaps and potential threats. But fear not, there's a solution on the horizon.
In this dynamic digital landscape, enforcing security policies is no small feat. However, the adoption of context-based access controls presents a transformative approach that dynamically adjusts security policies based on contextual parameters such as device posture and geo-location, significantly enhancing security and compliance. Join us as we explore the intricacies of context-based access controls, their benefits, and how solutions like the StrongDM empower organizations to navigate the complexities of modern infrastructure.
The Challenges of Policy Enforcement
Modern infrastructure, including on-premises systems, multiple cloud environments, and evolving compliance requirements, have complicated the task of maintaining a consistent security posture. Organizations are challenged to enforce security policies effectively across their entire infrastructure, which can lead to gaps in security and expose the organization to potential threats.
Additionally, there is no straightforward method to manage security policies across various platforms and services, resulting in inconsistencies and inefficiencies in policy administration. This fragmentation and lack of seamless enforcement lead to non-compliance with regulatory standards, which increases the risk of security breaches and exposes the organization to potential fines and penalties.
What Is a Context-Based Access Control?
Context-based access control is a dynamic and adaptive security approach that adjusts access permissions based on real-time factors like user location, device status, and behavior. Unlike traditional methods, it uses continuous risk assessments to make more precise security decisions. By narrowing access based on contextual parameters, it reduces the attack surface, enhances security, and streamlines policy administration, ensuring compliance in evolving environments.
Embracing Context-Based Access Controls
To address security access concerns, organizations must adopt a more dynamic and context-aware approach to access management. Context-based access controls offer a range of benefits that can significantly enhance security and compliance. By narrowing the aperture for access, these policies ensure that only the necessary resources are accessible to the right users under the right conditions, thereby reducing the overall attack surface.
Context-based policies enable organizations to quickly adapt to changing business environments and emerging security threats by considering the device posture, geo-location, and more to dynamically adjust controls and maintain optimal security.
This approach also reduces administrative overhead by providing a more streamlined and automated method for managing access, simplifying the process of defining and enforcing policies across diverse environments. By continuously evaluating the context and adjusting access accordingly, these policies ensure that organizations remain compliant and be confident with the controls in place.
Implementing Context-Based Policies with StrongDM
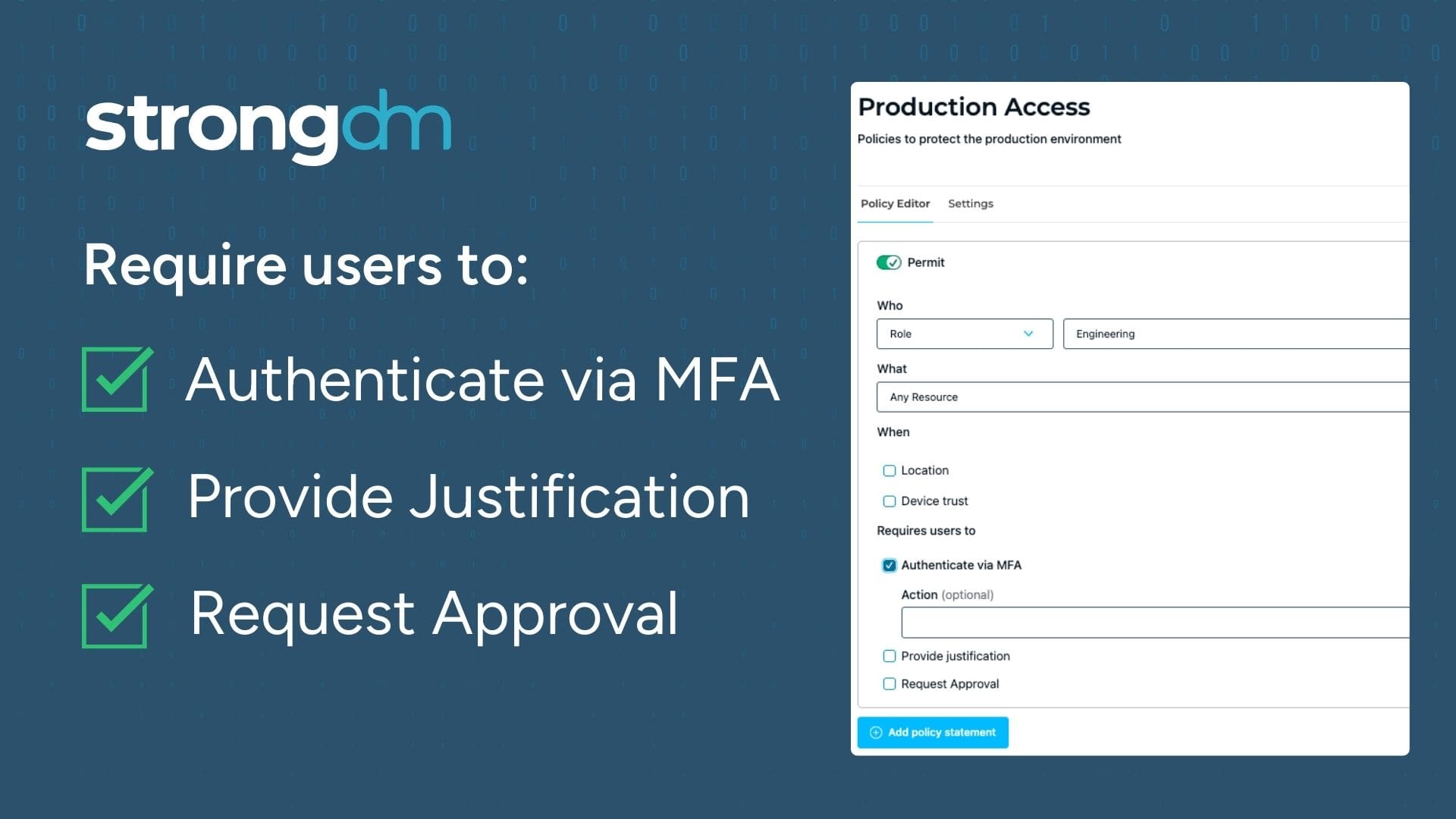
To operationalize context-based access controls, organizations need robust tools that can handle the complexity of modern infrastructures. StrongDM introduces the Strong Policy Engine, which allows customers to define context-aware policies against StrongDM resources. This enables:
- Enforcement with justification or MFA: Users can be required to provide justification or complete multi-factor authentication (MFA) to gain access to sensitive resources, ensuring that access is granted only when necessary and secure.
- Context-based signals for granular control: Access can be restricted based on context signals like device posture, geography, and IP. Coupled with continuous assessment, this further enhances security and considers the broader context of access requests.
See It in Action
Moving to Zero Trust Continuous Authorization
Implementing context-based access controls is a critical step towards achieving continuous authorization and embracing Zero Trust. By continuously evaluating the context of access requests and adjusting permissions accordingly, organizations can ensure that access is granted only when it is truly needed and under secure conditions. This proactive approach to security significantly reduces the risk of unauthorized access and data breaches, paving the way for a more secure and compliant future.
The adoption of context-based access is a necessity in the face of evolving security challenges. By leveraging tools like the Strong Policy Engine, organizations can effectively implement these controls, ensuring a more secure, compliant, and agile security posture in today's complex digital landscape.
Want to see StrongDM in action? Book a demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Fazila Malik, Sales Enablement Expert, as an accomplished Product Marketing Manager in the technology industry with over 5 years of experience, Fazila transitioned to a Sales Enablement leader position passionate about empowering go-to-market teams to excel in their roles. Throughout her career, she has worked with a range of technology products, including software applications and cloud-based solutions. Fazila is a member of the Product Marketing Alliance and an AWS Cloud Certified Practitioner. To contact Fazila, visit her on LinkedIn.
You May Also Like




