This tutorial will walk you step by step through how to manually set up SSH passwordless login to a Linux server. These commands should work on the majority of Linux distributions, and instructions are included for modern client machines of the macOS, Windows, and Linux varieties.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
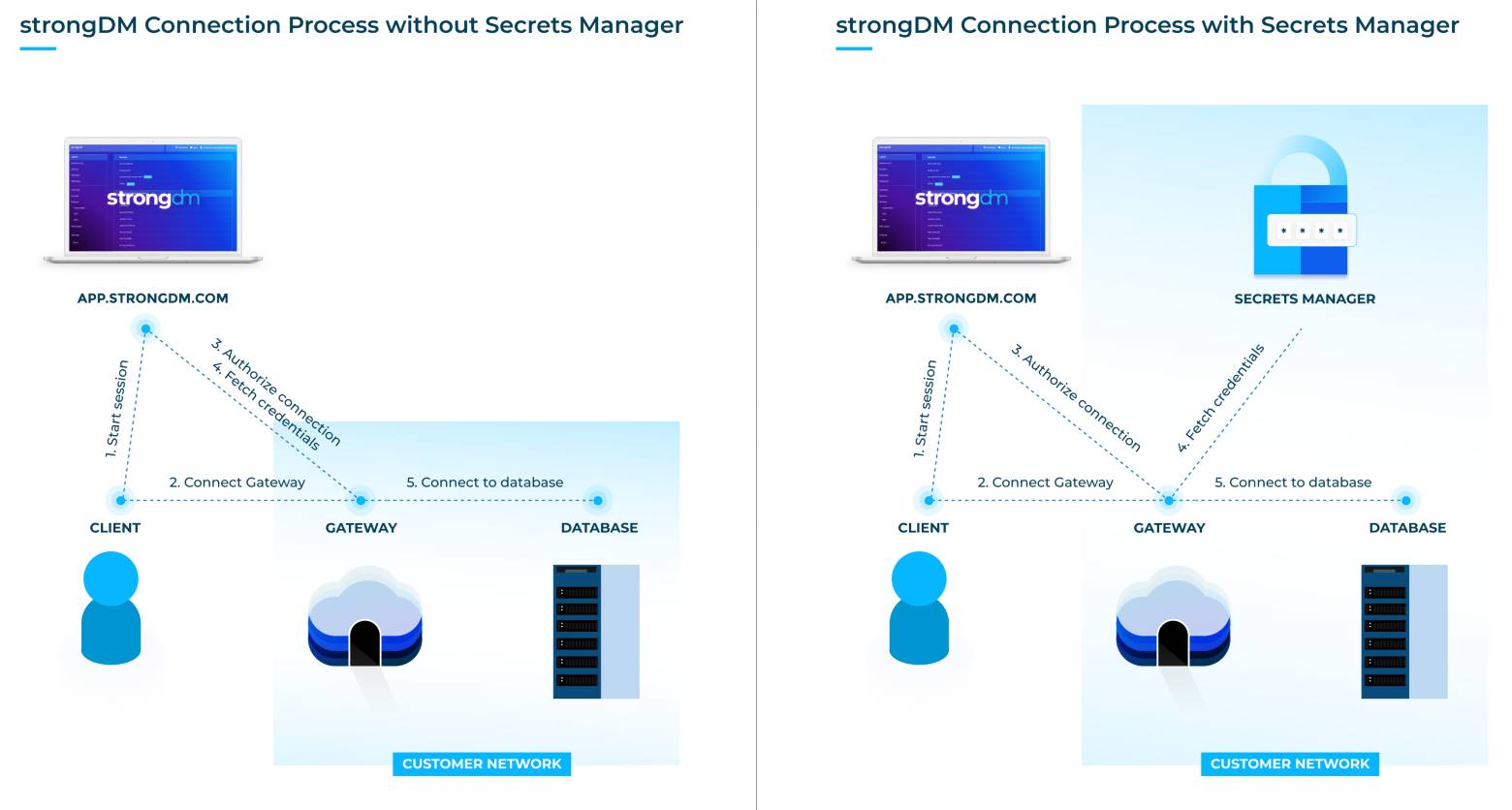
We’re pleased to announce public beta support for the use of third-party secrets managers with StrongDM to store your credentials. And the best part? There are zero changes to your workflow.
Infrastructure and DevOps administrators face significant barriers in managing Secure Shell (SSH) keys. In this article, we’ll explore the complexities of SSH key management. We’ll also show how to effectively authenticate users without having to manage SSH keys for individual users.

An explanation of role-based access control (RBAC) in Kubernetes, why it is hard to manage manually and practical strategies for simplifying RBAC in large-scale clusters.
Kubernetes authentication presents a unique challenge. While Kubernetes defines the concepts of both user accounts and service accounts natively, it doesn’t provide us with a single, built-in method for authenticating those accounts. Instead, we must choose from a variety of techniques involving third-party tools or resources to perform Kubernetes cluster authentication.