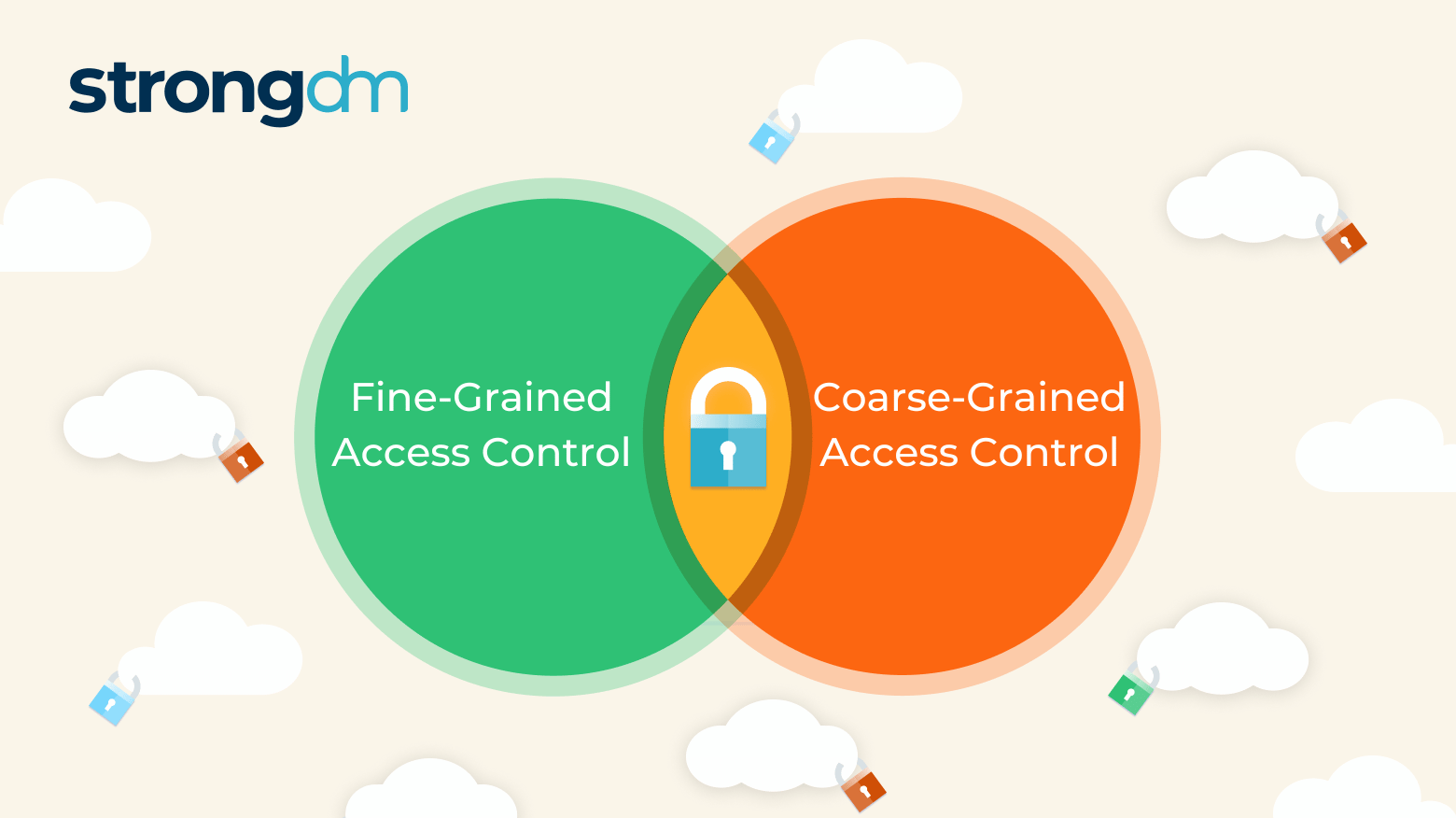
If credentials fall into the wrong hands, intruders may enter a network and launch a disastrous attack. In fact, 46% of cybersecurity incidents involve authentication credentials, according to the Verizon 2022 Data Breach Investigations Report. Organizations have two general ways to determine someone’s access rights once past initial authentication: Coarse-grained access control (CGAC), which relies on a single factor, and fine-grained access control (FGAC), which relies on multiple factors.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
If you’re Kuberntes admin and you’re not familiar with the tactics outlined in the MITRE ATT&CK framework, this blog post is for you. MITRE ATT&CK framework is an extensive knowledge base of tactics and techniques employed by bad actors that defensive security experts use to help defend their organizations against attack, and many times, used by their offensive security counterparts to test their weaknesses.
The CIS Kubernetes Benchmark is a set of prescriptive recommendations assembled to guide administrators to achieve good security hygiene and results in strength security outcomes for their Kubernetes environments.

I'm continuously shocked by how poorly the PAM industry has treated customers to date. Shame on CyberArk, Delinea, and all the rest of you for persisting with such predatory models. The business model is "squeeze the blood out of them, then squeeze harder." The deployment model is "you'll never ...
Historically, finding an infrastructure access management solution that is secure while still being easy to use has been extremely difficult. Too often, ease of use and complexity end up at odds. StrongDM addresses this challenge–and does so by integrating with your existing identity-based security initiatives. This blog details how StrongDM enables organizations to level up their access management approach to meet the requirements of Dynamic Access Management (DAM), bolster security, and

Both StrongDM and CyberArk are privileged access management solutions to provide secure access to backend infrastructure. While there are many similarities between the two solutions, there are also some key differences.

To embark on a successful Zero Trust journey, it's crucial to articulate and implement policies that align seamlessly with your business model. The Kipling Method serves as a guiding light in this endeavor. Let's delve into the six fundamental questions it poses.

Since Amazon Web Services first announced it in 2011, AWS IAM has evolved to become the gateway to the AWS Cloud. Organizations cannot interact with their cloud resources and its many services without it. Identity, not networking, is the real access boundary.

Standing Credentials. They’re a problem that seems to persist despite the latest security and access innovations. They’re also one of the main reasons that achieving zero trust is so hard–and enough of a problem that two strategic security initiatives have come to the forefront: Just-in-Time (JIT) access and Zero Standing Privileges (ZSP).
Identity and access management (IAM) and privileged access management (PAM) are critical security tools for modern organizations. However, they can sometimes bar users from accessing critical systems and services, potentially impacting production, customer experience, and cybersecurity. In urgent cases, a method of bypassing normal security controls to regain access—called “break glass”—is needed. In this post, we’ll walk you through the break-glass process—what it is, why it’s important, and

Want a secure and compliant AWS environment? Then you need to audit access. Keeping tabs on who has accessed what—as well as the whens, wheres, and whys—helps you spot suspicious activities and address them promptly. Without this kind of access control, your sensitive data could be exposed to malicious actors, putting you at risk of data breaches and subsequent regulatory nightmares or service interruptions.
Let’s face it. If you work with any type of technology, you know that all software, hardware, and networking gear can fail in weird and unexpected ways. That’s why it’s critical that your technology stack has no single point of failure in your environment. At StrongDM, that means having options in a “break glass” scenario. We firmly believe that this is a requirement for the responsible operation of modern technology. So here’s how we tackle it.

The Federal Financial Institutions Examination Council (FFIEC) places significant emphasis on user security controls and the mitigation of potential risks posed by privileged users. To comply with FFIEC guidelines and safeguard critical systems, strong access management measures are crucial.