Network Level Authentication (NLA) is a security feature of Microsoft’s Remote Desktop Protocol (RDP) that requires users to authenticate before establishing a remote session. By enforcing this pre-authentication step, NLA reduces the risk of unauthorized access, conserves server resources, and protects against attacks like credential interception and denial of service. While effective in securing RDP sessions, NLA is limited to a single protocol, lacks flexibility, and can add complexity in
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

Enterprises seek ways to effectively address the needs of dynamic, always-evolving cloud infrastructures, and StrongDM has developed a platform that is designed with built-in capabilities to support continuous compliance in AWS environments.
![IP Whitelisting: Meaning, Alternatives & More [2026 Guide]](https://discover.strongdm.com/hubfs/ip-whitelisting.jpg)
IP whitelisting is a security strategy that restricts access to a network/system to a specified list of trusted IP addresses. This approach ensures that only individuals using the approved addresses can access certain resources.

Discover how StrongDM's Zero Trust PAM and fine-grained authorization secure cloud data plane access and mitigate shadow access risks without hindering productivity.

Learn why Just-in-Time (JIT) access is essential for Zero Trust security in AWS environments. Discover how StrongDM's JIT access enhances security, optimizes workflows, and ensures compliance with Zero Trust principles.
Let’s talk about the unsung heroes of your on-premises infrastructure: network devices. These are the routers, switches, and firewalls that everyone forgets about…and takes for granted—until something breaks. And when one of those somethings breaks, it leads to some pretty bad stuff. If your network goes down, that’s bad, bad, bad for business. But if those devices lack the necessary security, well, that can leave you exposed in an incredibly dangerous way.
Zero Trust cloud security is a cybersecurity model that operates on the principle that no user, device, system, or action should be trusted by default — even if it's inside your organization’s own network. This approach minimizes the risk of breaches and other cyber threats by limiting access to sensitive information and resources based on user roles, device security posture, and contextual factors.
Protecting sensitive patient data in healthcare isn't just a priority—it's a legal and ethical obligation. However, one of the most overlooked security gaps that healthcare organizations face is the practice of password sharing among employees. This seemingly harmless habit can quickly lead to unauthorized access and serious data breaches, putting both the organization and patients at risk. While often seen as a convenient shortcut, password sharing undermines the security of protected health

Privileged Identity Management (PIM) is a complex cybersecurity approach. But it’s the only proven method you can use to lock down access and protect your precious resources. It can help you keep cybercriminals out and ensure that even your trusted users can’t accidentally—or intentionally—jeopardize your system’s security.
Zero Trust Data Protection isn't just the best way to safeguard your data — given today's advanced threat landscape, it's the only way. Assuming inherent trust just because an access request is inside your network is just asking for a breach. By implementing the latest tactics in authentication, network segmentation, encryption, access controls, and continuous monitoring, ZT data security takes the opposite approach.
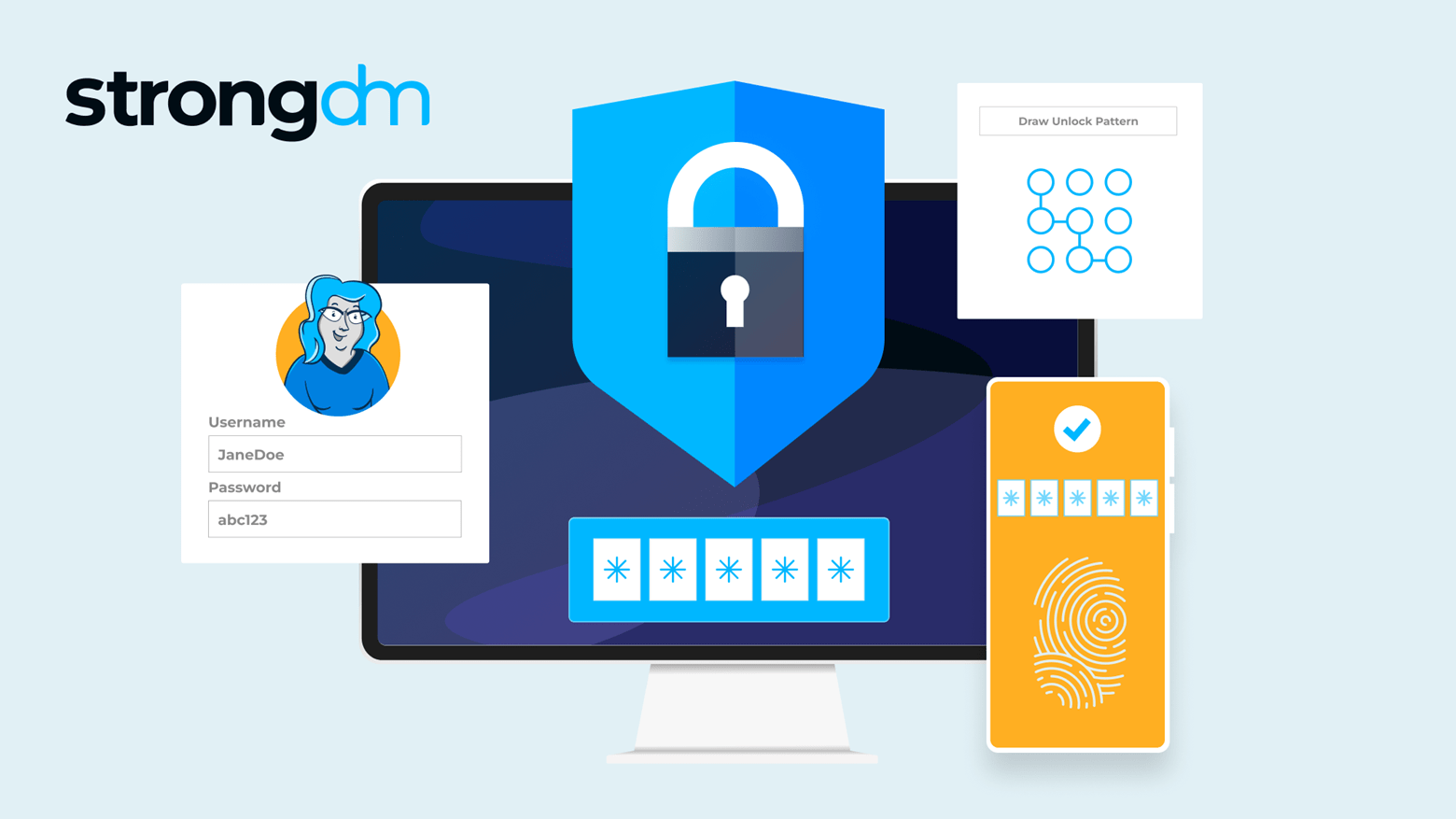
With so many advanced cyber attackers lurking on the threat landscape, a simple password is no longer enough to safeguard your sensitive data. There are many reasons to adopt MFA for your business. It supplements your security by requiring additional information from users upon their access requests—and it significantly reduces your risk of incurring a breach. Several multi-factor authentication methods are available, with varying strengths and weaknesses. Be sure to compare the differences
As enterprises continue to modernize their IT environments, the need for a more advanced and adaptable approach to database authorization becomes increasingly apparent. Traditional models, with their reliance on static roles and broad permissions, are no longer sufficient to meet the demands of decentralized, dynamic infrastructures. StrongDM addresses this gap by offering a solution that emphasizes fine-grained, policy-based action control, enabling organizations to manage database access with
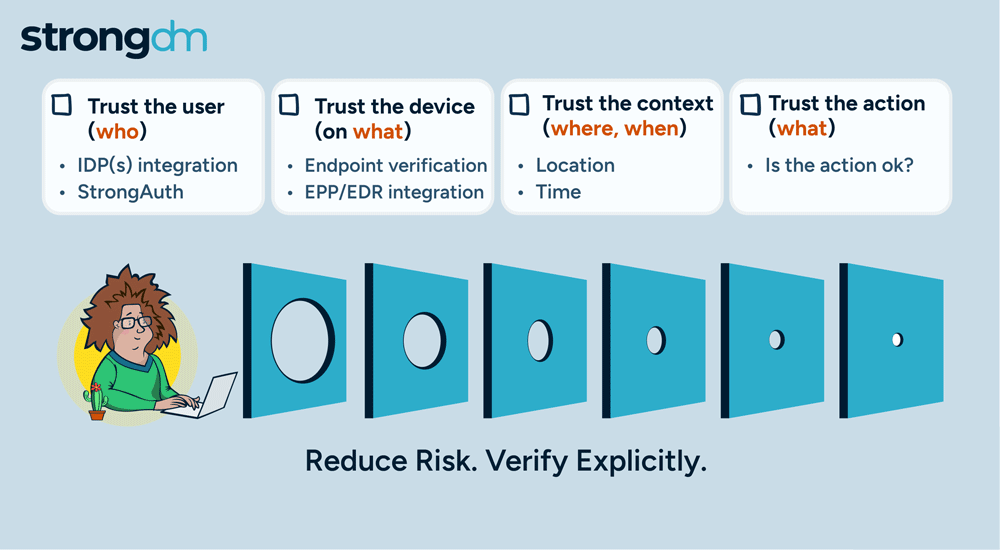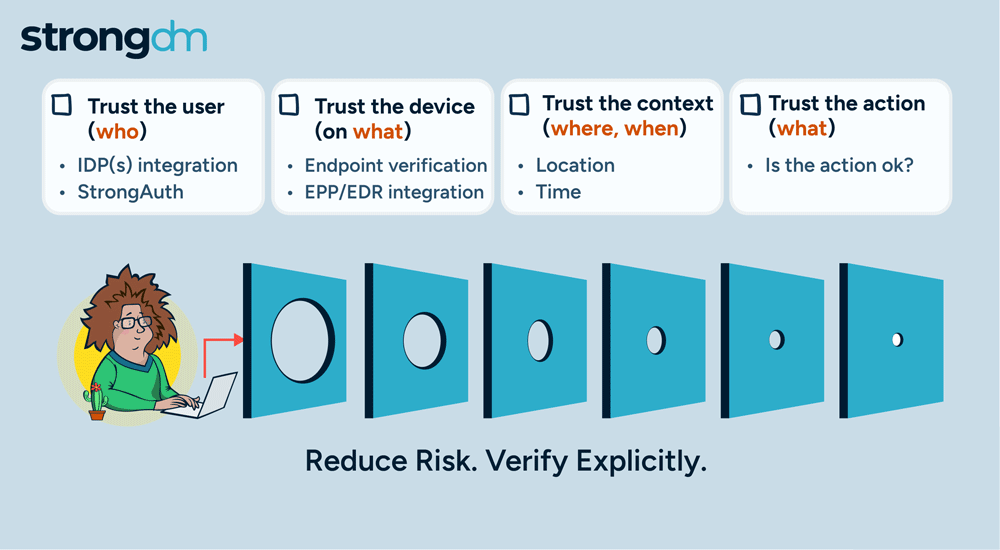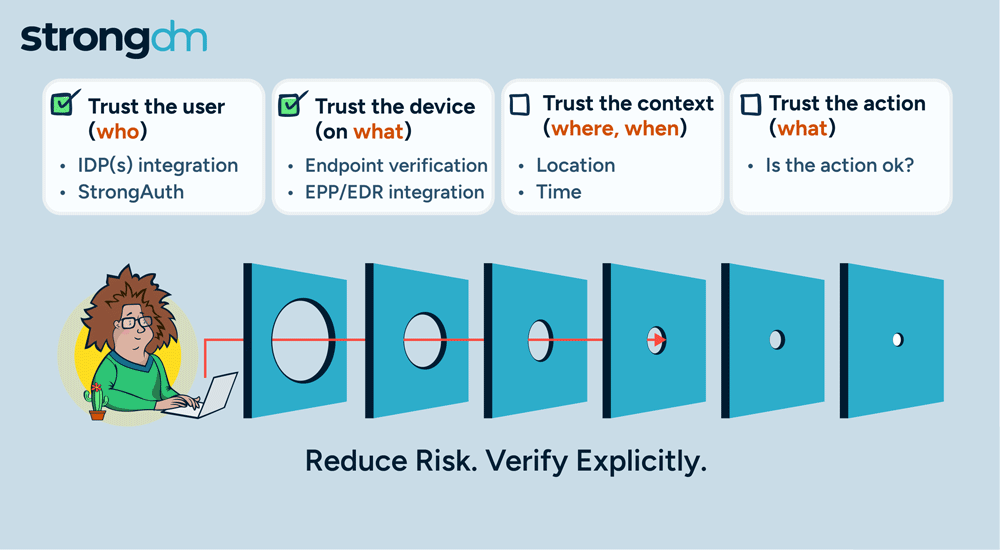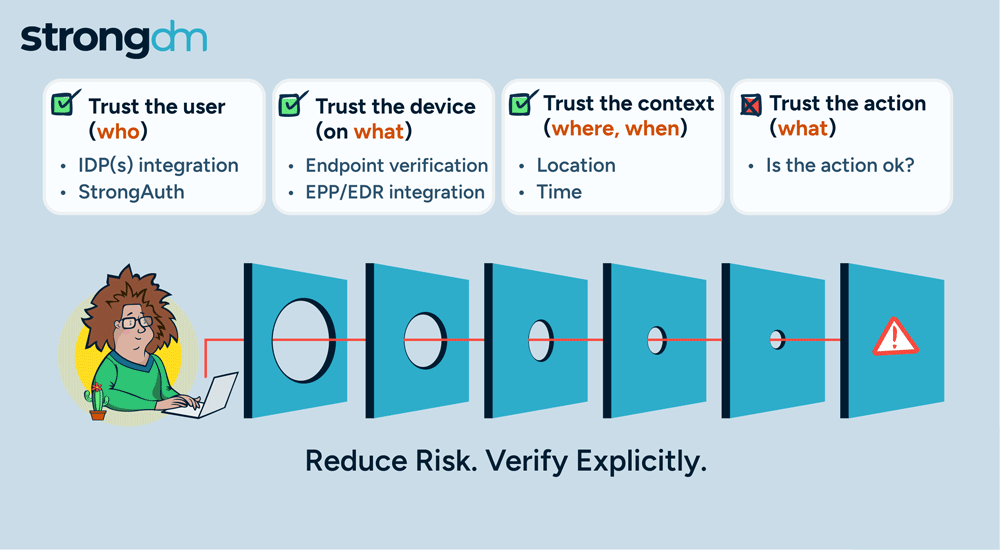
Access is no longer the primary challenge in enterprise security; it's the actions of users that are most aligned with managing risk. By focusing on how actions are authorized, StrongDM is giving customers a more effective approach to enterprise security. Our policy-based action control ensures that, in addition to access, every user action is scrutinized, delivering a higher level of security tailored to meet the complex demands of modern enterprises.
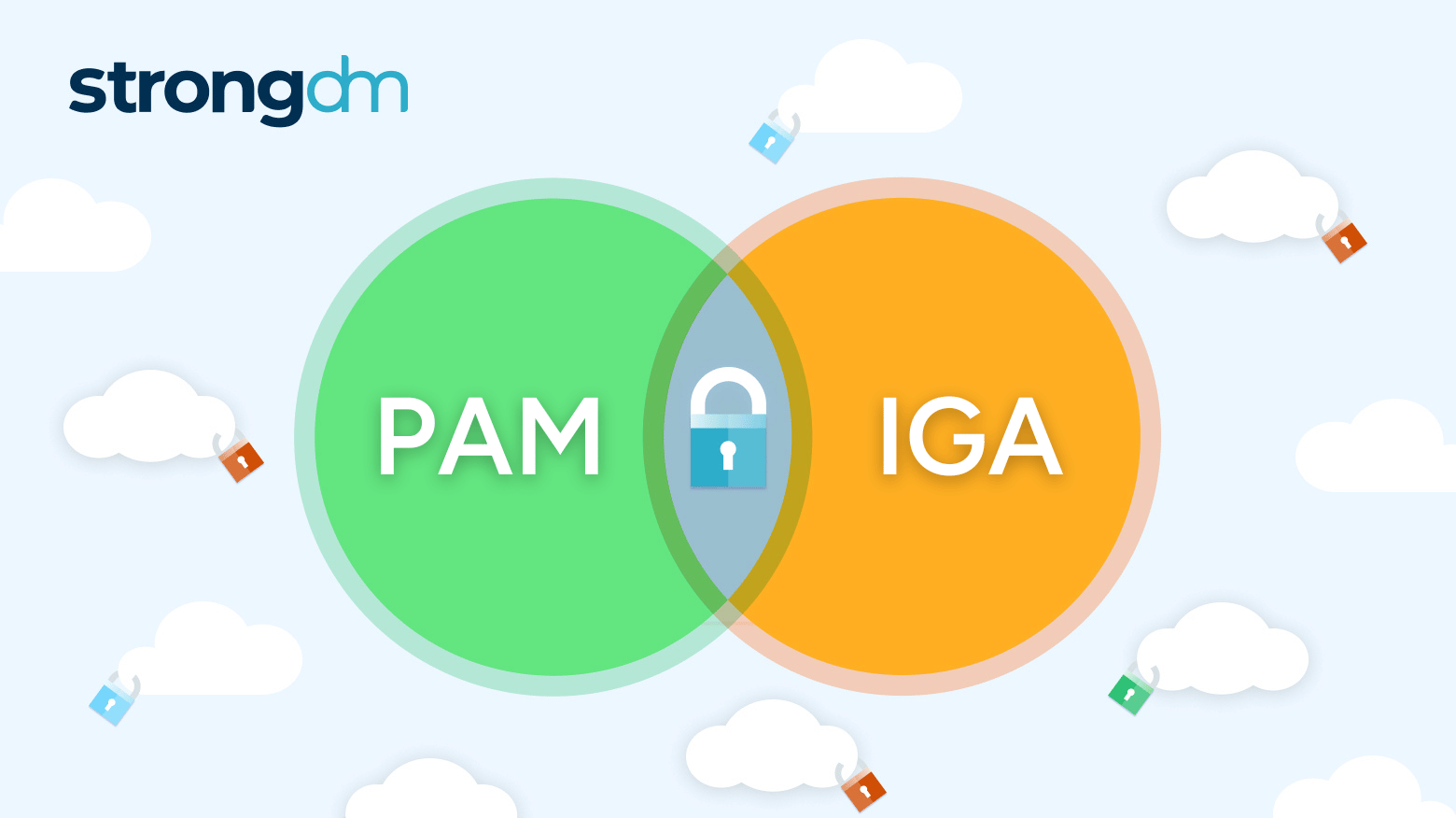
IGA (Identity Governance and Administration) manages user identities and access across the organization, ensuring proper access and compliance. PAM (Privileged Access Management) secures privileged accounts with elevated permissions by using measures like credential vaulting and session monitoring to prevent misuse. While IGA handles overall user access, PAM adds security for the most sensitive accounts.

