Today there are numerous technologies and solutions to help organizations create an active onboarding experience for employees. But what do the employee onboarding statistics say about the process?
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
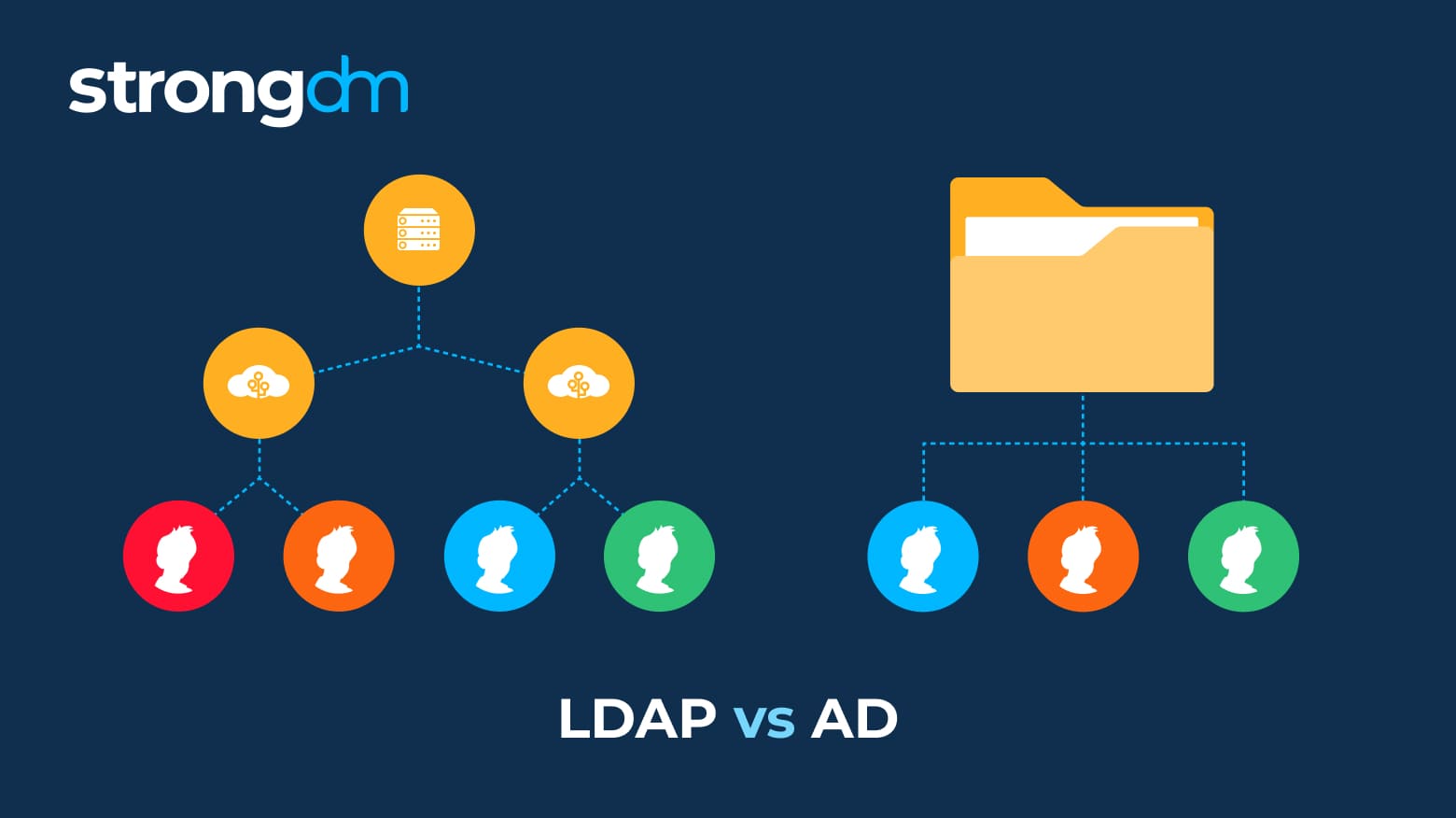
Struggling to understand the difference between Active Directory and LDAP? Don't worry, we’ll make it simple. These are just two among many methods that can provide secure user authentication and authorization. The information in this article will help you decide if LDAP or Active Directory is right for your organization. Robust security and a seamless user experience are attainable, and you can have both!

In this article, we’ll take a deep dive into attack vectors. You’ll learn what they are, the most common types, how they’re used, and why hackers continually use them to exploit vulnerabilities. By the end of this article, you'll have a thorough understanding of the fifteen most common types of attack vectors and what you can do to prevent your organization from falling victim to them.

In this article, we’ll compare the top IAM solutions: StrongDM, CyberArk Identity, Okta, BeyondTrust, ManageEngine AD360, Saviynt, and Twingate. We’ll explore what business needs identity and access management solutions address, and review the pros and cons of each. By the end of this article, you’ll know how to choose the right IAM solution for your organization.

Cloud data protection is an increasingly popular element in an organization’s security strategy. In this article, we’ll explore what cloud data protection is, why it’s important, and the best practices to follow when migrating to the cloud. By the end of this article, you’ll understand the benefits and challenges of adopting a data security strategy for cloud environments.

In this article, we will look at three important types of access control in security. You’ll learn about the different types of access control, how they work, and their pros and cons. By the end of this article, you’ll understand what type of access control will work best for your organization and meet your security needs.

Enterprise cloud security is quickly becoming a cybersecurity best practice for large organizations. In this article, we’ll explore what enterprise cloud security is, why it’s important, and the challenges organizations experience with enterprise cloud adoption. You’ll learn about common cloud security issues and the best practices you should adopt to avoid those issues. By the end of this article, you’ll feel confident choosing the right enterprise cloud solution for your organization
Enterprises often have thousands of users to manage, and therefore unique requirements for their enterprise identity and access management software solutions. In this article, you’ll learn what enterprise IAM is and what to expect in a successful enterprise-wide IAM software implementation. By the end of this article, you’ll know the benefits and challenges of introducing enterprise IAM solutions in your organization.
In this article, we’ll review the leading privileged access management (PAM) solutions on the market. We’ll explore the pros and cons of the top privileged access management vendors so you can easily compare the best PAM solutions. By the end of this article, you’ll feel confident choosing the right privileged access management solution for your organization.

In this article, we look at the top risks and security issues in cloud computing. You'll learn about specific cloud security threats and cloud storage security issues, as well as strategies for managing cloud security effectively. By the end of this article, readers will fully understand the top security issues related to using cloud-based file management tools and services.

In this article, we'll cover the Authentication, Authorization, and Accounting (AAA) framework for cybersecurity, the meaning of each AAA component, and the benefits of using it for granular access control. You'll learn about different AAA protocols and how they relate to Identity and Access Management (IAM). By the end of this article, you'll fully understand AAA networking and how the model assists with network security and monitoring.

In this article, we take a deep dive into Remote Browser Isolation (RBI), its history, and how it works. You'll learn about the common challenges associated with remote browser isolation and its importance in securing users from internet-based cyber threats. By the end of this article, you'll gain a complete understanding of remote browser isolation, as well as how it can be used to complement a Zero Trust framework.

In this article, we will explain how User and Entity Behavior Analytics (UEBA) helps modern organizations defend against sophisticated, hard-to-detect cybersecurity attacks. You’ll learn how UEBA compares to other security monitoring tools, the top benefits of UEBA, and important challenges to consider. By the end of this article, you’ll know the basic UEBA meaning and the most important factors to help you decide if a UEBA tool is right for your organization.