Latest blog posts from Andrew

As cyber threats have increased in recent years, more organizations are turning to cyber insurance to mitigate their financial risks. In this article, we’ll review cyber insurance basics, including what cybersecurity insurance is, how it works, what it covers, and what it costs. By the end, you will understand the different types of cyber insurance, the benefits of coverage, and how cyber insurance fits into a comprehensive security strategy.
HITRUST and HIPAA often go hand-in-hand when talking about security compliance. But what are they, and how do they compare? In this article, we’ll review HITRUST vs. HIPAA, including their differences, similarities, and advantages, and we’ll explain how and when to use them in compliance efforts.

ManageEngine’s PAM360 gives system administrators a centralized way to manage and audit user and privileged accounts within network resources. However, teams that need to manage secure access to Kubernetes environments or enforce password policies within their privileged access management (PAM) system may want to consider other options. This blog post will cover ManageEngine PAM 360 and some solid alternatives, along with the pros and cons of each.
In this article, we'll cover machine identities and address the importance and challenges in machine identity management. You'll gain a complete understanding of how machine identity management works and see the concept in action through real-world examples. By the end of this article, you'll be able to answer in-depth: what is machine identity management?
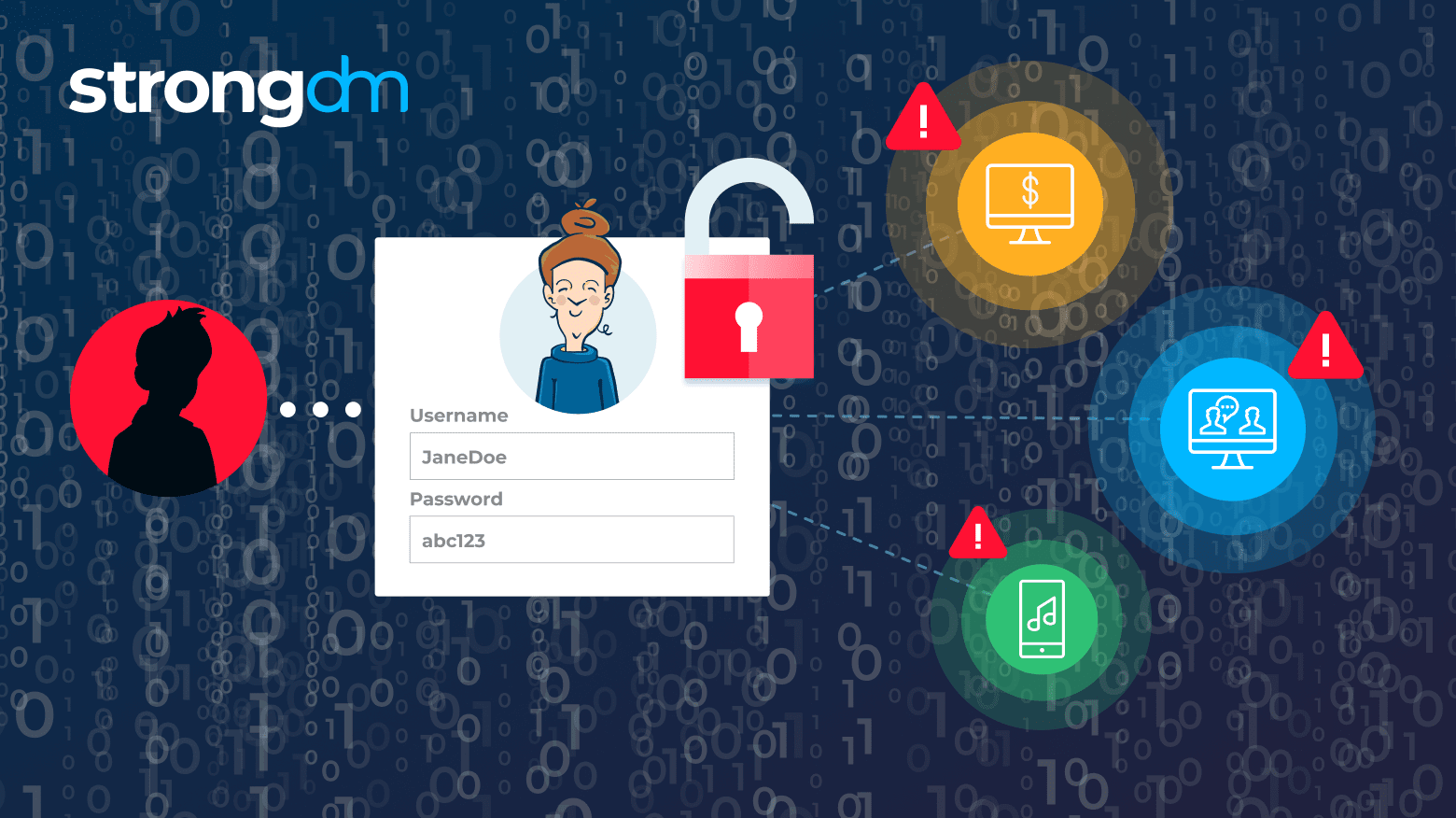
In this article, we’ll define credential stuffing and explain the risks that credential stuffing attacks pose to organizations and customers. We’ll cover recent examples of credential stuffing attacks and discuss how to detect and prevent them. By the end of the article, you should understand the full scope of credential stuffing, including how to protect your customers’ and employees’ account credentials with the right tools.
In this article, we will take a big-picture look at the Payment Card Industry (PCI) Data Security Standards (DSS). You’ll learn what is required to be PCI compliant and what’s involved in each of the 12 PCI DSS requirements. You’ll also find a handy PCI Compliance Checklist for easy reference, including new PCI compliance requirements.
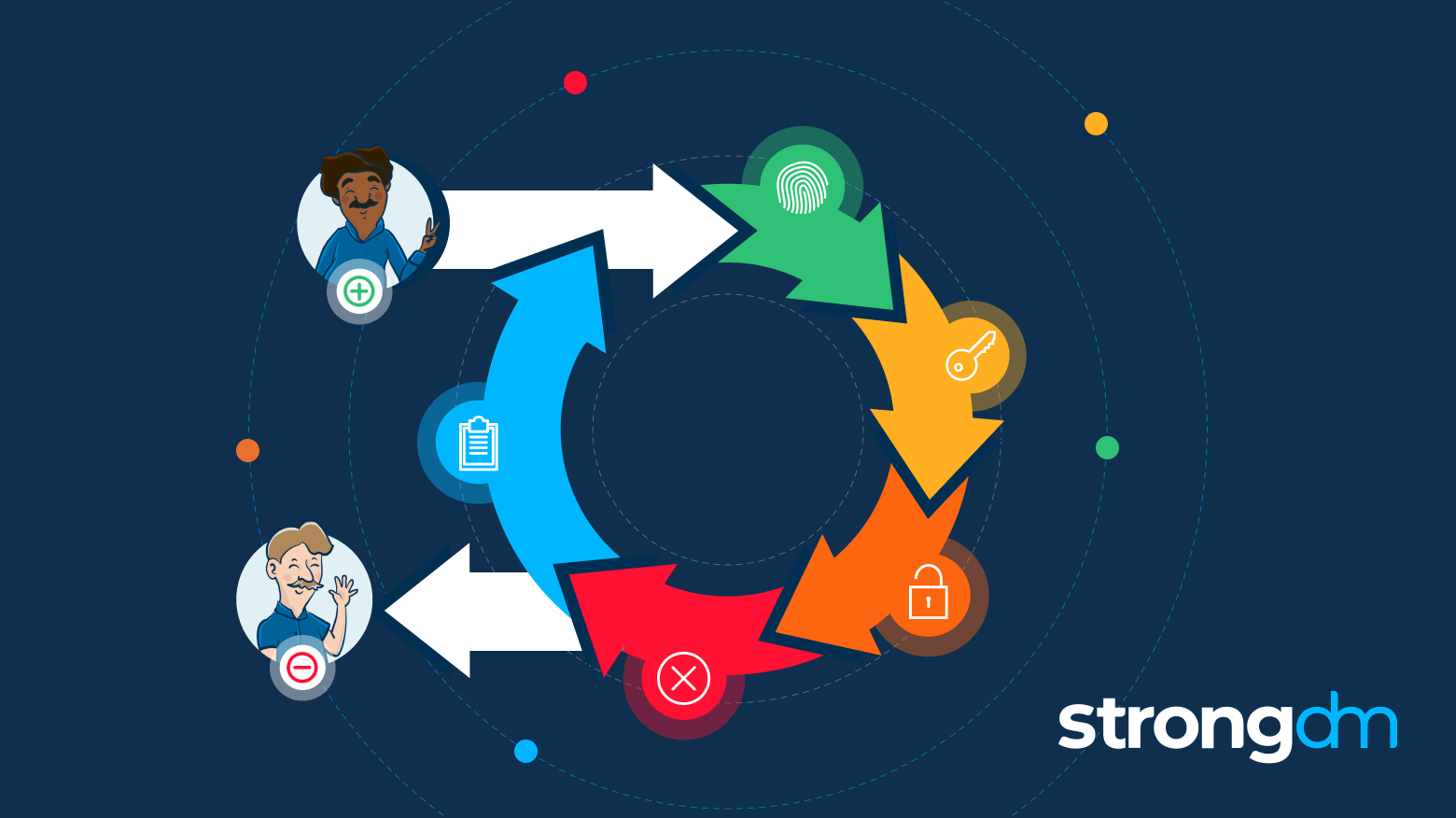
In this article, we’ll take a broad look at identity governance and administration (IGA) and examine how it differs from other IT risk mitigation topics. You’ll get insight into the history, benefits, and features of IGA and learn how to start planning an IGA implementation of your own.
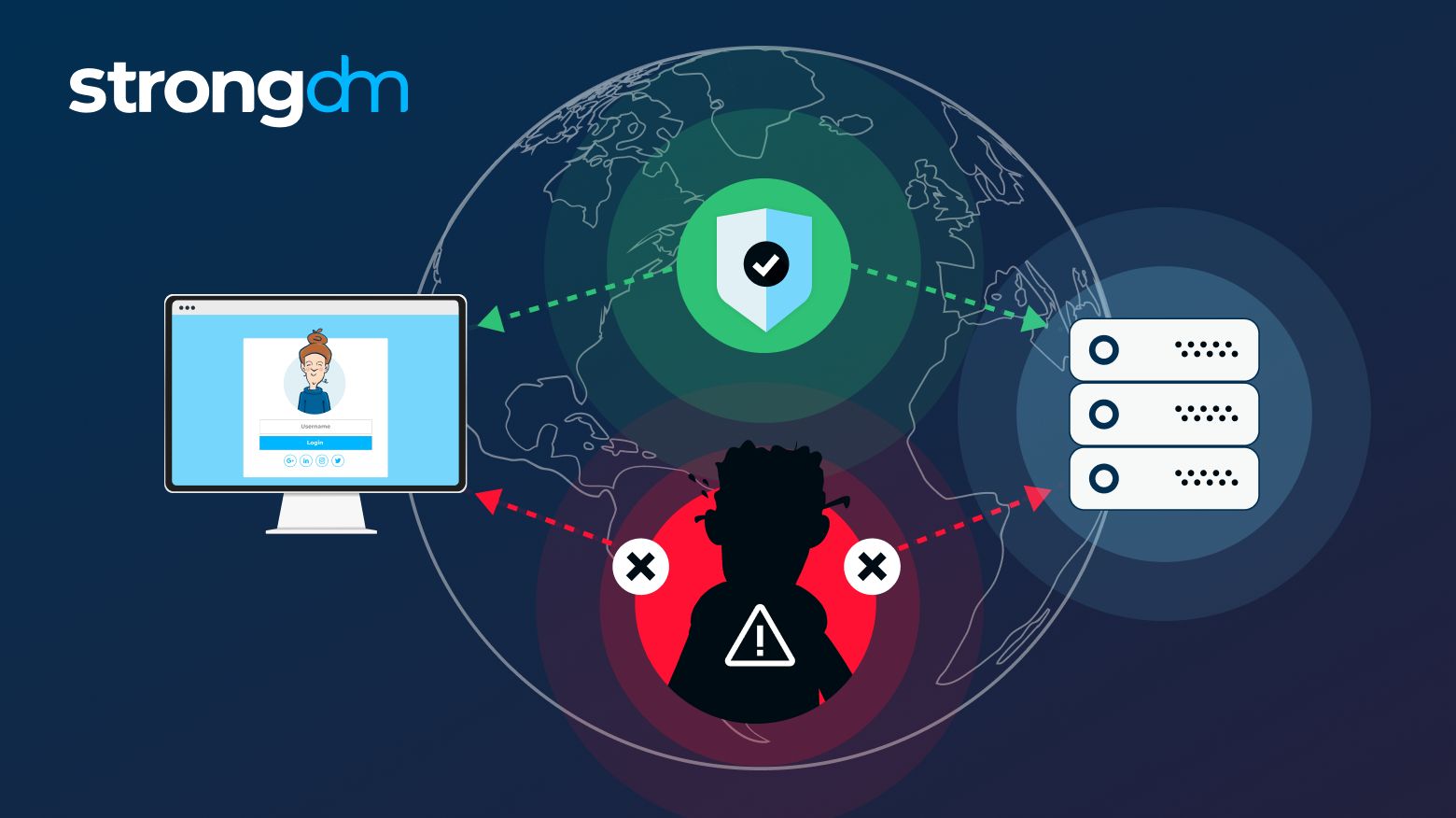
In this article, we go over the man-in-the-middle attack definition and discuss the different types of these attacks. We'll take a deep dive into the dangers of man-in-the-middle attacks and address some examples. By the end of this article, you'll have a complete understanding of how a man-in-the-middle attack works and how to detect and prevent one.
In this article, we’ll take a look at insider threats in cyber security and the dangers they pose. You’ll learn the insider threat definition, who the insiders are, the types of insider threats to be aware of, and how to detect threats. By the end of this article, you’ll have a clearer understanding of the entire insider threat ecosystem and the best practices you can use to protect your organization, data, and systems.
In this article, we’ll take a comprehensive look at brute force attacks: what they are, how they work, and the different shapes they can take. You'll learn about popular tools utilized by hackers and examples of brute force attacks in action. By the end of this article, you'll be able to understand critical prevention measures for brute force attacks.
Advanced threat protection is a type of cybersecurity dedicated to preventing pre-planned cyberattacks, such as malware or phishing. ATP combines cloud, file sharing, email, network, and endpoint security.
SASE is a cloud-based network security solution, whereas SD-WAN is a network virtualization solution. SASE can be delivered as a service, making it more scalable and resilient than SD-WAN. Additionally, SASE offers more comprehensive security features than SD-WAN, including Zero Trust security and built-in protection against Distributed Denial-of-Service (DDoS) attacks.

In this article, we’ll take a big-picture look at how SASE and CASB solutions fit into the enterprise security landscape. We'll explore the key differences between SASE and CASB and explain how each tool helps ensure enterprise security. You will gain an understanding of how SASE and CASB solutions compare and which might be suitable for your organization.

In this article, we’ll compare two Privileged Access Management (PAM) solutions: CyberArk vs. Thycotic, with a closer look at what they are, how they work, and which will best fit your organization. We’ll explore product summaries, use cases, pros and cons, PAM features, and pricing to that by the end of this article, you’ll have a clearer understanding of how these PAM tools work and be able to choose the one that’s right for you.