
Latest blog posts from John

In this article, we’ll walk you through the ISO 27001 checklist you’ll use en route to your cybersecurity certification. From assigning roles to implementing controls, assessing risks, and documenting your processes for future audits, you can use the ISO 27001 compliance checklist to ensure you’re on the right track for your official audit.
In this article, we’ll look at the overall price tag for one International Standards Organization certification (ISO 27001), along with some of the factors that impact costs and why they vary across organizations. You’ll learn about different ISO 27001 certification costs, from the audit, with its ISO 27001 exam cost, to implementation and maintenance. By the end of this article, you’ll get a sense of the factors involved in ISO 27001 certification and be able to compare quotes to decide your

SOC 2 and ISO 27001 both provide companies with strategic frameworks and standards to measure their security controls and systems against. But what’s the difference between SOC 2 vs. ISO 27001? In this article, we’ll provide an ISO 27001 and SOC 2 comparison, including what they are, what they have in common, which one is right for you, and how you can use these certifications to improve your overall cybersecurity posture.

In this article, we will take a deep dive into WebAuthn and some of its associated authentication concepts. We’ll go over the history of WebAuthn and help you better understand the benefits and challenges of using this standard of secure authentication. By the end of this WebAuthn guide, you’ll be able to fully define the concept and grasp how to incorporate it into your organization's security program and web applications.
In this article, we will take a big-picture look at FIDO2 and how it applies to passwordless authentication. You’ll learn about the origins of FIDO2, its advantages and disadvantages, the differences between FIDO2, FIDO, and WebAuthn, and how UAF and U2F differ. By the end of this article, you’ll have a clear understanding of how FIDO2 works, what problems it solves, whether you need FIDO2 certification, and what that certification entails.
In this article, we dive into passwordless authentication and some of the implications of using this verification method. You’ll learn about examples of passwordless authentication solutions, whether they're secure, and how it's different from multi-factor authentication (MFA). After reading this article, you’ll have a full understanding on how passwordless authentication works and how it can address today’s cybersecurity and access management challenges.
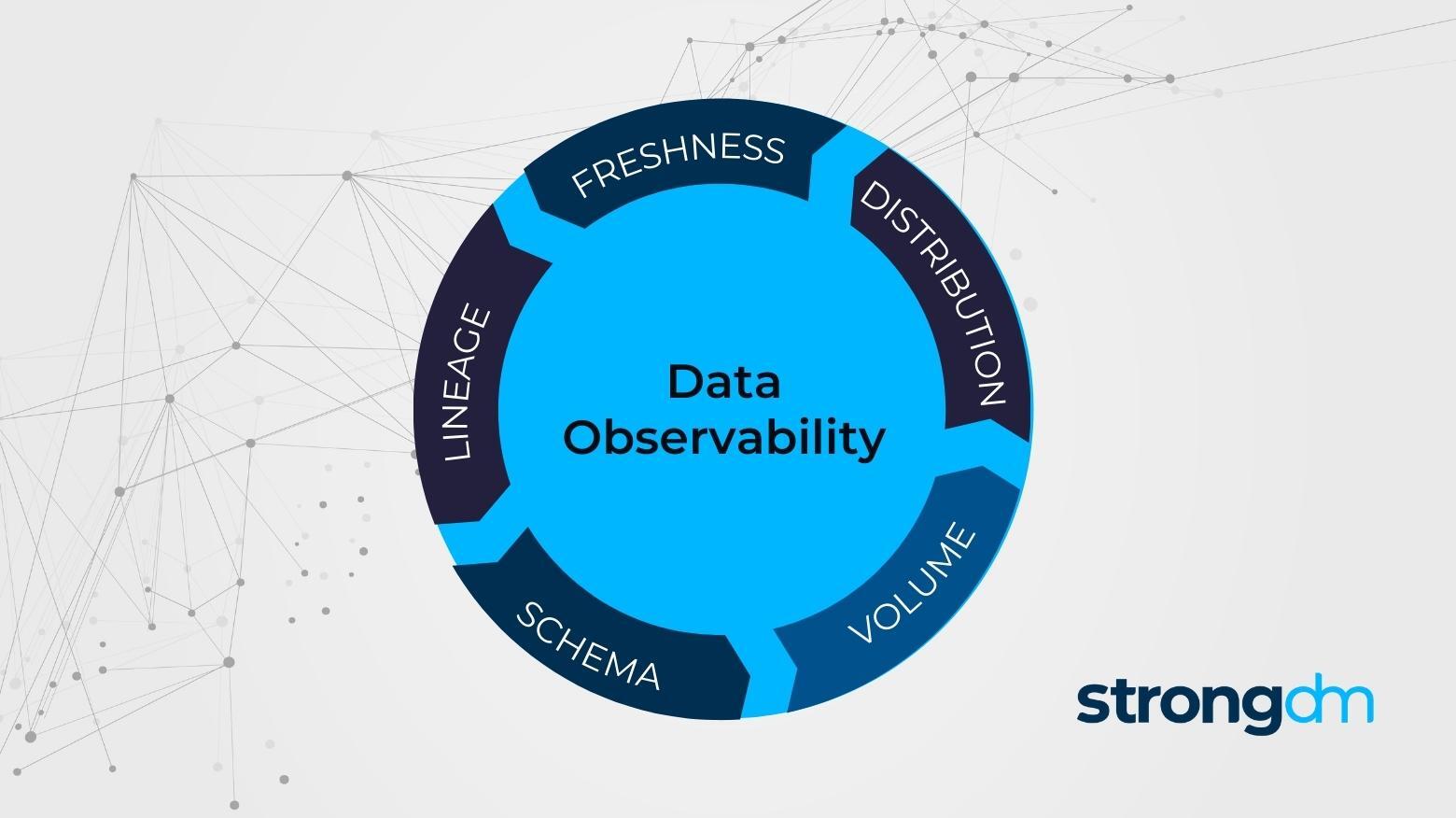
Data observability can help companies understand, monitor, and manage their data across the full tech stack. In this article, you’ll learn what data observability is, the differences between data observability, monitoring, and data quality, and what information you can track with data observability. By the end of this article, you’ll discover how to implement data observability and find the right data observability tools for your organization.

In this article, we’ll focus on the three pillars of observability. You’ll learn about the definitions, strengths, and limitations of each pillar. By the end of this article, you’ll know about their individual contributions and typical real-world challenges, tying them together for an overall view of your system.

In this article, you’ll learn the difference between AWS roles vs. policies and see examples of each. By the end of this article, you’ll have a clear understanding of what distinguishes an AWS role from a policy, in addition to understanding the difference between IAM roles, users, and groups.
Observability and monitoring are often used interchangeably, but there are key differences you should know between these two IT terms and the tools that enable them. In this article, we’ll explore the relationship and differences between observability vs. monitoring. Plus, you’ll learn about what makes observability and monitoring different from telemetry and application performance monitoring (APM).

In this article, you’ll learn about how GCP IAM works and the different types of roles that can be delegated to users as well as when those roles are most appropriate in the GCP environment. By the end of this article, you’ll have a clear understanding of the pros and cons of each different role type as well as their limitations.
In this article, we'll list eleven Identity and Access Management (IAM) best practices and describe each one of them in detail. You'll also learn how to make these best practices standard in your organization.

In this article, we will take a comprehensive look at software-defined networking (SDN). You’ll learn what it is, how it works, and what its benefits and disadvantages are. You’ll also learn how SDN compares to and works with other types of networks and get answers to common questions.

Data breaches are a perpetual risk for modern organizations — and the wider your attack surface, the higher your organization’s risk of a breach. In this article, we will take a high-level look at what your attack surface is, what vectors and endpoints may be at risk, and how to analyze your attack surface.

