
Written by
John MartinezLast updated on:
September 29, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
AWS Cognito is a user authentication service that lets you add access control to your web and mobile apps. Cognito manages sign-up, sign-in, password changes, token refresh, data synchronization, and updates to user account attributes. The service is initially free for AWS users, and the pricing model scales as your user base grows. But Amazon Cognito may not be the best fit for all situations. If you're looking to centralize and secure access to databases, servers, and Kubernetes, you may find other tools to meet your needs. This article will take you through some popular AWS Cognito alternatives, with a brief look at the strengths and weaknesses of each. But first, here are some features you may want to consider.
AWS Cognito Overview
Brief product summary
Unlike AWS Identity and Access Management, which manages access to AWS services and resources, AWS Cognito allows developers to add user authentication and access control to web and mobile apps. With Cognito, your users can sign in using social identity providers (like Facebook, Google, and Amazon) or external identity providers (via SAML 2.0). The service generates ephemeral security credentials to access backend resources behind Amazon API Gateway.
Cognito adds security and convenience for your users, with data synchronization across devices and platforms. It is easy to integrate with your app and provides access management for your AWS resources, a customizable user interface for user sign-in, and security features like multi-factor authentication (MFA).
Use cases
- Allow app users to federate through a third-party identity provider (IdP).
- Provide access to server-side resources for your web or mobile app.
- Enable app users to access your API.
Pluses
- Easy integration with other AWS services.
- Secures passwords.
- Simple to set up.
- Supports MFA.
- Allows sign-in with social identity providers.
Minuses
- Lacks rich customization.
- Difficult to reconfigure.
- Limited integration with non-AWS services.
- Audit logging requires additional tools.
1. StrongDM
Brief product summary
StrongDM is a control plane to manage and monitor access to databases, servers, and Kubernetes. Their zero trust model means instead of distributing access across a combination of VPN, individual database credentials, and SSH keys, StrongDM unifies user management in your existing SSO (Google, Onelogin, Duo, Okta, SAML, etc...) and keeps the underlying credentials hidden. Neither credentials nor keys are accessible by end users. Because StrongDM deconstructs every protocol, it also logs all database queries, complete SSH and RDP sessions, and kubectl activity.
Use cases
- Faster onboarding- no need to provision database credentials, ssh keys, VPN passwords for each new hire.
- Secure off-boarding- suspend SSO access once to revoke all database, server access.
- Automatically adopt security best practices- least privilege, just-in-time access, audit trail.
- Comprehensive observability and visibility- log every permission change, database query, ssh & kubectl command.
- Vendor privileged access management-connect third-party vendors to resources with project-based access that automatically expires.
- Security and compliance teams-simplify HIPAA, SOC 2, SOX, ISO 27001 compliance certification.
- Modern Cloud PAM solution-built to support a variety of cloud networks, including public, private, multi-cloud, and hybrid.
Pluses
- Easy deployment - self-healing mesh network of proxies.
- No change to workflow- use any SQL client, CLI, or desktop BI tool.
- Standardize logs across any database type, Linux or Windows server, and Kubernetes.
- Graphical client for Windows and MacOS.
- See and replay all activity with session recordings.
- Manage via a user-friendly web browser interface.
- Simple, straightforward pricing.
Minuses
- Requires continual access to StrongDM API for access to managed resources.
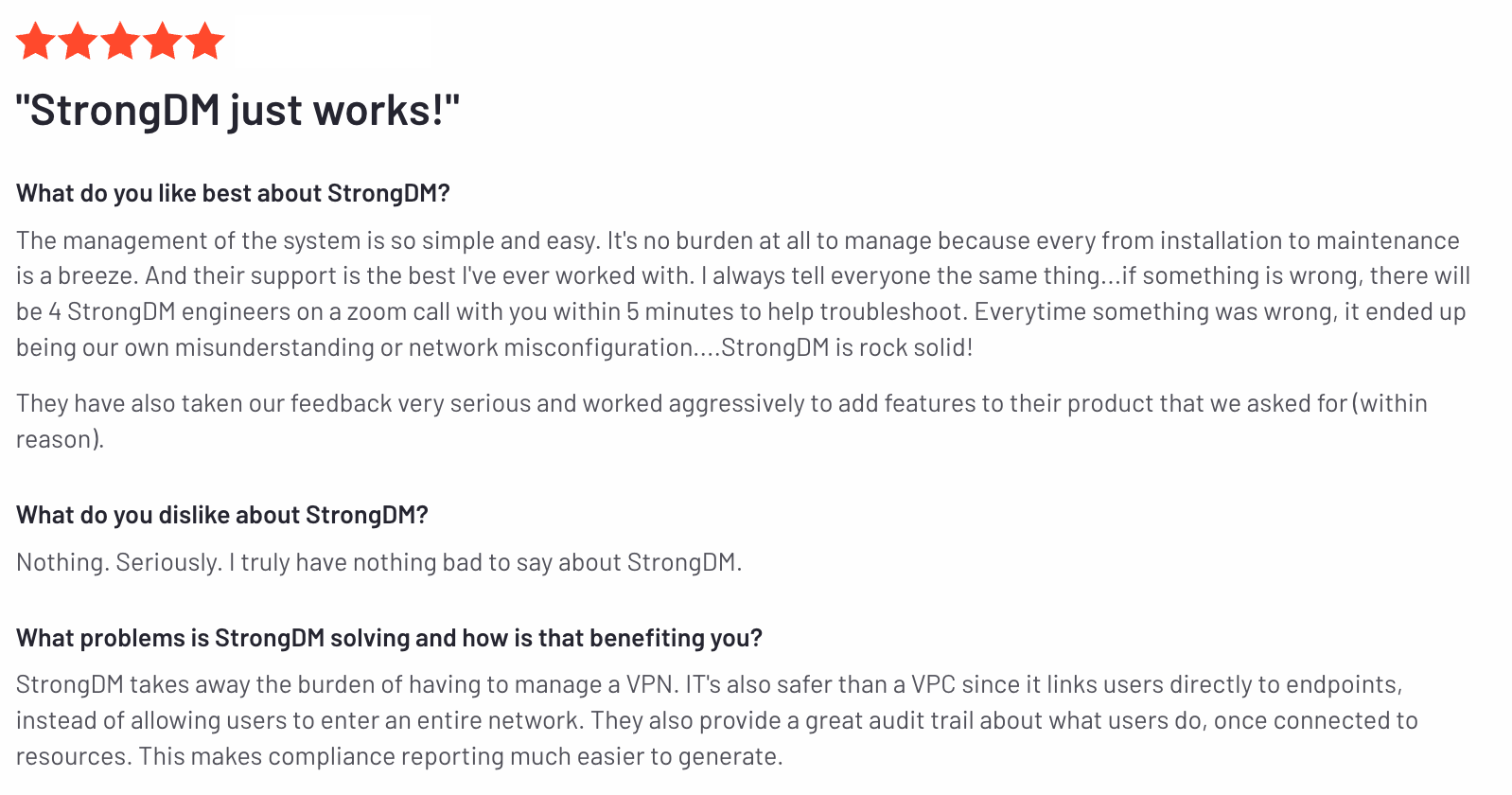
StrongDM’s G2 Reviews
- 4.8 / 5 stars
Read all of StrongDM’s G2 reviews here.
Pricing Information
StrongDM offers simple pricing, including support for all resource types.
Users have the option to sign up for a free 14-day trial.
2. Google Cloud IAP
Brief product summary
Google’s Identity-Aware Proxy aims to increase security, allowing admins to establish and enforce access-control policies. The service simplifies access for cloud administrators and remote workers, eliminating the need for a VPN.
IAP provides a zero-trust access model for GCP resources such as Google Compute Engine and Google Kubernetes Engine (GKE) instances, allowing access only to users with the correct identity and access management (IAM) role. Additionally, you can use TCP forwarding to control access to SSH and RDP. With proper configuration, IAP will also authenticate to apps on other clouds and on-premises.
Use cases
- Authentication for web applications and cloud resources.
- Access control for SSH and RDP.
Pluses
- SSH access available.
- RDP access available.
- Automatically creates an OAuth 2.0 client ID and secret.
- Easy to integrate with other GCP services.
Minuses
- Requires additional configuration to use with multi-cloud apps.
- Doesn't protect against activity within a project.
- Limited third-party integration.
- Initial setup is complex.
3. Okta Customer Identity
Brief product summary
Okta Customer Identity provides identity management for app developers. With Okta, developers can simplify signups, logins, and password management. Users synchronize authentication across all devices and platforms with a single global ID. Whether you’re building a new app, integrating multiple apps, or modernizing a platform, Okta aims to provide security, scalability, and ease for customer identity.
Use cases
- Add authentication to your web and mobile app.
- Synchronize customer identity across multiple devices.
Pluses
- Includes a wide range of pre-built app integrations.
- Offers social login and OIDC support.
- Synchronizes customer identity across multiple devices.
- Secures APIs from malicious attacks.
Minuses
- Integrations can be difficult to implement.
- Lacks access management for backend infrastructure.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like



