Why We Built Comply | Free SOC 2 Policy Templates


Written by
Justin McCarthyLast updated on:
October 17, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
SOC 2 can be a daunting process. Policies are subjective; auditors avoid providing much guidance; advice on the internet is incomplete or vague. We decided to create Comply, an open-source collection of SOC 2 policy templates that include best practices. We hope it reduces the stress of SOC 2 and points fellow startups in the right direction.
SOC 2 involves every team in the company -- including many which don’t report to you. You need to inventory your existing tools/infrastructure, research best practices, define policies and procedures for your teams, build consensus, and ultimately persuade every team to adopt them. The process is inevitably accompanied by acute time pressure: a major Q4 deal, an impending IPO, or a life-changing partnership that depends on successfully completing your audit.
Our team recently went through another SOC2 audit and decided this time around, we'd like to share some of our lessons learned (see "How to Stay SOC 2 Compliant"). We compiled these lessons in Comply and open-sourced all our work so fellow startups could easily adopt our work. I've been a part of security and compliance for other regimes as well (PCI, HIPAA, GDPR), and one thing all of these systems share is an unabiding love for documents!
As a developer, writing 80 pages of policies in Word docs reminded me just how much I love Git. We wanted policy documentation that felt more like code documentation and the workflow to be as convenient as the DevOps automation we use every day. In short, we wanted compliance to feel more like software.
We've published Comply (on Github) to establish a free, open-source foundation for a successful SOC 2 program.
Introducing Comply
Comply approaches SOC 2 from a developer’s perspective. Download a pre-authored library of 24 policies, edit directly in markdown, track versions with Github, assign compliance tasks through Jira and monitor progress in a unified dashboard. It's 100% free and open source.
SOC 2 Templates
Before starting SOC 2, we had a solid grasp of security, but security and compliance are two very different things. We found ourselves wishing for a baseline set of practices that definitively addressed SOC 2 without requiring an army of headcount dedicated to ongoing operations.
We compiled these best practices into our policy templates so that you can incorporate industry standards for today’s SaaS businesses simply by executing `comply init`. No need to be intimidated by a blank page or waste any time writing original policies from scratch. The templates have been reviewed and enhanced by security and compliance experts from Splunk, Yext, InVision, Braze, and others. Decades of experience, months of research, and writing are included with every Comply template.
Software
The Comply tool itself addresses two large and related topics:
- Document management
- Process workflow
Collaboration is a solved problem for programmers, and wherever possible, we rely on the tools and techniques of software development to enable your compliance program itself to feel like software.
Document Management
Our documentation pipeline produces professional, LaTeX-formatted PDFs (thanks, Pandoc!) from simple, legible markdown documents. Because documents are plaintext and stored in your existing source control system, diffs, merges, and revision history are implicit. Even in cases where policies are updated by less technical team members, using modern interfaces such as Github’s web UI with native markdown preview provides a WYSIWYG experience while retaining everything else we love about source control.
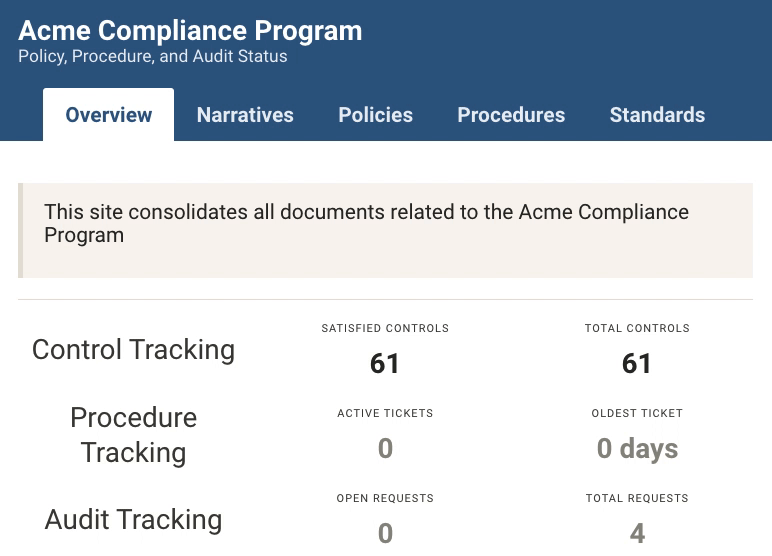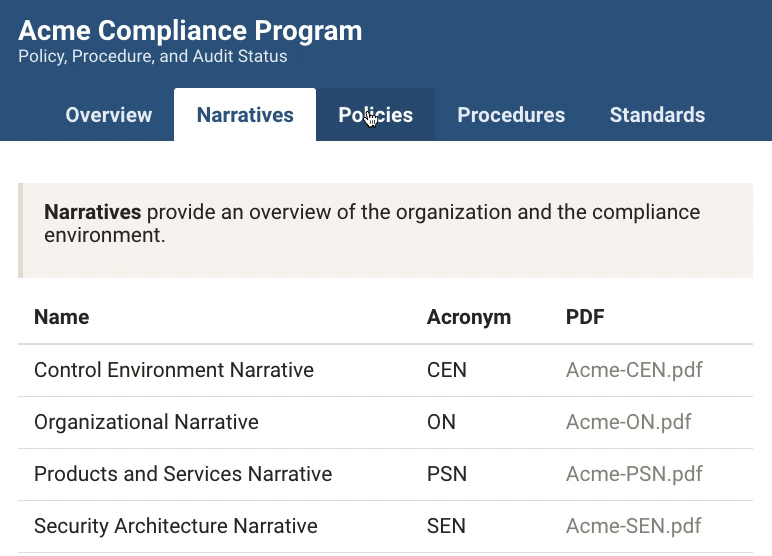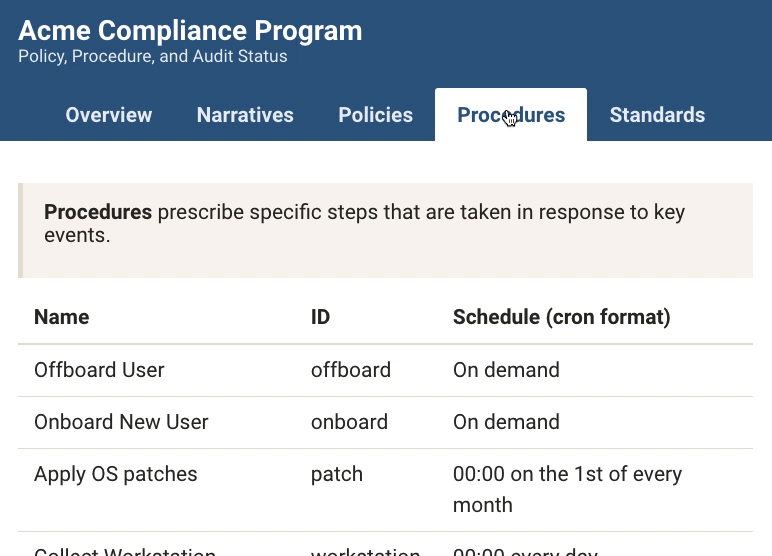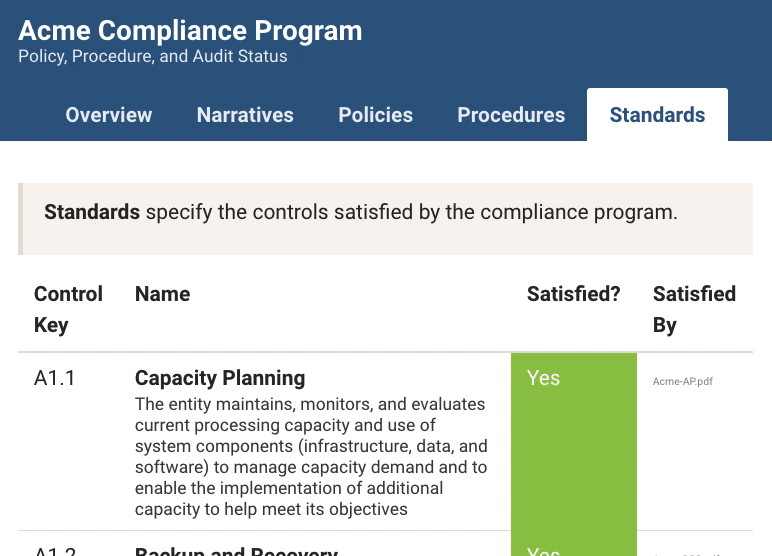
Each document also has a structured component, declaring exactly which aspects of the compliance standard it satisfies. Documents are cross-indexed with the compliance standard, allowing you to quickly point your auditor to the relevant document.
Process Workflow
Comply makes task management easy by integrating with your ticketing system (we’re launching with support for Github and JIRA). Assign a ticket to a collaborator and track the status in the Comply dashboard to instantly review which tasks are completed, in progress, or remain in the queue. Specify periodic tasks (policy reviews, OS patching, penetration tests, etc) and Comply will ensure a new ticket is created at the appropriate time. Like everything else in Comply, these schedules are plaintext (cron format) and are themselves committed to source control.
SOC 2 Companion Course
Because the templates still need to be tailored to your business, we’ve provided some context and commentary on each in the form of a SOC 2 video course. We’ve digested the key concepts, common mistakes, and best practices.
We highly recommend you check it out as you kick off your policy authoring process. The course also provides a detailed walkthrough of the use of the Comply software, as well as some additional background on the origins of SOC 2, the role of the AICPA, and what you can expect come audit time.
Our Goal
We hope Comply helps you avoid much of the frustration we felt going through SOC2. The entire suite of tools and templates is open-sourced, so if you think of ways to improve, jump in and contribute!
We look forward to hearing your feedback and questions -- drop us a note in the official Comply Slack!
To learn more about how StrongDM helps companies with SOC 2 compliance, make sure to check out our SOC 2 Compliance Use Case.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Justin McCarthy, Co-founder / CTO, originally developed empathy for Operations as a founding and pager-carrying member of many operations and data teams. As an Executive, he has led Engineering and Product in high-throughput and high-stakes e-Commerce, financial, and AI products. Justin is the original author of StrongDM's core protocol-aware proxy technology. To contact Justin, visit him on Twitter.
You May Also Like




