DevOps Security Explained: Challenges, Best Practices & More

Written by
Philip GallagherLast updated on:
October 31, 2024Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
DevOps teams are in no way exempt from the dangers of the Digital Age. With the number of cyber threats growing all the time, increased alertness from clients and customers, and unsympathetic compliance regulations to which companies are responsible, it is ludicrous for organizations to overlook the potential dangers within DevOps pipelines.
So why does it continue to happen? What are the biggest security challenges facing DevOps, and how can practitioners overcome them? In this article, we're going to define what DevOps security is and examine how DevOps engineers can work to guarantee security across their cultures.
What Is DevOps Security?
DevOps security (DevSecOps) is an approach to cybersecurity that focuses on application development and development operations (DevOps). It combines three phrases:
- Development
- Operations
- Security
The goal of DevOps security is to remove barriers between an organization’s software development and its IT operations. Namely, it calls for speed and intense, fast communication and collaboration. It is essentially a philosophy that covers developers’ code and its subsequent need to work (and grow) properly with the organization’s employees and customers.
The core of the DevOps security philosophy is continuous deployment. Development and IT teams work closely and rapidly to add to and fix software. This means, for example, adding new features and troubleshooting bugs so that they can be continuously released in fast cycles without causing disruptions. It enables teams, other employees, and customers to continue interacting with software without interruption.
In short, business operations are continuous and don’t face unnecessary interruptions.
Why is DevOps Security Needed?
Security is one of the critical areas of concern for developers. Developers often rely heavily on Software Development Kits (SDKs) or at least on other frameworks or individual programs. But third-party code can represent a serious security vulnerability in these cases. As far as a developer is concerned, their organization doesn’t necessarily know whether they’ve been addressed before.
DevOps Security Solutions
If an organization’s developers and IT staff work together closely, new software can be released quickly with less room for error. Each side can assess their colleagues’ needs more accurately when changes are planned and applied.
Brief History of DevOps Security
The landscape of cybersecurity has also evolved since DevOps was first introduced. Factors like cloud computing were nowhere near as prominent back then as they are now but have since introduced a wave of new potential issues to factor in at the policy level.
In short, not only did DevOps continue evolving over time, but so did the landscape and character of security. With this in mind, one could say that a greater focus on security in DevOps is part of a natural evolutionary process. The safety and reliability of code have become more of a core selling feature, and previous methods, such as leaving security checks until later on, have simply ceased to be viable.
With this natural transition also came the realization that DevOps pipelines offered an excellent opportunity to efficiently guarantee the security of code. Applying the approach's attitude to automation and evolution to security was a no-brainer, as was applying more rigorous checks to the development stage to avoid more serious issues later on. This led to the creation of systems such as 'Rugged DevOps' and, later, 'DevSecOps'.
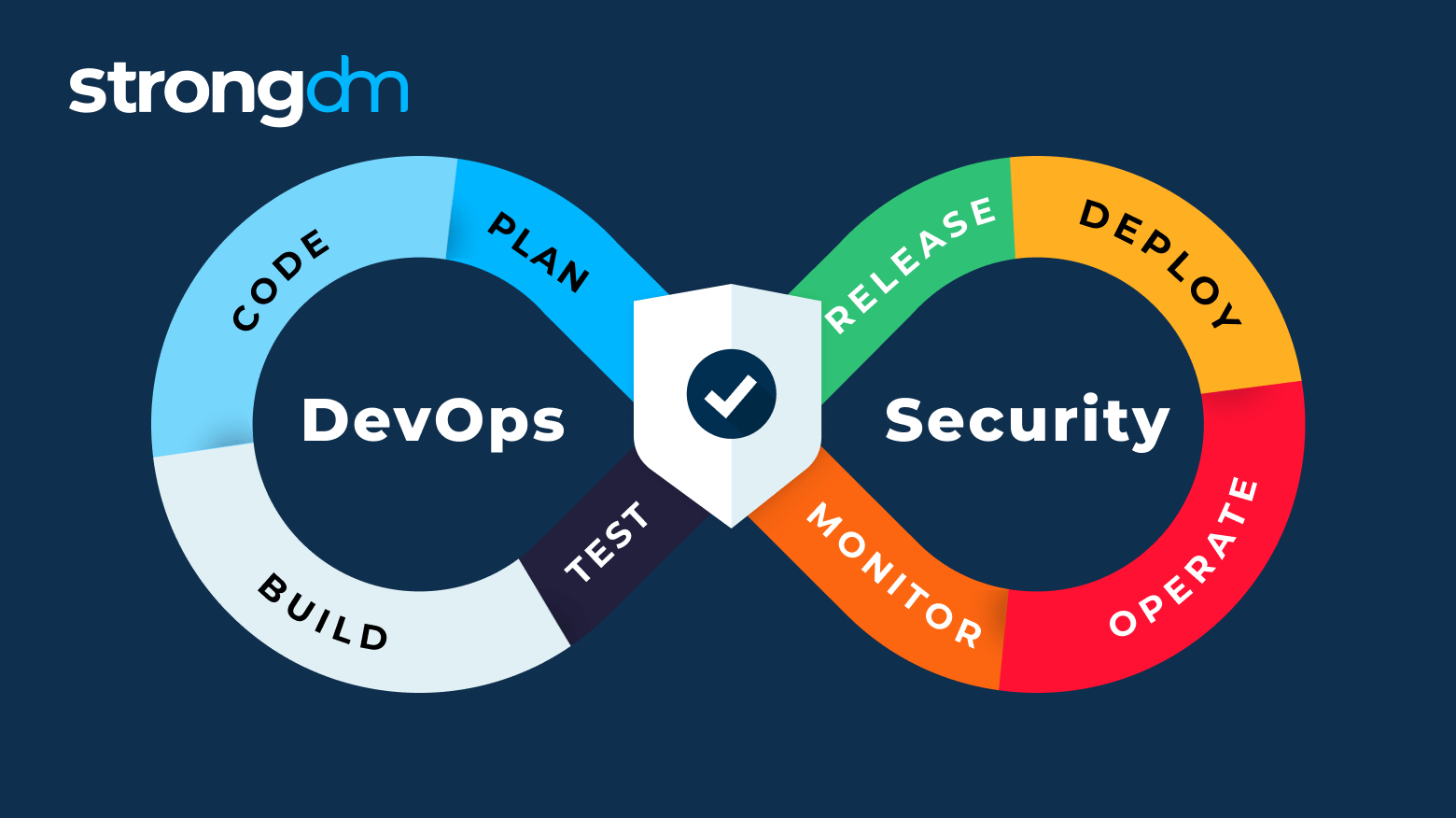
DevOps vs. DevSecOps
DevSecOps is very similar to DevOps. It’s a philosophy that pulls security into the software development process in a way that:
- Assigns responsibility that is shared by both IT and developers
- Integrates automated security into DevOps
Historically, application security was not considered a priority for developers. Security tasks would be completed after development was finished. Best practices have changed over time.
Changes in the cybersecurity scene, including many complex new dangers, call for a more proactive and aggressive strategy, which DevSecOps addresses.
DevOps Security Challenges
What are the reasons behind security failings in DevOps pipelines? The answer can vary, but there are several common causes:
- Lack of security awareness - It may simply be that developers and operations staff do not have enough security awareness. Checks like this have not always been everybody's responsibility, whereas these days, almost all staff are given cybersecurity awareness training. This can lead to vulnerabilities being left alone or overlooked, giving them a chance to build over time.
- Traditional vs. cloud security - The growth in cloud adoption has been staggering over the last few years. However, cloud computing comes with a range of security threats distinct from those found in traditional IT, meaning that a company's previous security controls may be inadequate. When adopting new security tools and processes, DevOps engineers must be aware of how their own security requirements have changed over time.
- Legacy and hybrid infrastructures - As businesses attempt to transition to the cloud, it is not uncommon for them to utilize a hybrid of traditional and cloud infrastructures. This mish-mash environment can result in a host of more complex security concerns. With this in mind, it is important for security-focused staff to assess the exact requirements of their setup rather than just following the guidance of a general methodology.
- Lack of DevOps fundamentals - Visibility, vigilance, and the drive to learn from failure are all essential to DevOps. Combined with frequent testing and experimentation, they enable continuous improvement that keeps pipelines performing as well as possible. With this in mind, ANY kind of security breach or similar issue should be treated as a welcome wake-up call for optimization!
Overcoming issues like this is largely down to encouraging awareness of threats inherent to the current digital landscape. However, it is also important to ensure your DevOps pipeline is actively monitoring and mitigating security threats, with everyone collaborating to optimize safety and resilience.
Learn more about DevSecOps Statistics and Challenges.
DevOps Security Best Practices
To get an idea of how to prioritize security in DevOps, let's return to the roots of the approach. The name 'DevOps' came from giving equal weight to Development and Operations as well as having these areas collaborate and share responsibility. The current landscape requires that cultures give a similar level of consideration to security, hence the term 'DevSecOps'.
So, how can teams ensure that security is given proper consideration?
- Treat security as a continuous priority - Security awareness and checks should be present throughout your DevOps pipeline, with security criteria clearly laid out as policy. This is particularly important early in the development cycle, as developers will require best practices to not only locate vulnerabilities but also avoid creating them. Taking into account ongoing threats and strict compliance regulations, failing to exercise ongoing vigilance can be tantamount to self-sabotage.
- Build awareness - DevOps engineers should always maintain an awareness of how the digital landscape is changing. Companies can facilitate this with security by discussing the growth and tangible consequences of security threats. This also goes back to the essential DevOps principle of shared responsibility, with everyone being held accountable for the success or failure of a pipeline. To emphasize this connection, it can be a good idea to refer to DevOps performance metrics that can be impacted by vulnerabilities and other failures, including the rate of deployment, mean time to recovery, and so on.
- Encourage communication and collaboration - Embedding security practices across a pipeline requires careful communication and collaboration between teams. This includes suggesting automation for inefficient processes, referring to the security impact of failures at different stages of the pipeline, and so on. This is largely a continuation of the ideal DevOps mindset that simply puts security on a similar level to other considerations.
- Smart automation - Automation is a cornerstone of DevOps, with engineers constantly working to increase efficiency and reliability by replacing manual processes. However, not considering the safety of third-party automation tools can be disastrous. This is largely a case of screening suggested automation methods in light of potential vulnerabilities, regardless of whether the suggested method is aimed at security specifically.
- Continuous improvement - It is important for DevOps engineers to be aware that security threats and capabilities are continuously evolving. Hackers and other criminals are always looking for new ways to exploit vulnerabilities and access valuable data. Ongoing communication, testing, collaboration, and experimentation are required to keep pipelines safe and airtight.
- Act quickly - We mentioned previously that security checks are particularly important during the development stage, the reason being that undiagnosed issues can increase in scale over time. Because of this, it is important to have strict policies and practices in place for when vulnerabilities are detected so that engineers can respond as quickly as possible.
- Tool and access security - This can be a vulnerability inherent to DevOps itself. With continuous tool adoption, it is important to be aware of exactly who has access to what. Account data, tool logins, and other important information may be within reach of engineers who simply do not require it. This can quickly create vulnerabilities and increase the margin for human error. To solve this, it is important to utilize privileged access management.
How to Enable DevOps Security In Your Organization
DevOps lends itself extremely well to vigilance and evolution. Both of these are inherent to the success of security in software development. However, realizing this in practice requires active and well-aligned action on the part of engineers. Successful DevOps cultures must learn to elevate security concerns, making them part of DevOps' ongoing holistic optimization process.
Companies can build awareness of security best practices by investing in DevOps training, especially with more recent syllabuses. It can be particularly worthwhile to look at certification schemes for well-defined approaches such as DevSecOps.
Want to learn about how StrongDM can help with DevOps Security? Check out how Splunk built a practical approach to DevSecOps at scale with StrongDM.
How StrongDM Can Help You with DevOps Security
StrongDM redesigns infrastructure access around the people who need it, making it incredibly simple to use while also ensuring total security and compliance. DevOps teams have precise control over what each user has access to without exposing credentials to the end user. Also, with least privlege access by default you can ensure just right permissions every time.
With StrongDM, you can maintain a strong security posture without sacrificing productivity. Try it out today with a free 14 day trial.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Philip Gallagher, Content Writer, graduated from the London School of Economics with a BA in History. Philip is a tireless enemy of cliched corporate jargon. He believes that marketing content should be clear, concise, and relevant to readers. In his spare time, Philip enjoys watching movies, gaming, and writing with friends.
You May Also Like




