Principle of Least Privilege Explained (How to Implement It)


Written by
Maile McCarthyLast updated on:
June 25, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Today we’re going to take a closer look at the principle of least privilege (PoLP)—what it is, why it matters, and how to implement it in your organization.
Understanding the principle of least privilege is critical, as network administrators must strike a balance between ease and security—protecting network access without causing friction for users. If access is too restrictive, employees won’t be able to do their jobs. Too lax, and the door to attack is open.
PoLP is essential to finding balance so you can keep your critical systems safe and workforce productive. Here’s how:
What is the Principle of Least Privilege?
Let’s start with an analogy. Imagine you’ve booked a trip to Hawaii for some much-needed R&R. You’re leaving town for a week and have asked a neighbor to watch your house. You give them a list of expectations: bring in the mail, water the plants, feed the cat, etc. You leave a key under the mat.
At this point, anyone could find the key and gain entry to your house. They could even make a copy of the key and enter at a later time. Is that a risk you’re willing to take?
You could improve the situation by locking your valuables in a safe. You could hand the key directly to the neighbor rather than leave it under the mat. Or you could skip the front door altogether. The cat usually eats on the porch anyway, and the plants could do with a little sun. The neighbor can gather the mail at her own house until you return. By giving the neighbor the bare minimum access needed to do the job, you are implementing the principle of least privilege.
In network security, least privilege is the practice of restricting account creation and permission levels to only the resources a user requires to perform an authorized activity. The terms least user access and least-privileged user accounts (LUA) apply to humans who utilize a computer or network service. But least privilege access management also applies to machines, including applications, processes, systems, and connected devices.
The principle of least privilege model (also called the principle of minimal privilege or the principle of least authority) is widely considered to be a cybersecurity best practice. And it is a foundational step in protecting privileged access to critical data and assets.
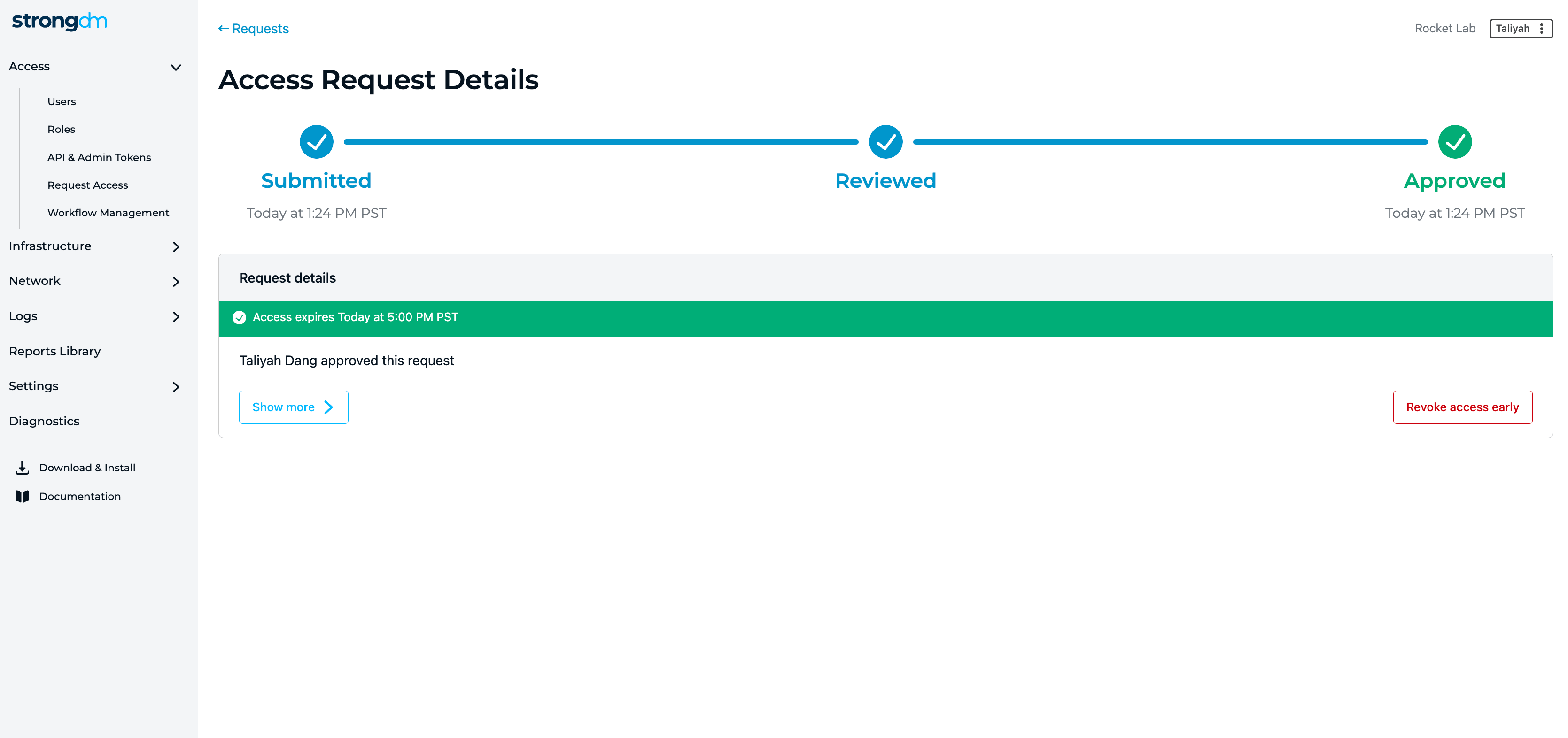
💡Make it easy: Just-in-Time Access works best when it is easy for the end user to request and receive access. It should also be auditing to map the end to end chain of events, who is requesting access, why they are requesting it, and for how long. Play the video below and see how easy StrongDM makes Just-in-Time access and implement least privilege across all your infrastructure. Try it yourself.
Why is PoLP Important?
When done right, the principle of least privilege offers many benefits as it strikes a balance between usability and the implementation of security protections. Such a policy safeguards critical data and systems by condensing the attack surface, limiting the scope of attacks, enhancing operational performance, simplifying auditing and compliance, and reducing the impact of human error.
Over-privileged users, whether human or machine, increase the potential for breaches within an organization and the extent of damage to critical systems should a breach occur. Without adequate protections, common privileged threat vectors, including hackers, malware, and rogue insiders, may misuse, exploit, or actively harm highly-sensitive systems. Even well-meaning users may cause damage. A 2021 study conducted by Aberdeen Strategy and Research found that 78% of insider data breaches are unintentional.

This is why the principle of least privilege is important. The enforcement of PoLP:
- Minimizes the attack surface. Limiting privileges condenses the overall attack surface of your organization, diminishing the pathways a bad actor could use to exploit privileged credentials to access data and sensitive credentials or carry out an attack. A broad attack surface (read: many ways in) is difficult to defend. By limiting superuser and administrator privileges, you make it easier to prevent, detect, and fend off dangerous activity.
- Reduces malware propagation. When users are granted too much access, malware can leverage the elevated privilege to move laterally across your network, potentially launching an attack against other networked computers. You can limit the spread of malware by containing it to the small section where it first enters your network. Additionally, least privilege endpoint management curbs users’ ability to install unauthorized applications, further reducing the chances of spread.
- Improves operational performance. The principle of least privilege, when properly implemented, improves workforce productivity, bolsters system stability, and enhances fault tolerance. It reduces system downtime that might otherwise occur as a result of a breach, malware spread, or incompatibility issues between applications.
- Facilitates audit preparedness. In addition to fulfilling a common compliance requirement, PoLP helps organizations prepare to pass an audit by establishing and maintaining internal company policies and providing an audit trail of privileged activity in the network.
- Safeguards against the human element. Whether through mistake, malice, or negligence, human users can cause great damage to an organization when left unchecked. PoLP limits the power of rogue insiders who choose to do harm. Employee sabotage includes the planting of malicious code, changing administrative passwords, and mishandling data. But even well-meaning users may mistype a command or accidentally delete crucial information. The least privilege access control model reduces the potential damage by limiting the scope of the action.
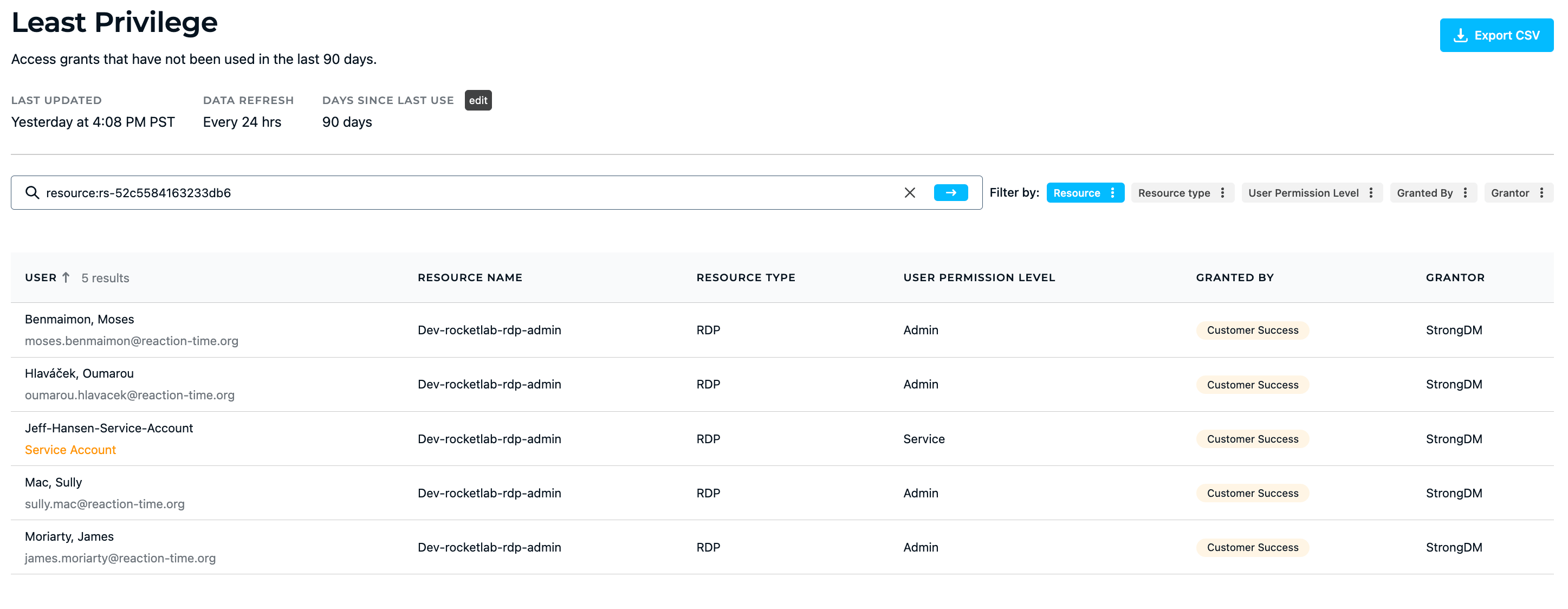
💡Make it easy: Fine-tune least privilege by analyzing and responding to comprehensive access insights. Easily report on which privileges are being used (or not). Try it for yourself.
Practical Examples of Least Privilege Access
With the principle of least privilege, network admins grant only the requisite access needed to perform legitimate activities and nothing more. As we’ve seen, this applies to human users, applications, networks, databases, and many other aspects of your digital environment. The effective implementation of PoLP can prevent and mitigate damage caused by mistakes, misuse, and neglect. Let’s look at a few real-world examples.
Privilege Creep
A junior programmer whose job entails updating lines of legacy code does not typically need administrative access to the customer database. However, occasional projects may temporarily increase the scope of their needs. In such cases, the IT team will grant elevated privileges so the programmer can perform those tasks.
Privilege creep occurs when those rights are not revoked and instead accumulate over time as more temporary access needs arise. We're all human and forgetful. Things can easily slip through the cracks when you don't have enough coffee. Next thing you know, our junior programmer has accidentally deleted every customer in Northeast terriory. Oops!
When admins over-provision access to ease friction, a user who accidentally mistypes a command or deletes an important file can cause catastrophic damage to your organization. Under the principle of least privilege, such temporary access would be revoked when no longer needed, limiting the scope of such damage.
💡Make it easy: Create Access Workflows that are time-bound. These can be automated or require human approval. Eliminate standing access to production environments or databases with sensitive customer information. Try it for yourself.
Phishing Attacks
Here’s another example. Imagine a new marketing specialist joins your organization and is granted administrator access to his personal laptop as a way to ease friction. If this person clicks on an attachment or link in a phishing email and loads malware onto his system, it could cause far-reaching damage.
Under the principle of least privilege, the impact of the attack would be isolated to a narrow band of resources. On the other hand, if the user has root access or superuser privileges, the infection could spread, potentially modifying account settings and corrupting or accessing sensitive data from across the network.
Such breaches can have severe, real-world consequences. Nearly half of US hospitals report disconnecting their networks due to ransomware threats in the first six months of 2021 alone. Some even shut down their networks in anticipation of an attack. Such security measures may protect the network, but they certainly don’t ease friction for users.
Remote Access
In our final example, we’ll look at the importance of least-privilege access with remote workers, including contractors and third-party vendors. Remote work has increased dramatically since the start of 2020. The shift has brought a host of new challenges as the line between home and work has blurred.
Some organizations attempt to secure access to a network using a VPN. This opens them up to a host of vulnerabilities. Suppose an HVAC contractor is given remote access credentials to perform maintenance on temperature control systems, as is common for large retail operations. This allows the contractor to act quickly and perform his job remotely. However, if hackers steal or guess those credentials, they could gain remote access to systems far beyond the HVAC controls, potentially causing network-wide damage.
With the principle of least privilege, remote access is granted only as needed, limiting the reach and opportunity for an attack to take hold. Furthermore, as we’ll discuss below, just-in-time access revokes the contractor’s privilege as soon as the task is complete, adding an additional layer of protection.
Challenges to Access Control Security
We’ve seen how over-provisioning users can lead to problems, including an increased attack surface, poor operational performance, and difficulties with compliance. Why, then, do organizations fail to implement and maintain least-privileged access?
In reality, while the concept of least privilege access management is straightforward, the implementation can be difficult. Factors ranging from employee expectations to the complexity of computing environments can hinder PoLP in practice.
Common challenges include:
- Employee Frustration. When attempts to restrict access cause friction, frustration among users and administrators will rise. This is especially true in DevOps environments, where the focus is on speed and automation. Network admins at large organizations may choose the path of least resistance rather than face a swell of administrative headaches. While those at smaller organizations where team members are known and trusted may believe they are immune to threats.
- Cloud Proliferation. The scale and ephemerality of cloud-native computing can also cause problems with over-provisioning, account sharing, and lack of segmentation. Many users expect cloud services, like AWS IAM, to enforce built-in security. And while cloud-based tools are an improvement over manual solutions for securing privileged accounts, the implementation of PoLP ultimately requires a strategy, not simply a product. This is especially true in multi-cloud networks.
- Diverse Networks. Modern computing environments are diverse, with privileged assets spread across on-prem, virtual, and cloud platforms, heterogeneous operating systems, multiple applications and endpoints, and human and machine identities. As multi-cloud computing becomes the norm, a cloud least privilege manager must centralize access for human and machine accounts across multiple platforms. This presents a novel challenge to implementing the least access principle as tools well-suited to one environment may be incompatible with another.
- Lack of Granularity. Operating systems such as UNIX, Linux, and Windows do not enforce the principle of least privilege by default. The US-CERT website archive explains, “In practice, most systems do not have the needed granularity of privileges and permissions to apply this principle precisely.” It goes on, “The UNIX operating system does not apply access controls to the user root. That user can terminate any process and read, write, or delete any file. Thus, users who create backups can also delete files. The administrator account on Windows has the same powers.” For this reason, it is important to restrict end-user access to the bare minimum required to perform a required task. Grant superuser or administrative permissions only to the Mac, Windows, or Linux users who need it to do their jobs.
- Default Credentials. A recent SANS Institute white paper states that “Operating systems come with default software conditions that emphasize features, functions, and ease of use, at the expense of security.” Beyond OS defaults, credentials embedded in CI/CD tools and applications as well as misconfiguration errors may provide excessive privileged access to machine accounts.
A final thought here: Multiple small challenges can add up to big problems. Poor password hygiene, third-party/vendor access, and easy-to-guess default credentials, for example, can leave privileged accounts unseen and unmanaged. Therefore, it is not sufficient to establish least-privilege policies as part of your access management strategy. Accounts must also be discovered and thoughtfully managed.
How to Implement Least Privilege Security
The successful application of least privilege requires you to centrally manage and secure privileged accounts and credentials for both human and machine entities. Remember to include applications, devices (such as IoT), processes, and services, as any of these accounts, when left unmanaged, represent a potential for compromise.
Establish a cohesive access management strategy, including policies, procedures, and tools which help you authorize and authenticate to privileged systems. Regularly perform privileged access audits, along with time-bound access practices and effective monitoring, to help safeguard your sensitive data.
The following best practices will help you stay on track:
- Carry out a privilege audit. You can’t protect what you can’t see. Perform a thorough audit of your full environment to ensure that all privileged accounts are under policy management. Include privileged accounts and credentials held by employees, contractors, and third-party vendors, whether on-premises, over remote access, or in the cloud. Your audit should cover both human and machine identities, including those in DevOps workflows, with special attention on default and hard-coded credentials that organizations frequently overlook.
- Establish least privilege as the default. Grant all new accounts the minimum privilege needed to perform the job. Remove or reconfigure default permissions on new systems or applications. Zero standing privileges should be your goal, where feasible. Using role-based access control can help you determine which privileges a new account requires by setting general guidelines around a responsibility, task, or team. Be sure to adjust permissions as a user’s role changes to avoid privilege creep.
- Implement separation of privileges. Avoid over-provisioning by restricting local administrator privileges. Separate administrative accounts from standard accounts, even for the same user, and isolate privileged user sessions. Grant higher-level system functions (read, write, execute) at the minimum level required. Additionally, divide auditing and logging capabilities. Host your session logs outside of the database they are monitoring and restrict write access for log admins.
- Provide just-in-time, granular access. To maintain least-privilege access without impeding employee workflow, supplement role-based access control with time-limited privileges. Replace hardcoded credentials with dynamic secrets or implement one-time-use (or disposable) credentials. This allows you to temporarily elevate access permissions without causing privilege creep in cases where a user requires increased authority to carry out a specific task or short-term project.
- Monitor and analyze privileged access. Continuously log and monitor authentications and authorizations to systems throughout your network. Ensure that individual actions are traceable. Capture all keystrokes, RDP, and SSH sessions, and use automation tools to detect anomalous activity and alert you to potential problems.
- Review privileges regularly. Your company should define a cadence to review existing accounts and permission levels. Newer companies should hold a monthly review, while mature companies with more accounts to manage can host a quarterly review. Revoke any excess privileges you discover, and close or deprovision all inactive accounts.
These best practices will help you secure your privileged accounts, data, and assets to enforce compliance requirements and improve operational security without disrupting user workflow.
Conclusion | Simplify User Access with StrongDM
Successful implementation of the principle of least privilege balances security and productivity. It eases friction for workers by increasing network uptime and reducing the impact of user error. At the same time, it condenses your cyberattack surface, making it harder for bad actors to release malware and access sensitive data.
While workflow disruptions, diverse computing networks, and default credentials all present challenges, access control software can help. StrongDM is a control plane for centralizing user access across differing environments, making it easy to enforce the principle of least privilege without administrative busywork. And built-in session monitoring and log collection help streamline compliance requirements, making it easier to pass an audit.
If you want to learn more about how StrongDM can help you implement the principle of least privilege, contact one of our experts today for a free demo.
To learn more about how StrongDM helps companies with managing permissions, make sure to check out our Managing Permissions Use Case.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Maile McCarthy, Contributing Writer and Illustrator, has a passion for helping people bring their ideas to life through web and book illustration, writing, and animation. In recent years, her work has focused on researching the context and differentiation of technical products and relaying that understanding through appealing and vibrant language and images. She holds a B.A. in Philosophy from the University of California, Berkeley. To contact Maile, visit her on LinkedIn.
You May Also Like