How Better Access Improves Productivity of Tech Staff [New Research]

Written by
Dominic GarciaLast updated on:
October 5, 2022Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Have you ever wondered how access impacts your productivity? If you're like most technical staff, the sum of hours lost adds up quickly across teams. It makes sense though. The longer it takes for you to access the systems you need, the less productive you are on any given day. And what happens when that access is too difficult to get? We found that teams typically set up workarounds. They still have deadlines to meet, after all. But suddenly that easy access comes at the expense of security.
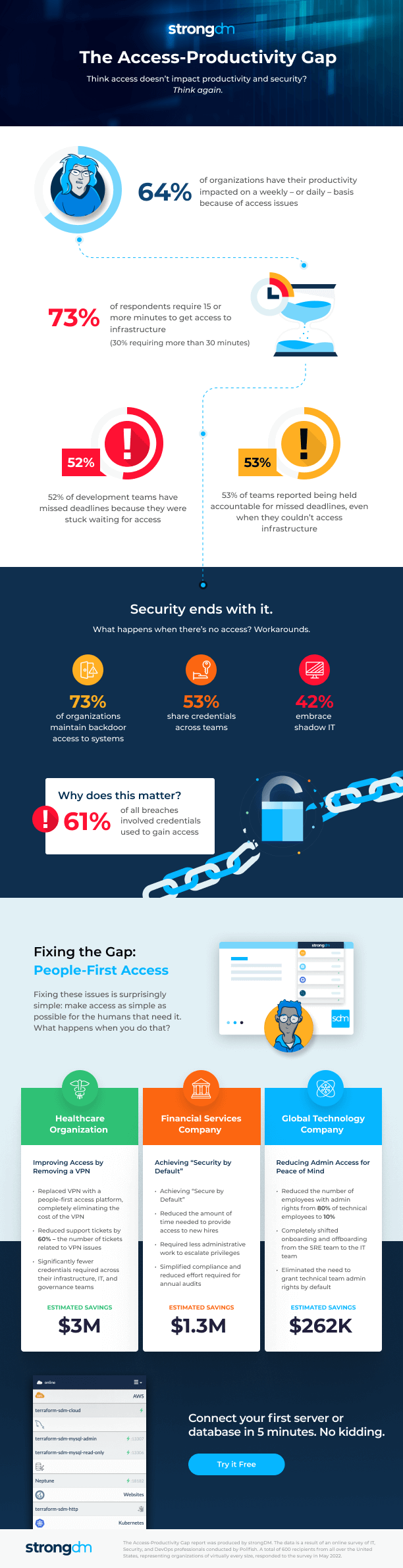
This can have a substantial impact on your bottom line. For example, Verizon’s research proved that 61% of all breaches involved credentials to gain access. And with each breach costing $4.35M on average, the cost of poor access extends far beyond lost productivity.
So how do you start to break the cycle?
Productivity & Security Start with Access
In a word: Access. Every technical employee requires access to do their job successfully, but they don’t always have access to what they need. Whether they are struggling to access a specific database or they are unable to add new tools to their existing access management solutions, both predicaments result in scrambling for workarounds or waiting on approvals.
For example, a developer must log in to a Kubernetes cluster to work within an application. But they can’t get in, and their manager, who normally would provision access, is on vacation somewhere with spotty reception. They have to kick their request up the chain manually and hope they can get started, losing valuable hours or even days in the process.

Think this isn’t happening in your company? Think again. Nearly one-third of technical employees (31.8%) reported daily interruptions to their work because of access issues, and another third (32.3%) reported weekly interruptions. Suddenly, this access issue hurts your ability to build and deliver products, and customer service is at risk. Now more than ever streamlining access becomes paramount to meeting deadlines and avoiding breaches of contract.
Access Is the Root of Security
Your company’s productivity isn’t the only thing at risk when employees don’t have the right access. Technical teams are very resourceful, and when they can’t access the systems they need to do their jobs, many turn to workarounds like shadow IT, sharing credentials, or maintaining backdoor access.

While technical teams can accomplish the task at hand with these workarounds, they’re also exposing the company to security breaches. For example, 8 in 10 (81%) of hacking breaches are due to shared passwords–and an alarming 53% of employees have shared their credentials.
Streamlining Access Brings Additional Benefits
Productivity and security are two critical reasons to streamline access, but there are many more.
Employees who have the tools to do their jobs tend to be happier–and less likely to leave. Nearly half of employers (44%) say that employee turnover makes it more challenging to achieve their goals, and it takes an average of 44 days to fill a technical position.
It’s not just the technical teams that will save time and be more productive. Streamlined access means their managers don’t have to approve access manually, nor does access need to be manually provisioned. One global technology company was able to completely shift onboarding and offboarding from the SRE team to the IT team, freeing up the SRE team’s focus.
Streamlining access also makes it easier to meet auditing and compliance requirements. With StrongDM, you’ll have a comprehensive audit trail that makes it easy to identify who accessed a particular system, when they did it, and what they did while in the system (such as the queries run in a database). This visibility also translates into information that can be used for training or troubleshooting.
So what’s stopping you from streamlining access and improving productivity? Yes, you can escape the negative loop of access, productivity, and security and put your people first–elevating morale in the workplace, showcasing products you deliver, and maintaining your peace of mind. StrongDM collected data from multiple third-party sources and compiled our results in a single, stat-packed report. Our latest report details the risks that access workarounds bring to organizations and the benefits you can achieve when access is managed appropriately.
Download The Access-Productivity Gap today.
Curious about how this gap impacts Financial Services? Download the special Financial Services edition.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Dominic Garcia, Technical Marketing Expert, has held marketing leadership roles for Silicon Valley technology companies specializing in database, data management, and data analytics solutions. As head of content marketing at Splunk, Dominic contributed to boosting the company’s market visibility and its growth from a $100M to a $1.3B company. He brings relentless creativity to the task of connecting people with technical products to improve their lives. Dominic holds a B.S. degree in Public Relations from the University of Texas at Austin. To contact Dominic, visit him on LinkedIn.
You May Also Like