Leveraging CSA CCM with StrongDM for Enhanced Cloud Security

Written by
John MartinezLast updated on:
September 6, 2024Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
At the risk of delivering the understatement of the year so early in the calendar, let’s just have at it: meeting rigorous compliance standards for your cloud environment (and your data centers, if you still have those) is hard.
That may be a big, “duh,” but security and compliance leaders recognize that it’s been a long time since “compliance” could be equated with a simple checklist. The sheer amount of resources in the modern tech stack, the democratization of technology usage, and the increase in standards frameworks have conspired to create a massive footprint that needs to be regulated. Doing that requires a robust, dynamic approach that is both comprehensive in what it assesses, and is agile enough to be implemented without being overly disruptive.
The Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM) provides a comprehensive security control framework that accounts for the challenges of modern IT infrastructures, and guides organizations in securing their cloud environments. Together with StrongDM's Zero Trust PAM and Continuous Authorization capabilities, organizations can satisfy not only their IAM compliance controls, but also significantly mature their identity security posture. We’ll explore how the CSA CCM framework, combined with StrongDM, offers a powerful, highly-usable solution for enhancing cloud security. By enhancing CCM with a dynamic and continuous approach to authorization, StrongDM customers get a “short cut” to solving their compliance requirements.
Understanding CSA CCM
The CSA CCM is a cybersecurity control framework specifically designed for cloud computing. It outlines a comprehensive set of best practices and security controls across 17 domains that are designed to ensure that cloud environments are secure and resilient against an ever expanding threat landscape. The CCM framework is structured to provide clarity and actionable guidance for the implementation of security measures in a prescriptive and adaptable way for recognized compliance standards and control frameworks.
The Value of CSA CCM Cross-Mappings
One of the unique aspects of the CSA CCM is its cross-mapping to other industry and regulatory compliance standards and control frameworks, such as CIS (Center for Internet Security) Controls, PCI, and HIPAA, to name a few. This cross-mapping offers organizations a streamlined approach to compliance, enabling them to prepare for meeting multiple standards through adherence to a single, unified framework. The practical implications of this are significant: simplifying compliance efforts; and reducing the complexity of securing cloud environments.
StrongDM’s dynamic approach gives CCM adherents a true blueprint for ensuring effective cross-mapping across different compliance frameworks. It provides:
- Standards Alignment: Cross mapping helps organizations align their internal controls and security measures with established industry standards and compliance frameworks. This ensures that the organization's practices work according to widely accepted norms, making it easier to demonstrate compliance during audits.
- Efficient Compliance Management: By cross mapping, companies can identify commonalities and overlaps between different compliance frameworks. This helps in streamlining compliance management efforts, avoiding duplicative tasks, and ensuring that one set of controls can address multiple regulatory requirements.
- Cost Savings: Mapping controls across multiple frameworks can lead to cost savings. Instead of developing separate controls for each compliance standard, companies can leverage shared controls, reducing the overall financial burden associated with compliance implementation.
- Risk Mitigation: Compliance frameworks are designed to address specific risks and threats in the respective domains. Cross mapping ensures that companies consider a comprehensive set of controls, reducing the likelihood of overlooking critical security measures and thereby enhancing overall risk mitigation efforts.
- Simplified Reporting: When an organization adheres to multiple compliance frameworks, reporting can become complex. Cross mapping facilitates the creation of consolidated reports that demonstrate compliance with various standards, making it easier for stakeholders, auditors, and regulatory bodies to assess the company's overall adherence to industry norms.
- Enhanced Security Posture: Many compliance frameworks are developed based on best practices and industry expertise. By cross mapping, companies can adopt a holistic approach to security, incorporating proven controls from various standards. This, in turn, helps in strengthening the organization's overall security posture.
- Adaptability to Changes: Compliance frameworks are subject to updates and changes over time. Cross mapping allows companies to adapt more easily to new or revised standards by leveraging existing mapped controls and adjusting them as needed, minimizing the impact of regulatory changes.
StrongDM's Alignment with CSA CCM
StrongDM’s Zero Trust PAM platform plays a crucial role in aligning with the CSA CCM by providing capabilities and audit data that directly supports key IAM controls within the framework. StrongDM's platform enables organizations to manage and monitor access and user sessions to their cloud environments, data stores, Kuberenetes clusters, and compute instances in real-time, ensuring that only authorized users can access sensitive resources. StrongDM is perfectly in line with the CCM's recommendations for secure access and identity management.
To provide more context and support for CCM users, StrongDM has recently published a solution guide for CCM 4.0. It provides details about CCM requirements and how StrongDM capabilities can help you meet specific controls. You can see how we’ve outlined this control mapping in the image below;
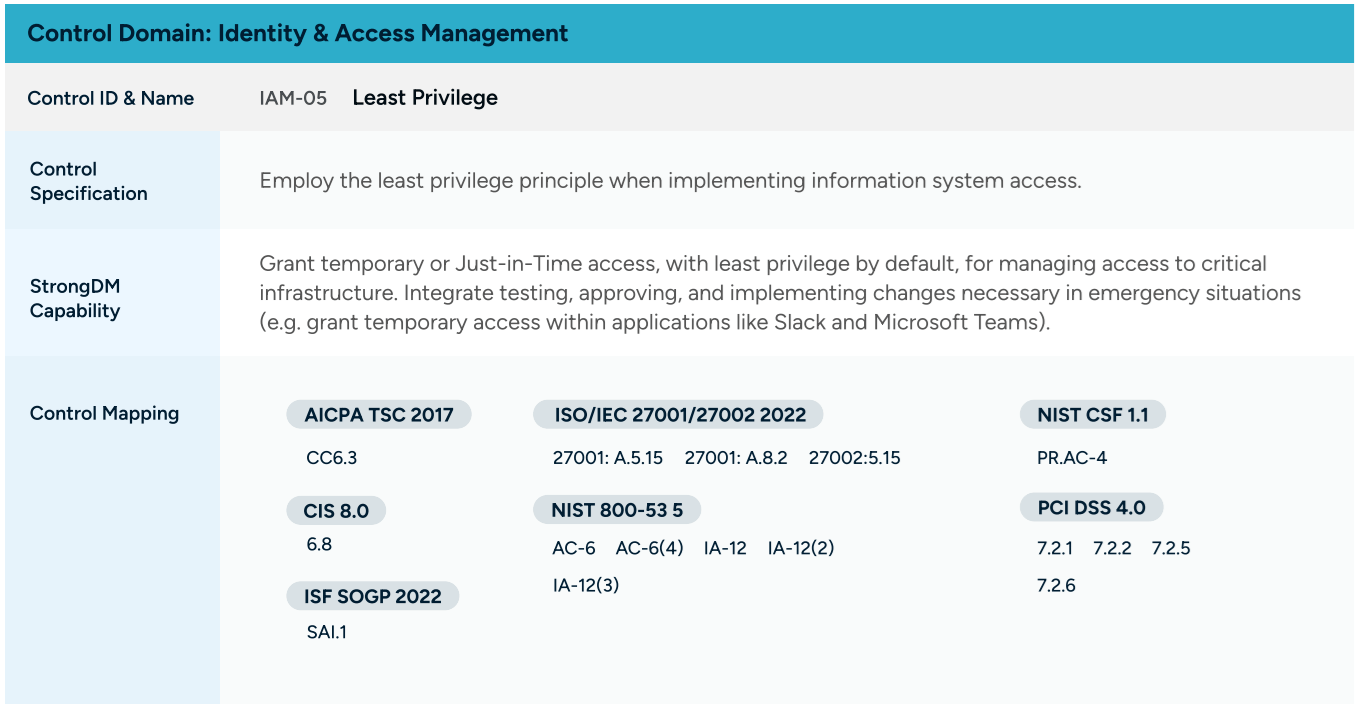
Leveraging StrongDM for Compliance and Beyond
StrongDM's Zero Trust PAM capabilities not only simplify adherence to CSA CCM controls but also enhance overall security and compliance for an organization’s managed resources. The platform's continuous authorization approach ensures that access rights are constantly evaluated, adapting to changes in user behavior and other contextual signals. This proactive approach to access management goes beyond meeting compliance controls, it offers organizations a way to actively protect their critical cloud resources against unauthorized access and privilege escalation attacks.
The StrongDM platform also collects critical logging information which helps make sense of any auditing actions you may need to take. This is an important factor because of the continuously changing nature of cloud environments. Consider that you may be, at any given time, accumulating terabytes of log data from your intrusion detection system and antivirus solution. However, the potential exists to overlook crucial details if your security logs fail to address the following questions — all of which is provided by the StrongDM platform:
- What happened?: Are there relevant error messages, event IDs, or other indicators that provide insights into the security event?
- What systems are affected?: Do the logs capture pertinent system names and IP addresses to identify the impacted systems?
- When did it happen?: Are the activities and actions outside the normal windows?
- Who was logged in?: Are events associated with a unique user ID, allowing for the identification of individuals involved?
While this core information offers a foundation for effective issue triage and response, the "who" question becomes particularly vital. It extends beyond understanding who accessed the system; it requires knowledge of specific actions taken at critical moments, such as discerning an individual's activities at, say, 11:41am on July 16th when a system incident occurred. It involves examining other activities linked to the individual and verifying whether those activities fell within their access permissions.
This critical information becomes readily accessible when utilizing a tool that generates comprehensive access log files, including details about:
- The provisioning and de-provisioning of user access to a resource
- Granting or suspension of sessions
- The detailed activities performed by a user
- Recordings of sessions of those activities
All of these should be coupled with Integrations to log analysis tools and SIEM systems that operate to support an organization’s compliance, security, and incident management strategy.
Tying Things Up
The CSA Cloud Controls Matrix is a cloud-relevant framework for implementing prescriptive security controls, with its value further amplified through cross-mappings to other compliance standards. StrongDM's solutions directly support the fulfillment of IAM controls within the CCM, providing a pathway to other compliance standards. By leveraging StrongDM in conjunction with the CSA CCM, organizations can achieve a simplified user experience without sacrificing a strong security posture.
Learn more about how StrongDM helps you meet the CCM framework guidelines as well as map the controls to multiple security frameworks for Identity and Access Management.
Want to see StrongDM in action? Book a demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like