SASE or Dynamic Access Management? Here’s Why You Need Both
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
I wish you could have seen my dear late mother leave her house. It involved a series of intent-based actions, checks, and re-checks, all built into a confirmatory loop that ideally left her with mental and emotional peace: The stove is off, the temperature is adjusted correctly and the doors are locked. Now she can enjoy tea and cakes with her friends.
That continuum of checks and desired assurances is similar to what CISOs experience. They must know what is happening at all times, everywhere, and with everyone. And that’s not just a nice-to-have. Compliance mandates and self-imposed policies and controls dictate that awareness and understanding are critical to manage the security of their infrastructure effectively.
The Need for SASE
As the scope of enterprise attack vectors widens, spanning cloud applications, on-premises assets, and personal devices, there has become a critical need for simplifying and consolidating network and security tools. Secure Access Service Edge (SASE, pronounced “sassy,” also a concept my mother could relate to) is a framework that enhances an organization's capabilities by combining network security and wide-area networking. It enables your organization to:
- Securely connect users to applications
- Precisely enforce security controls
- Enhance operational efficiency
That’s a much-needed remedy for the ever-expanding surface areas that require security controls to be enforced directly at the point of connection—a user, device, Internet of Things (IoT) device, or edge computing location—rather than through a centralized data center.
SASE Origins
SASE, coined by Gartner in 2019, represented a major pivot in networking and security architecture. It consolidates networking and security capabilities into a cloud-native, edge-based service model. By integrating functions like Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA), and Firewall as a Service (FWaaS), SASE provides organizations with a comprehensive, streamlined solution for securing network access from any location.
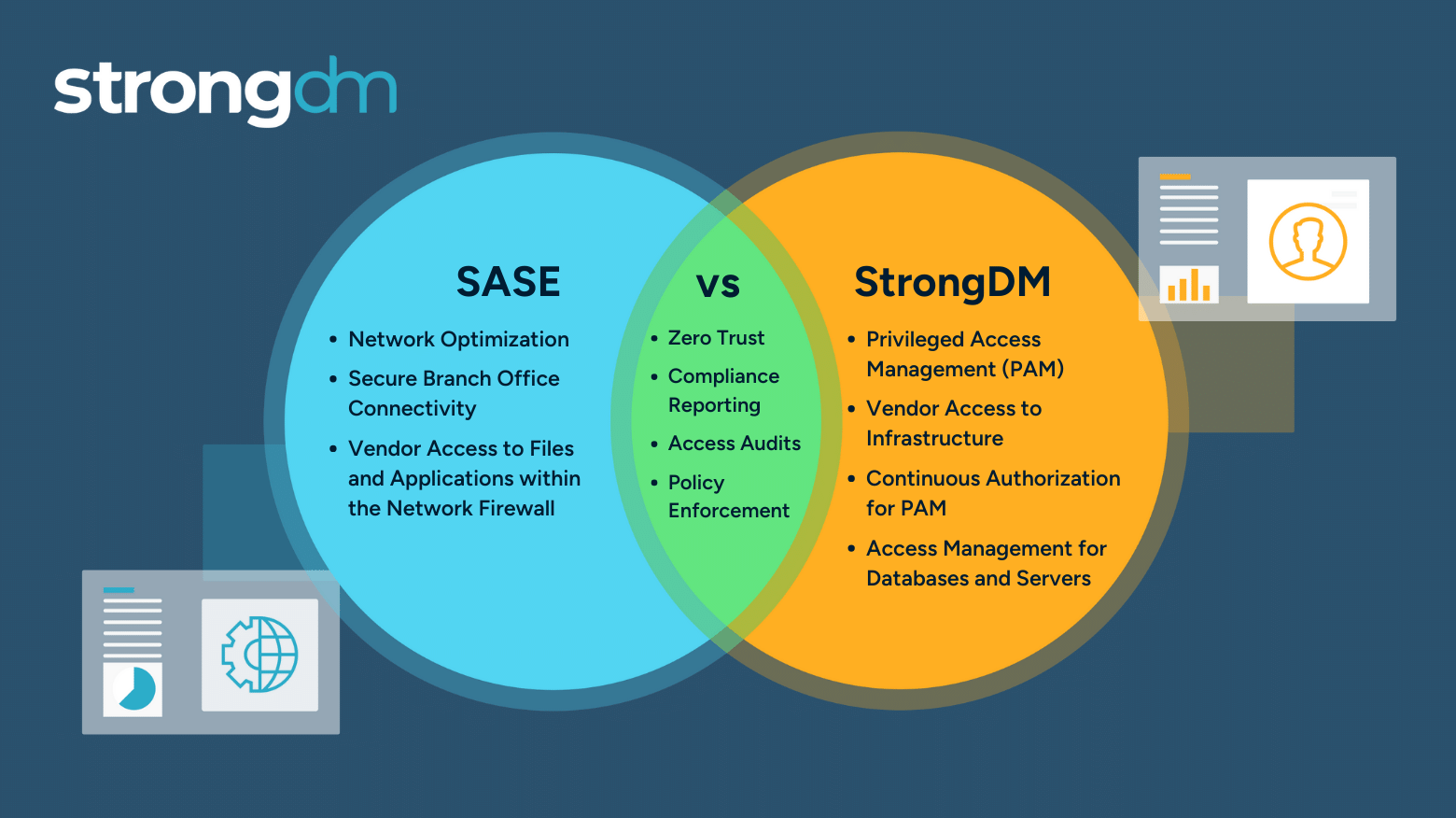
Privileged Users: Where SASE Falls Short and DAM Completes It
Yet, while SASE excels in providing broad network security coverage and solves broad issues for regular enterprise users, it is not equipped to address the specific requirements of privileged users who wield extensive administrator or superuser privileges. Dynamic Access Management (DAM) addresses the specific needs of privileged users by providing granular control over their access grants and sessions in real time.
Unlike traditional access management approaches, which often rely on static permissions assigned to users once at the beginning of a session, regardless of context, DAM dynamically grants access permissions based on various factors such as user roles, tags, resource type, via an auditable approval workflow.
For privileged users that require permission to perform sensitive actions on critical resources, DAM ensures they only have access to those resources and data when they need it, and only for the required duration. Combined with Continuous Authorization, it can dynamically change the access aperture based on changing circumstances, such as revoking access immediately if suspicious activity is detected, or restricting elevated permissions further on the resource or for a specific action.
SASE and DAM in Harmony
Now, there are distinct differences between SASE and DAM. Organizations deploy SASE to govern access from their enterprise users and use PAM for their privileged users. Think of it this way: Motorized vehicles are all forms of transportation, but you need to pick the right one for the right job—you may drive your minivan on a family vacation, and then switch to driving a truck to make deliveries.
Combining SASE with DAM
By combining DAM with a SASE framework, organizations can extend the benefits of SASE to privileged users, ensuring that they receive the appropriate level of access control and security measures tailored to their specific requirements. This ensures that while SASE provides broad network security coverage for all users in an enterprise, DAM addresses the unique needs of privileged users, enhancing overall security posture and minimizing the risk of insider threats or unauthorized access.
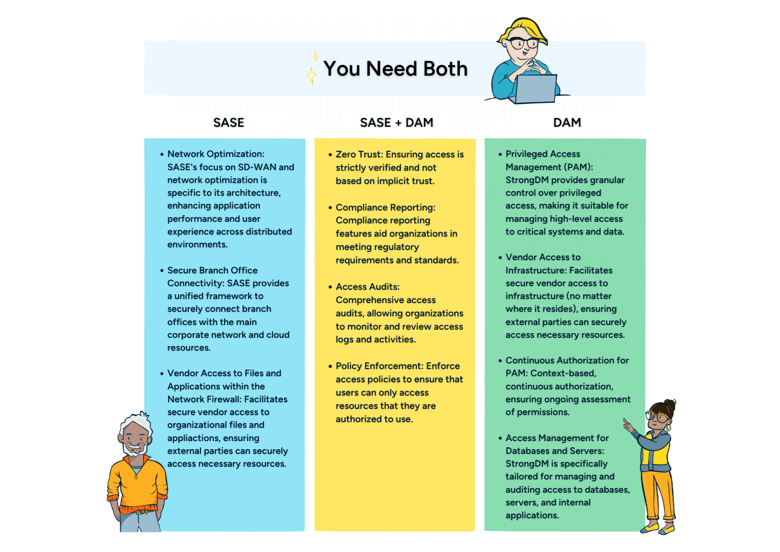
The StrongDM Dynamic Access Management (DAM) platform precisely controls privileged access within an organization’s infrastructure. Unlike the broad scope of SASE, DAM operates at a granular level, offering fine-grained control over user access to and actions on critical resources, databases, and systems. Through Continuous Authorization, StrongDM ensures that access permissions are dynamically adjusted based on real-time user behavior and contextual data.
Now, just like my mother’s children, whom she claims to love all the same (except that time my “science” experiment almost set the house on fire; love was suspended for about 36 hours), SASE and DAM both serve critical needs in the CISOs portfolio. It’s just a matter of what you’re trying to achieve and the rigor you’re trying to accomplish it.
The StrongDM DAM platform does what traditional SASE solutions are not designed to do. Again, this isn’t a fault or limitation of SASE; it was designed for a broader set of enterprise needs and falls short in addressing the specific requirements of privileged users with extensive access privileges. StrongDM’s granular control mechanisms empower organizations to manage privileged access and actions with precision, mitigating the risk of insider threats and unsanctioned actions.
Complementary Components
It's important to note that StrongDM is not a replacement for SASE but a complementary component within the broader security framework (and the same is true for SASE; it cannot replace, nor mimic what DAM provides). As organizations embrace the depth and breadth of SASE capabilities, they begin to recognize the need for both SASE and DAM to effectively manage access. They are able to enhance their security posture by integrating the StrongDM DAM model to address the very unique challenges associated with privileged access management.
StrongDM's Continuous, Contextual Policy-based Authorization
StrongDM’s new Continuous, Contextual Policy-based Authorization functionality provides unparalleled granular control for administrator actions. By doubling down on capabilities that enable organizations to enforce stricter access policies and monitor user activities in real time, StrongDM reinforces its position as a leader in DAM.
While SASE helps organizations secure network access in an increasingly distributed and cloud-centric environment, StrongDM’s DAM platform addresses the challenges of privileged access control. Organizations can adopt SASE to protect their Enterprise users, but they need to adopt StrongDM to protect their infrastructure and their applications by ensuring policy based privileged access control to remain in continuous compliance.
Oh, and good news, our house survived my “science” experiments.
Want to see StrongDM in action? Book a demo.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Amol Kabe, Chief Product Officer (CPO), spearheads the StrongDM Zero Trust PAM platform. Previously, he was the Senior Director at Google, leading the Zero Trust and Identity and Access Management portfolio for GCP. His career includes executive roles at Netskope, driving its transition from CASB to SASE, and at Riverbed Technology. Amol was also a founding member at Tablus, a pioneer in Data Loss Prevention. To contact Amol, visit him on LinkedIn.
You May Also Like