Understanding Cloud Access Security Brokers (CASBs)

Written by
Schuyler BrownLast updated on:
June 26, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Summary: In this article, we’ll take a high-level look at what a CASB is, what it does, and how it works. You’ll learn the key pillars of CASBs and how they address the growing threat of Shadow IT in cloud-based organizations. By the end of this article, you’ll understand the differences between CASB, SASE, and IAM, as well as the main challenges to implementing a CASB solution.
What Is CASB?
The rise of remote work has brought new challenges for security. Cloud usage is expanding, employees are using personal devices with greater frequency, and Shadow IT—the unsanctioned use of devices, software, or services—is emerging as a serious problem. Organizations need a new way to effectively monitor and govern cloud application use as part of a robust security posture. CASB offers a solution.
A Cloud Access Security Broker (CASB) is software that applies an organization’s security policies beyond its own infrastructure to protect its cloud environments.
CASBs include security services such as:
- Discovering sanctioned and unsanctioned (aka “Shadow IT”) applications
- Auditing cloud app configurations
- Preventing data leaks or data loss
- Detecting malware automatically
- Encrypting data
- Monitoring user activity
- Alerting administrators to potential risks and real-time threats
CASBs are essential for organizations that utilize cloud-based applications. CASBs fill in the security gaps that are not covered by cloud application vendors and extend across software-as-a-service (SaaS), infrastructure-as-a-service (IaaS), and platform-as-a-service (PaaS) environments. This allows organizations to safely access the cloud without compromising sensitive corporate data.
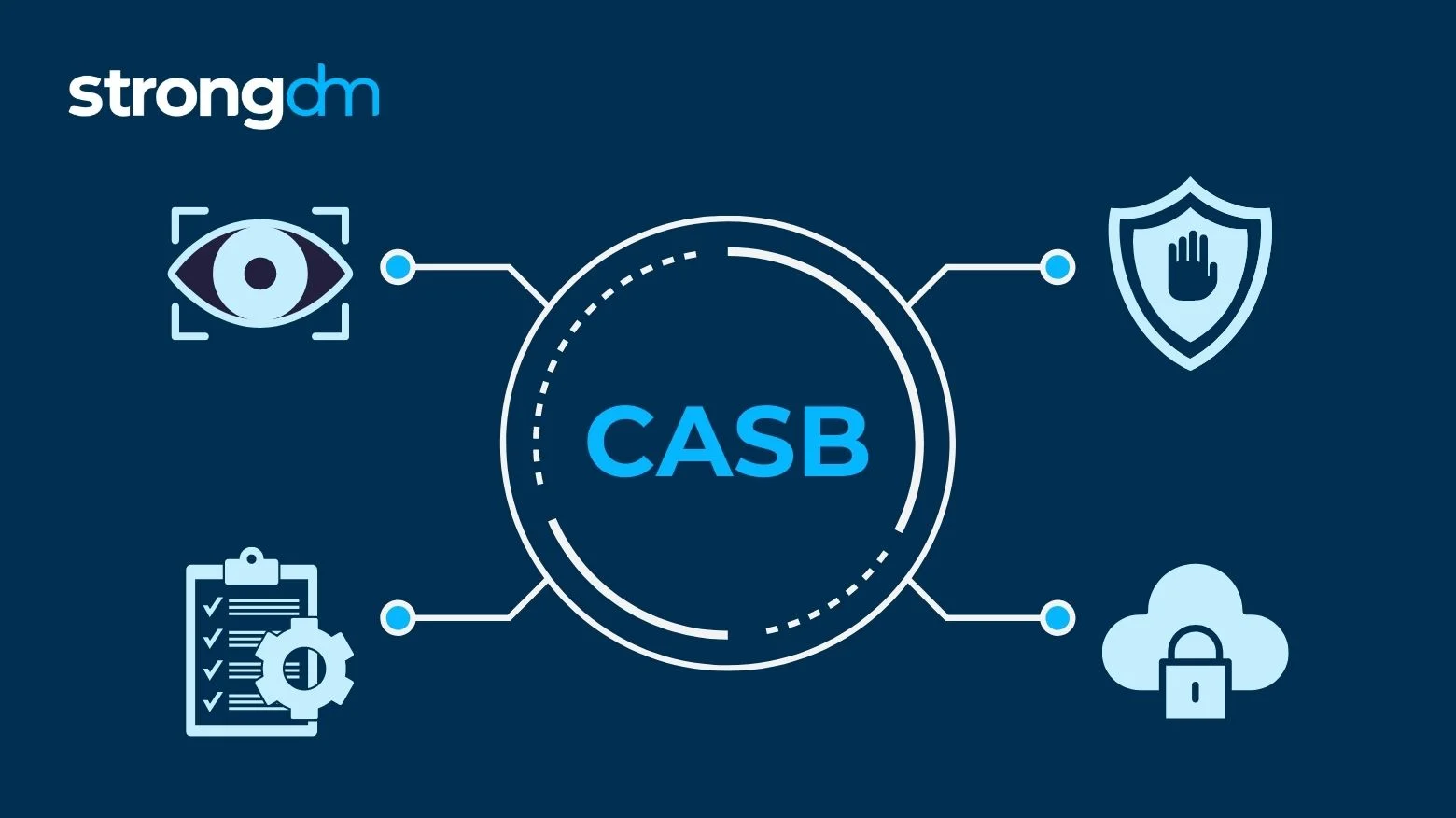
Four Pillars of CASB
The security features embedded in a CASB solution can be categorized into four main pillars.
Visibility
One of the main challenges that enterprises face in a cloud-enabled environment is a lack of visibility into the entire network. Today’s employees are accessing multiple applications across many cloud environments—and any cloud usage that is outside IT’s view means enterprise data is no longer subject to the company’s governance and security policies. This leaves the company vulnerable to security breaches and compliance risks.
CASBs protect an organization’s users, data, and intellectual property by monitoring traffic through both sanctioned applications and Shadow IT, providing full visibility into cloud application usage. Cloud discovery analytics provides security administrators with the risk level of cloud services so they can determine which apps to allow access to and which ones to block.
Threat Protection
CASBs protect an organization against threats related to user behavior and the use of corporate data across internal and external networks. They do this, in part, by ensuring unwanted devices, users, and applications cannot access cloud services. They also use machine learning to create User and Entity Behavior Analytics (UEBA) that review usage patterns to detect and address threats in real-time.
Other CASB threat protection measures include anti-phishing, malware detection, account takeover protection, and URL filtering.
Data Protection
On-premises data loss prevention (DLP) solutions typically provide network, discovery, and endpoint protection, but their security features do not extend to cloud services. CASBs work with an enterprise’s DLP solution to provide blanket protection that allows IT to see when sensitive data is moving within the cloud.
CASBs enforce data-centric security policies based on data classification and through controls like alert, block, audit, delete, and encrypt. CASBs also monitor the access of sensitive data or privilege escalation. This contextual access control governs the level of access users are given to an application and works in conjunction with data leak prevention to monitor and control what data is being accessed and how it can be used.
Compliance
Compliance is a critical and often complicated standard for organizations to manage. This is especially true as increasing amounts of data and services are moved to the cloud, as most vendors do not provide the level of security required for full compliance. CASBs help enterprises maintain compliance in the cloud through comprehensive monitoring, access control, and DLP. They also help identify key areas of compliance risk so IT can ensure regulatory compliance at every level.
How Does a CASBWork?
CASBs operate simultaneously as filters, firewalls, and proxies between users and cloud environments.
As Gartner explains, CASBs consolidate multiple types of security enforcement, including:
- Authentication
- Single sign-on
- Authorization
- Credential mapping
- Device profiling
- Encryption
- Tokenization
- Logging
- Alerting
- Malware detection and prevention
CASBs apply those security policies to everything the business uses in the cloud and to every device that requests access. CASBs use a variety of tools to accomplish this, including Application Programming Interfaces (APIs), gateways, log data, and agents. APIs monitor activity, analyze content and adjust settings as needed. Gateways sit between users and the cloud apps to provide real-time insights and policy enforcement. Log data is imported from firewalls and secure web gateways to analyze and secure traffic. Lastly, endpoint agents help manage user activity on BYOD and enforce policies.
What Is Shadow IT?
Shadow IT is the use of devices, software, and services without IT’s knowledge or control. This may include non-sanctioned activities or purchases related to:
- Hardware such as servers, PCs, and smartphones
- Packaged, off-the-shelf software
- Cloud services, including SaaS, IaaS, and PaaS
Shadow IT has grown exponentially with the rapid adoption of cloud services and employees utilizing their personal devices for work, largely as a result of remote work and digital transformation. According to a report by Statista, some of the most common Shadow IT applications adopted by employees include file storage and sharing services, video conferencing tools, and collaboration tools.
Using unapproved applications brings serious information security risks as IT has no visibility or control over that access. In other words: if you can’t see it, you can’t protect it.
One of the biggest benefits of a CASB solution is its ability to address the increasing threat of Shadow IT. This is especially relevant today, as more employees are working from home and using their own devices and technology solutions to supplement and streamline their workflows outside of IT’s approved tech stack.
Employees typically turn to Shadow IT for convenience or efficiency’s sake. It’s often easier to integrate personal devices and tools (such as collaboration software) to conduct business as sanctioned IT solutions may be buggy, unreliable, or difficult to integrate with other tools in employee workflows.
Although Shadow IT can make employees—and, by extension, an organization—more agile and productive, it needs to be managed in order to mitigate risks.
In order to effectively address Shadow IT, administrators need to:
- Assess the scope of Shadow IT in your organization.
- Monitor and prioritize risk.
- Establish guidelines around cloud services and BYOD.
- Control access to third-party apps.
These capabilities are why CASBs are so useful in managing Shadow IT. CASBs monitor and identify all data movement across the cloud, including Shadow IT access such as employees logging on to the corporate network via an unmanaged device (e.g., a personal laptop).
CASB vs. SASE
CASB and Secure Access Service Edge (SASE) are both designed to address the needs of a growing enterprise cloud environment. SASE accomplishes this by integrating networking and security into one streamlined solution instead of traditional perimeter-based security architectures.
As Gartner explains, SASE provides a cloud architecture model that “combines network security functions (such as SWG, CASB, FWaaS, and ZTNA), with WAN capabilities (i.e., SD-WAN) to support the dynamic, secure access needs of organizations.”
This synergy reduces organizational complexity while ensuring access control and consistent policy enforcement across the network—no matter from where users are connecting.
You may also be interested in our blog post, SASE vs. CASB: Everything You Need to Know.
So how does CASB fit in?
The main difference between a CASB and SASE is the level of security integration and what assets are protected in the solution. CASB focuses specifically on cloud security and is particularly useful to organizations that have invested in other security solutions and need to fill the cloud security gap. In contrast, SASE provides a more holistic solution to network security combined with WAN capabilities.
Both a CASB or SASE solution provides the needed functionality for cloud security. But, which solution an organization adopts depends on its unique business needs and security and networking environment.
A SASE solution is generally the better option for all-around security and networking integration because it simplifies and streamlines security and network management. However, CASB is a simpler alternative that is more easily added to the organization's existing infrastructure.
What Is the Difference? CASB vs. IAM
CASBs and Identity Access Management (IAM) tools work together to protect cloud-based assets from threats through monitoring and access management.
IAM is a framework of technologies and policies that control user access to the information within an organization. IAM manages user identities, provisions and de-provisions users, authenticates and authorizes users, and provides reporting using tools like Single Sign-On (SSO), multi-factor authentication (MFA), and adaptive authentication.
CASBs work with an organization's IAM tools to ensure access is secure from all angles, primarily by providing visibility into the access landscape and the associated risks that IAM tools cannot uncover on their own. CASBs monitor activity across cloud-based services, alert IAM tools when new devices appear on the network, and communicate what credentials were used to gain access. The IAM can then verify the user access levels to ensure users have the right permissions and block or remove privileges as needed.
What Are Some Challenges With CASB?
The main limitation of a CASB solution is integrating it with the rest of your organization’s standalone security solutions. Each additional cybersecurity solution increases the complexity (and subsequently the cost) of managing security since every security solution must be acquired, provisioned, monitored, and maintained separately.
CASB’s biggest challenge to implementation also highlights why the software is so necessary for enterprises that have already invested heavily in on-premises security solutions: these organizations need a technology that can consolidate their standalone security measures into a streamlined, cloud-optimized solution.
Streamline Your Network Infrastructure Access With StrongDM
Juggling security and access across complex enterprise networks presents challenges and often involves competing priorities. As cloud-based workforces gain in popularity, organizations must find solutions that enable secure management across legacy, cloud, and even multi-cloud environments.
StrongDM is an infrastructure access platform that delivers secure access controls for any network environment—combining authentication, authorization, networking, and observability into one platform. It eliminates point solutions, covers all protocols, and delights both admins and end users alike.
Want to learn more? Get started with a Free StrongDM Trial.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Schuyler Brown, Chairman of the Board, began working with startups as one of the first employees at Cross Commerce Media. Since then, he has worked at the venture capital firms DFJ Gotham and High Peaks Venture Partners. He is also the host of Founders@Fail and author of Inc.com's "Failing Forward" column, where he interviews veteran entrepreneurs about the bumps, bruises, and reality of life in the startup trenches. His leadership philosophy: be humble enough to realize you don’t know everything and curious enough to want to learn more. He holds a B.A. and M.B.A. from Columbia University. To contact Schuyler, visit him on LinkedIn.
You May Also Like