Alternatives to Teleport


Written by
John MartinezLast updated on:
October 24, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
If you’re looking for a Teleport alternative, you’re likely either frustrated with configuration management and protocol limitations, or you are looking for a secure privileged access management solution and want to see if there’s a better option on the market.
Teleport is an Open Infrastructure Access Platform used by DevSecOps teams for SSH, Kubernetes, databases, internal web applications, and Windows. Here are some of Teleport’s features:
- Certificate authentication for SSH and Kubernetes
- Access to databases, internal web applications, and Windows
- Role-based access control
- Just-in-Time access through ChatOps
- Session recording
- Audit logs
Need a better fit for these use cases? Our list of Teleport alternatives has you covered.
1. StrongDM
StrongDM is a Zero Trust Privileged Access Management (PAM) platform that extends Privileged Access Management (PAM) to work across any environment on-premises and in the cloud. It is designed to make access least-privilege by default with role-based, attribute-based, policy-based, and just-in-time access controls. Companies like Humana, SentinelOne, and more have adopted StrongDM to secure access management to all their critical infrastructure.
It easily integrates into existing DevOps pipelines, supporting automated Terraform deployment and secure access provisioning from day one, with support for 100+ protocols, ephemeral credentials, and just-in-time (JIT) access controls.
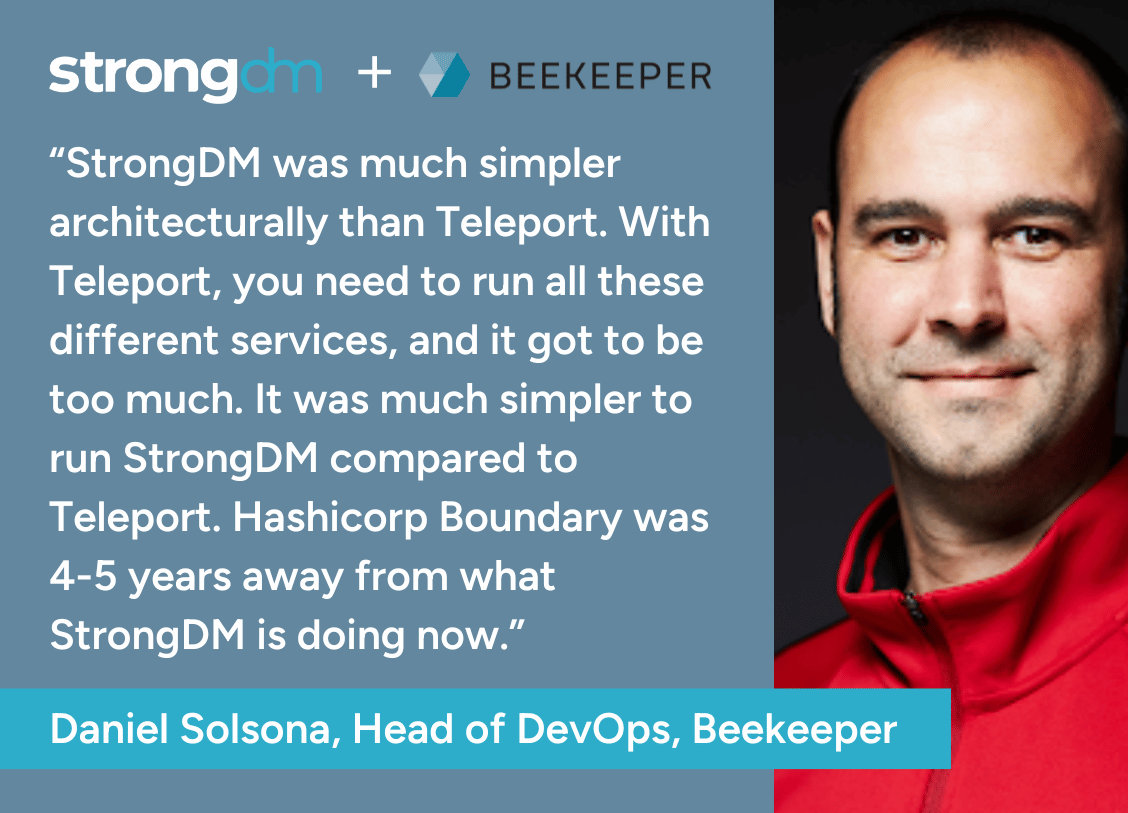
"Like AWS for computing power and Kubernetes for container orchestration, StrongDM is the gold standard for access and auditing. Developers won’t tolerate tools that slow them down or force them to use substandard workflows. StrongDM is the only security product that actually makes their lives easier.”
- Drew Blas, Director of Internal Engineering, Betterment
6 Reasons to Choose StrongDM Over Teleport
1. Deploys Across Your Entire Environment: StrongDM is a complete privileged access solution for the enterprise that allows users to authenticate using credentials, cloud-native authentication, or certificate-based authentication. It supports a large breadth of systems and protocols, including older systems that enterprises still rely on.
2. Integrates with Existing Security Tools: StrongDM can leverage existing integrations with your vault, PAM, or IGA solutions and give you time to transition on your own schedule. Teleport does not integrate with other elements of the security ecosystem, limiting your ability to leverage existing vaults and forcing you to replicate your investment in IGA, device posture, etc.
StrongDM also includes built-in Slack integration to streamline access requests and approval workflows directly from team communication channels, plus ServiceNow, Jira and Microsoft Teams integrations, access workflows automation, and audit APIs with 13-month data retention.
3. Identity Lifecycle Management: StrongDM automates joiner, mover, leaver workflows through SCIM integration with major identity providers like Okta and Azure. It also supports cloud-native authentication and certificate-based authentication. Teleport's exclusive reliance on certificates and cloud provider IAM authentication limits the range of systems it can interface with and constrains operational flexibility.
4. Easy to Adopt, Manage, and Maintain: StrongDM does not require agents on end resources. Agentless architecture means fewer administrative headaches in managing the solution and faster time-to-value for the product.
Moreover, StrongDM updates without any downtime. Teleport requires downtime to update, limiting access to resources and making it harder to adhere to compliance policies.
5. Secure and Auditable: StrongDM allows you to audit your complete access profile at any point in time. With multiple analytics dashboards to evaluate your PAM deployment. Teleport has no such reporting capability, making it difficult to prove to an auditor who had access to which systems.
6. Zero Trust Context-Based Policies: Customers can define context-aware policies against StrongDM resources and enforce them with a centralized configuration. Teleport offers an access graph for comprehensive visibility of policies without centralized access management capabilities
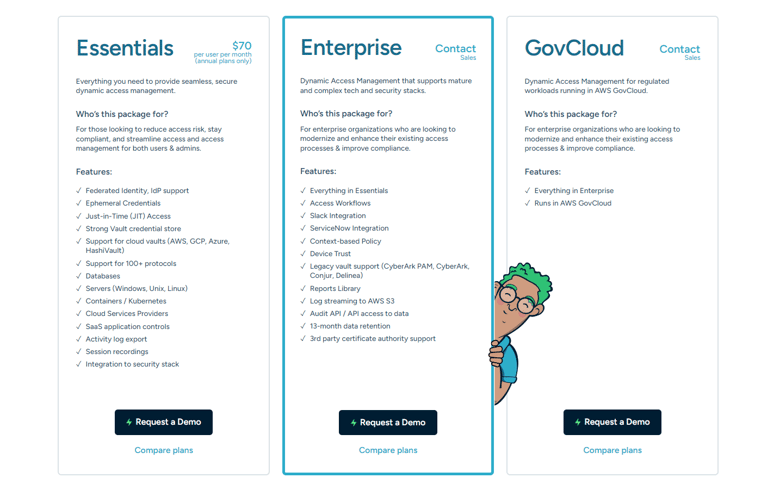
Some of StrongDM’s Features
- Access to databases, cloud, servers, clusters, and internal web applications.
- Dynamic Access Rules: StrongDM supports role-based and attribute-based access controls so that only the right users have access to the resources they need. StrongDM also supports change management. If users switch teams, their access is immediately revoked, and they are assigned resources based on their new role.
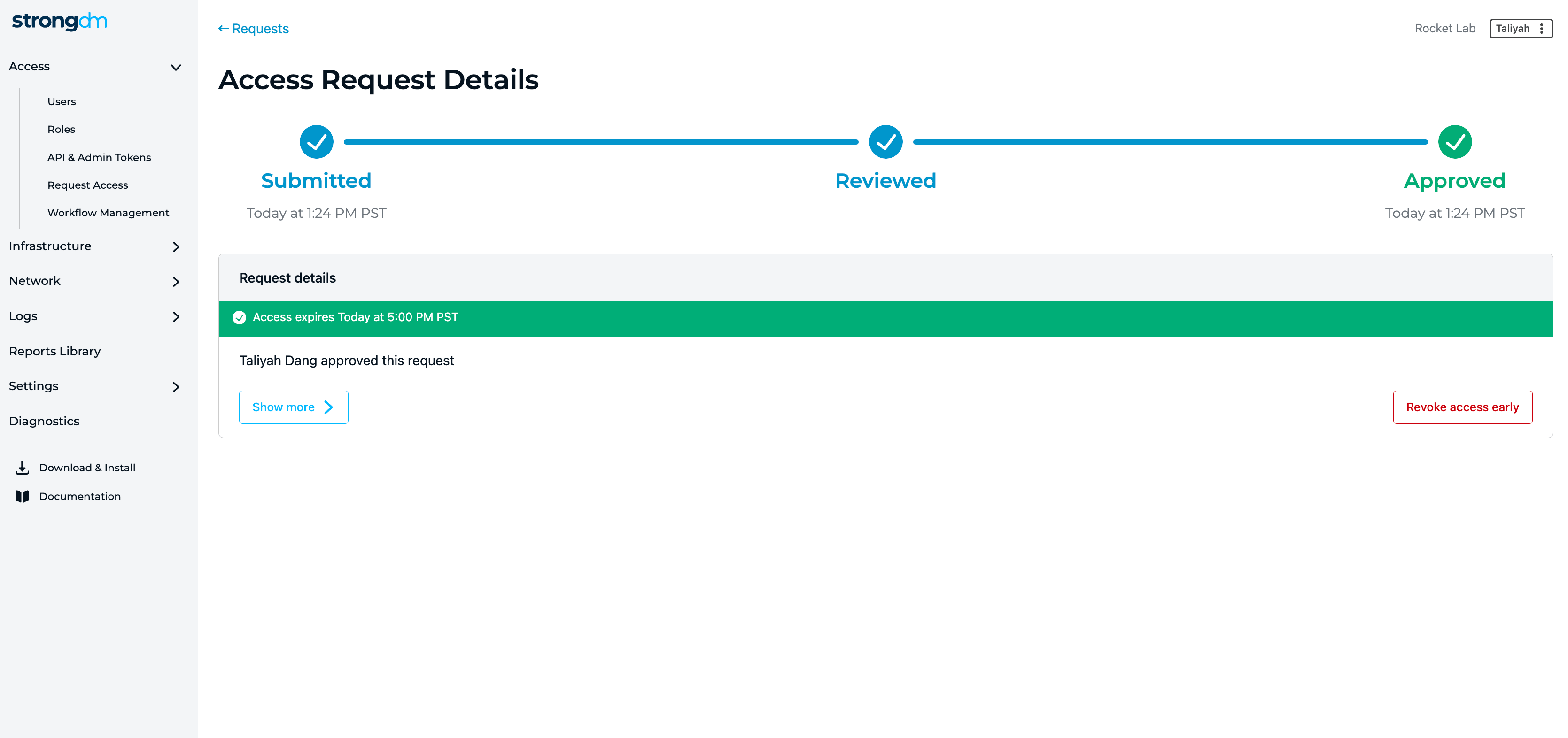
- Just-in-Time access: Request access to resources through StrongDM’s Access Workflows. Automate access or require manager approval based on the resource type.
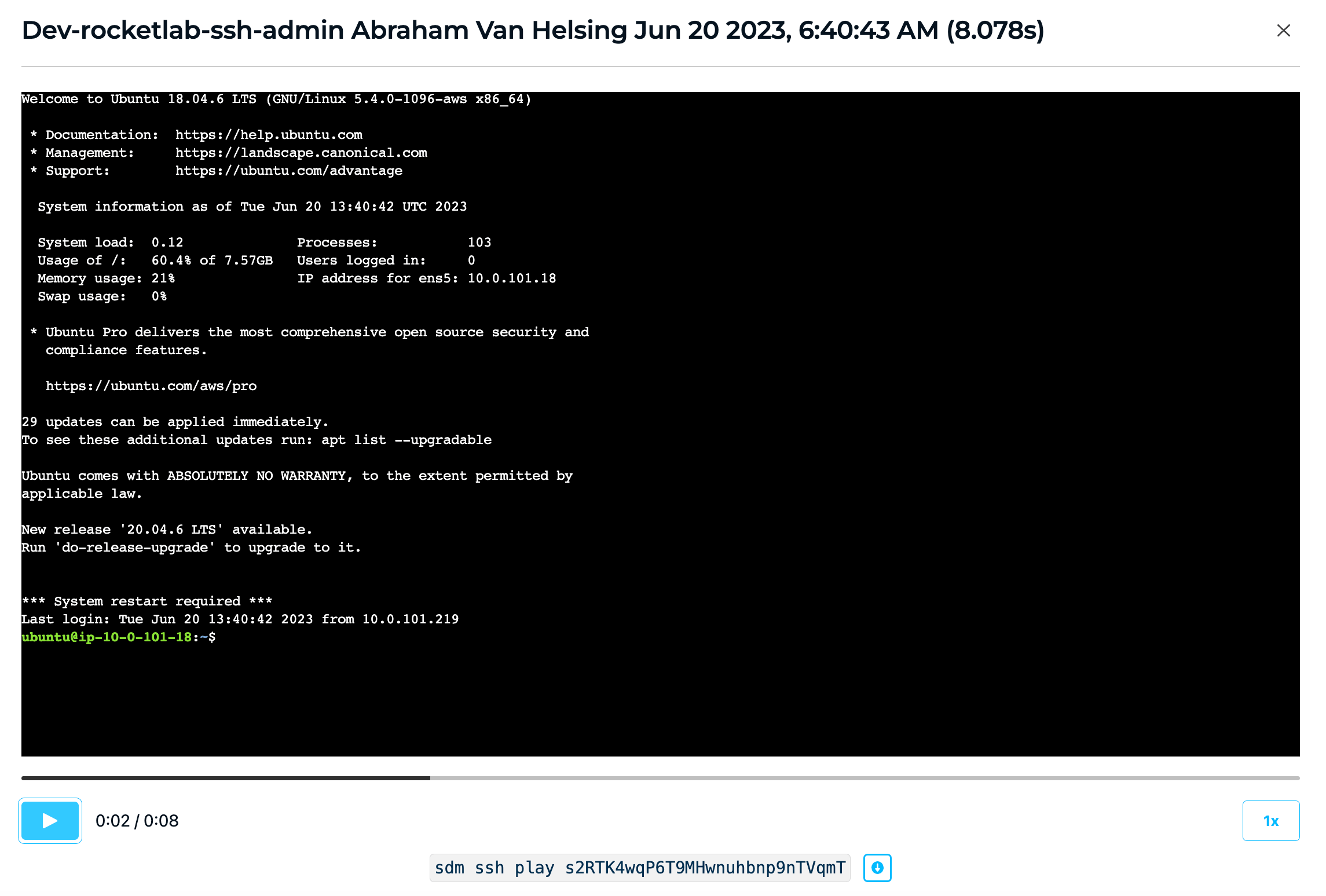
- Session recording: All SSH, RDP, and Kubernetes sessions are recorded with the ability to playback and text-search each session. Helping customers reduce Mean Time To Investigate (MTTI) and Mean To Respond (MTTR) for incident investigations.
- StrongDM provides a Reports Library to report on unused privileged access, sensitive access grants, and an overall access review at any point in time.
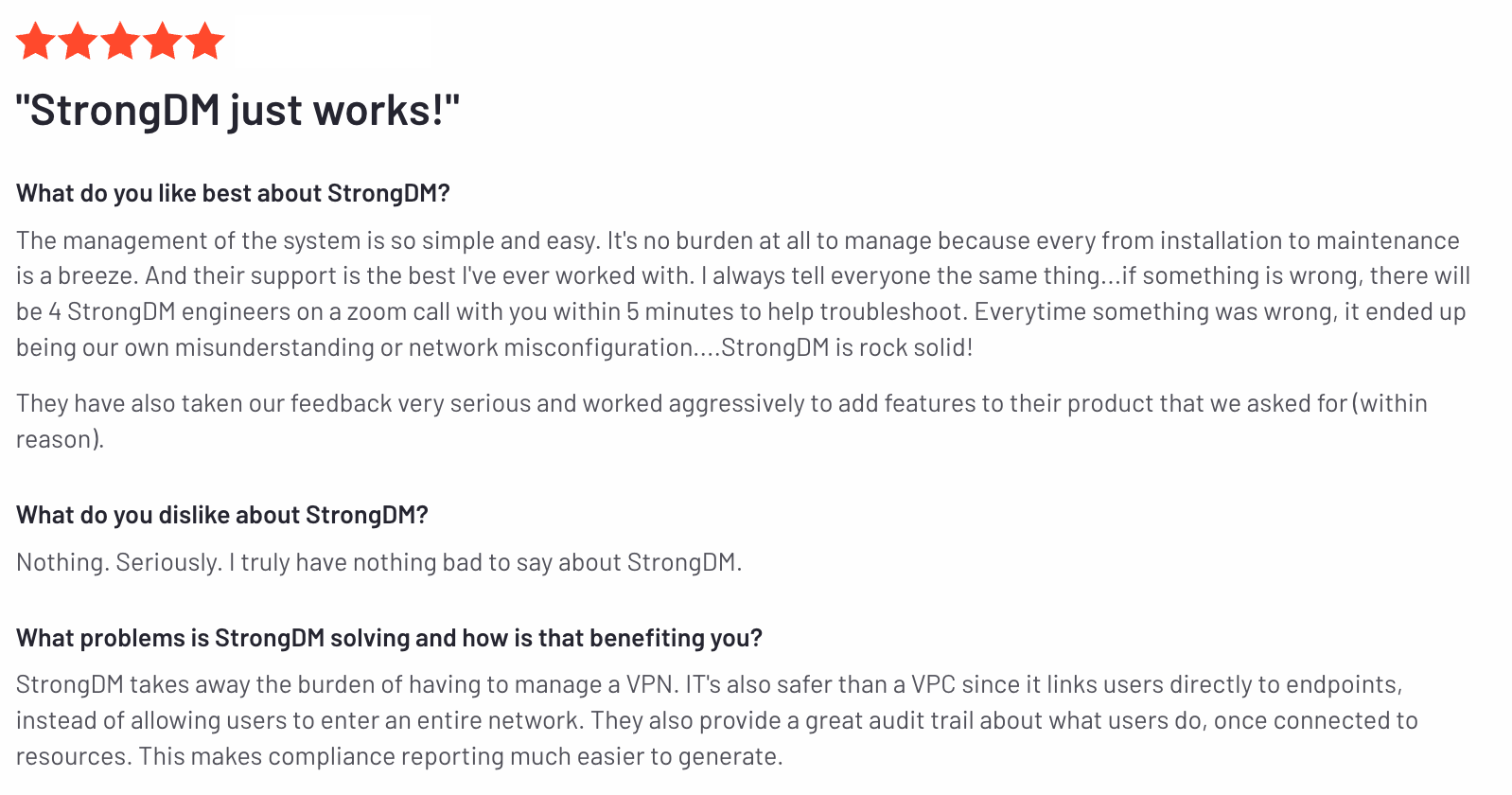
StrongDM’s G2 Reviews
- 67 reviews (at the time of writing)
- 4.7 / 5 stars
Read all of StrongDM’s G2 reviews here.
Pricing Information
StrongDM offers a per/user pricing model that includes support for all resource types.
Users have the option to sign up for a free 14-day trial.
2. HashiCorp Boundary
Brief product summary
HashiCorp Boundary is an open-source identity access management (IAM) tool that facilitates secure user access to dynamic hosts and critical infrastructure across environments.
Use cases
- Hashicorp Boundary is open-source and free identity-based security.
- Role-based and logical service authorization.
- Use SSO to manage, onboard, and offboard users.
- Integrate with existing tools and APIs.
Pluses
- Dynamic resource catalogs.
- Dynamic credentials.
- Integration with Vault and others for end-to-end dynamic credentials.
- Authenticate with the identity provider already in use.
Minuses
- Tools are confusing.
- Complex setup with lots of "moving parts." Users have trouble figuring out what to run together and how to integrate.
- Requires a third tool, Consul, to manage services and machine-to-machine access.
3. Teleport Community Edition
Brief product summary
The open-source Community Edition of Teleport is the same as the Enterprise edition, with the following exceptions:
- No RBAC
- No SSO integration
- No paid support available
Use cases
Because Teleport CE is nearly identical to the Teleport Enterprise version, the same use cases apply.
Pluses
- Open source code (https://github.com/gravitational/teleport).
Minuses
- The same minuses as the other version of Teleport apply.
- Because it’s available free, only community support is available.
- The free version is missing important enterprise features (see above).
- Only uses local users or GitHub for identity-based authentication.
4. Bastion Host
Brief product summary
A bastion host is simply a Linux/UNIX server that mediates access to sensitive servers/database access by requiring the user to first log into the bastion host then ‘jump’ to additional resources in the network controlled by the bastion. Organizations simply need to set up an additional server that is both accessible from external sources and is able to connect to internal resources.
Use cases
- Mediate access to protected resources on a restricted network segment.
- Database clients and similar tools can work via bastion host by using port forwarding over the SSH connection.
Pluses
- Free, or nearly so: the only requirement is the cost for the hardware (or virtual server) underlying the bastion host.
- Straightforward access for users who are familiar with SSH.
Minuses
- Because all access to protected resources requires first logging in via command line to the bastion host, the user must have an account on the bastion and a certain level of technical acumen, especially if employing port forwarding for database access.
- The bastion host represents a single point of failure; if it is unavailable all resources behind it are inaccessible. Setting up multiple bastion hosts to mitigate against this possibility means another set of credentials to manage.
- In the case of problems, support is limited to whatever support may be available for the underlying OS running on the bastion host.
- Session logs and database/other protocol activity are not captured.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like



