Access Management for today's dynamic infrastructure
Protect the access of all technical users–not just the privileged. Keep all of your infrastructure connections secure to reduce the attack surface and increase productivity for both users and administrators.
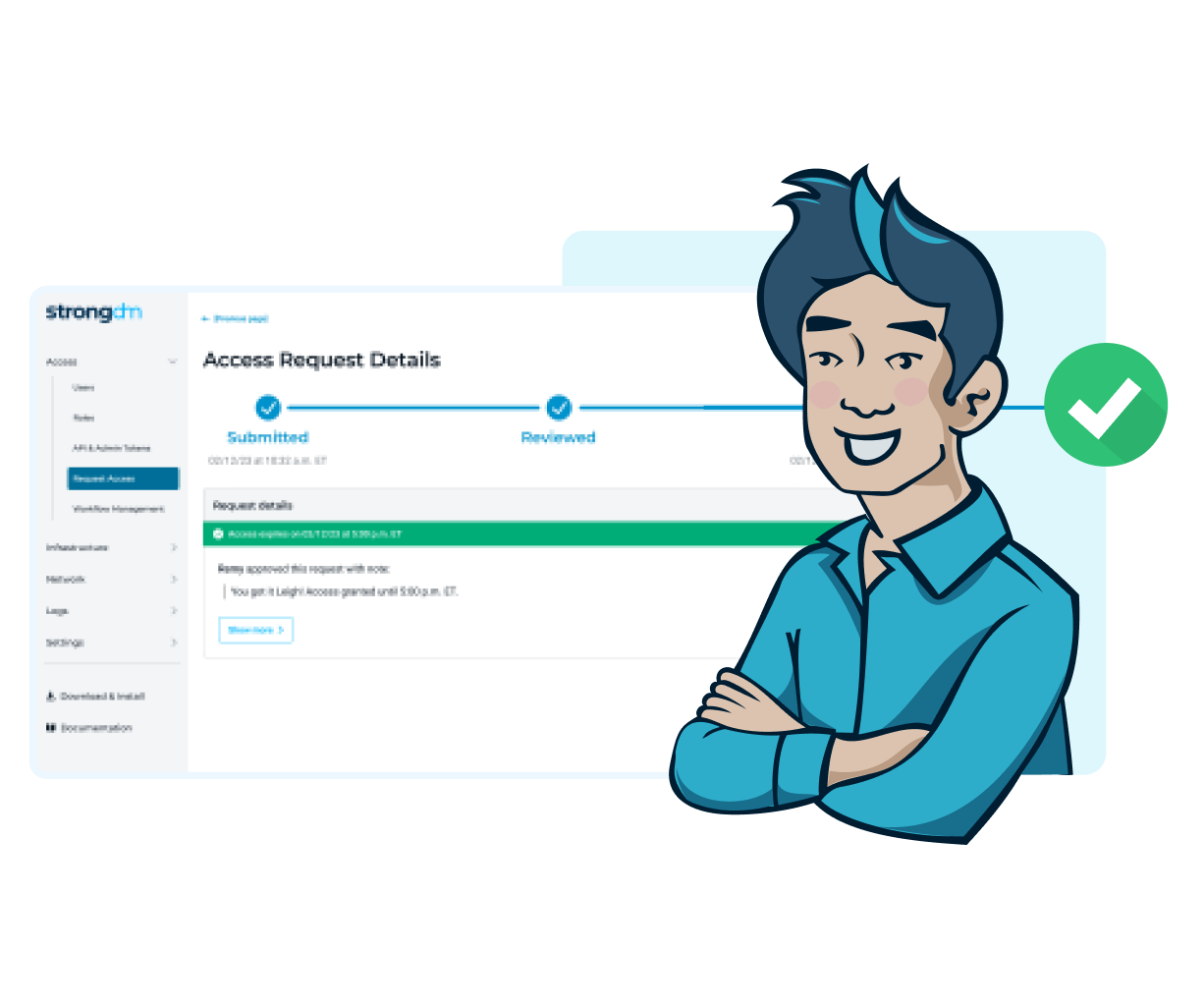
What is StrongDM?
StrongDM is a Zero Trust Privileged Access Management platform that goes beyond the capabilities of traditional privileged access management (PAM) solutions to support all modern infrastructure, providing secure and auditable access for precisely the duration access is needed. You need to secure access for more than just a limited set of privileged users—because today, all users are privileged users. Unlike traditional PAMs, StrongDM supports cloud, modern databases, and ephemeral resources, ensuring that infrastructure is protected. Zero Trust PAM powers just-in-time (JIT) or Zero Standing Privilege (ZSP)—allowing your organization to move faster to reduce static, standing credentials.
Privileged Access That Works With Everything
Security needs to be applied universally. With StrongDM, you can seamlessly and securely apply your access policies to modern and legacy databases, servers, and clusters—both in the cloud and on-prem.
The flexible architecture allows you to leverage the investments your teams already have made in legacy PAM, identity providers, cloud vaults, and SIEMs. No need to rip and replace (unless you want). Instead, augment and extend.

Total Visibility Into Every Access Grant and Keystroke
You can't manage access without having a line of sight into every resource, user and role that exists in your environment. Capture and record the precise details of every single session, query, and command, providing answers to auditors' questions.
Gain insight into what your users are accessing and why with comprehensive logging and robust reporting that integrates with your IGA, SIEM or SOAR tools.

Secure by Design
Add another layer of security by isolating critical assets from direct external access to protect your most sensitive data.
StrongDM's secure proxy technology establishes encrypted connections between users and target resources.
Designed to ensure credentials are always inaccessible to users and never transferred to a client in any form, StrongDM helps keep your secrets from escaping into the wild.
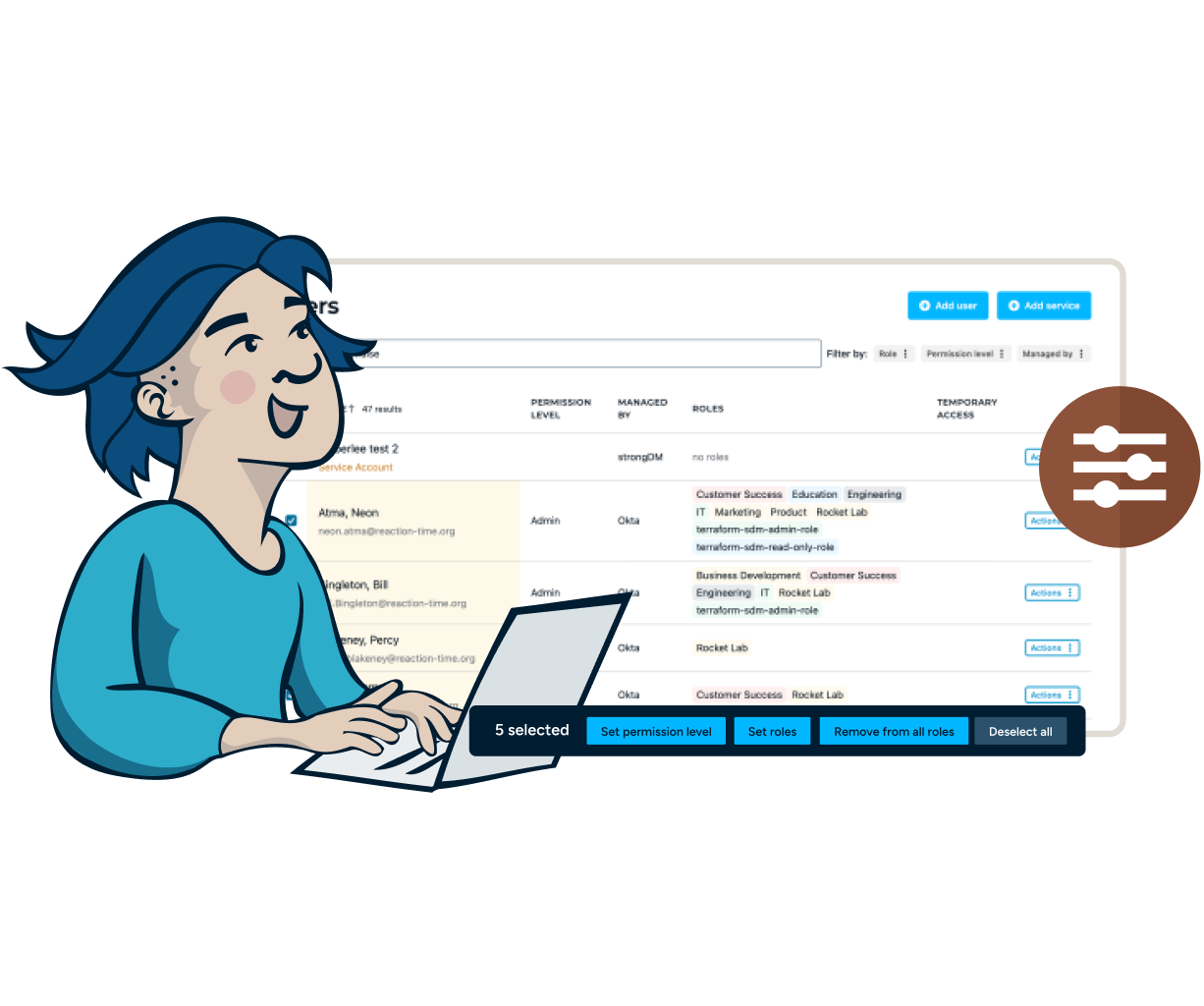
Precise Control
Easily track and manage every permission with automated just-in-time (JIT), temporary, role-based, attribute-based, or direct access.
Revoke access in real time through your identity provider and end sessions in their track.
Reach your Zero Trust goals faster with StrongDM access workflows. Access can be granted just-in-time, eliminating standing access to resources and achieving a stronger least-privilege posture.
Read why just-in-time access is table stakes for the modern stack.

Security That Users Adopt
"Secure Access" and "Easy to Use" must not be at odds. In order to ensure full adoption and compliance, user and admin experiences must be simple. With StrongDM, your users won't circumvent security because access is on-time, every time.
Native protocol support allows developers to continue to use the tools they prefer.
With SDKs in multiple languages and open APIs, StrongDM fits into your infrastructure-as-code workflows to streamline deployment and maintenance.
Complete visibility and total control.
Across your entire stack.
Free for 14 days. No credit card required.