Privilege Elevation and Delegation Management (PEDM) Explained


Written by
John MartinezLast updated on:
June 25, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
Summary: In this article, we’ll explore Privileged Elevation and Delegation Management (PEDM). You’ll learn how PEDM works and how it mitigates the risks associated with poorly managed privileged accounts. By the end of this article, you’ll understand why PEDM is an important security strategy and how businesses can use PEDM to manage privileged access and prevent cyberattacks.
What Is Privilege Elevation and Delegation Management (PEDM)?
Privilege Elevation and Delegation Management (PEDM) is a type of Privileged Access Management (PAM). PEDM provides greater security than traditional PAM methods, allowing organizations to use granular controls to elevate access privileges for a limited time.
PEDM mitigates the risks associated with over-privileged accounts by allowing IT administrators to grant just-in-time (JIT) access for a limited time and only when needed. JIT leverages the principle of least privilege to reduce the risk of standing privileges, which allow unrestricted access to infrastructure and other IT resources.
💡Make it easy: Just-in-Time Access works best when it is easy for the end user to request and receive access. It should also be auditing to map the end-to-end chain of events, who is requesting access, why they are requesting it, and for how long. Play the video below to see how easy StrongDM makes Just-in-Time access, and try it yourself.
Importance of PEDM
With 80% of data breaches stemming from the misuse of privileged access, compromised privileged accounts are prime targets for hackers. Weak cybersecurity practices—such as shared credentials, poor password hygiene, manual access management, and over-privileged accounts—increase the chance that a privileged account could be exploited. PEDM mitigates these risks by ensuring elevated privileges are granted only when needed.
Instead of giving users access to critical systems and infrastructure through ephemeral administrative accounts with root-level privileges, PEDM grants privileged access for a limited time upon request. This ensures users can access only the areas they need to complete a specific task, while eliminating opportunities to exploit accounts that carry permanent privileges.
Benefits of PEDM
Privilege Elevation and Delegation Management offers many benefits, all of which support a stronger security posture. By leveraging the principle of least privilege and just-in-time access, PEDM reduces the risks associated with permanently elevated privileges and widespread use of fully privileged administrative accounts. With PEDM, users get admin privileges only temporarily, preventing them from gaining unrestricted access.
💡Make it easy: Fine-tune least privilege by analyzing and responding to comprehensive access insights. Easily report on which privileges are being used (or not). Try it yourself.
In addition, PEDM enhances security by enabling privilege segregation. IT teams can use granular controls to grant privileges to applications, services, processes, and devices—and they can expand those privileges automatically under certain conditions. PEDM validates self-service elevation requests based on predefined criteria to enable automatic, just-in-time approval.
Finally, Privilege Elevation and Delegation Management reduces vulnerability by minimizing the number of privileged accounts and curtailing the need to use fully privileged administrative accounts that grant access to an enterprise’s entire IT infrastructure or tech stack. The result is a smaller attack surface, as hackers will have fewer vectors to exploit.
What Is the Difference Between PEDM and PASM (Privileged Access Session Management)?
There are two types of Privileged Access Management: Privilege Elevation and Delegation Management and Privileged Access Session Management (PASM). While both approaches provide a way to allow just-in-time access to critical infrastructure and applications, sensitive data, and other privileged areas or systems, PEDM and PASM are fundamentally different.
PASM solutions broker shared admin accounts that have root-level privileges. Users who require administrative access to a privileged resource must request permission to use a shared account. If approved, the PASM tool creates a temporary session on the fly using brokered credentials, and then monitors and logs the user’s activity during the session. Because shared admin accounts give users access to the entire system, PASM is less secure than PEDM.
In contrast, Privilege Elevation and Delegation Management manages conventional user accounts, granting individual users only the privileges their respective roles require from day to day. If a user needs additional privileges, a PEDM solution can grant temporary privilege elevation. While PEDM is inherently more secure, PASM and PEDM solutions are complementary. Many organizations use both, reserving PASM for exceptional circumstances.
What Is the Difference Between PEDM and PAM (Privileged Access Management)?
Privilege Elevation and Delegation Management (PEDM) is a subset of Privileged Access Management (PAM) that focuses on temporary privilege elevation and granular access control. While both enhance security by managing privileged access, they serve different functions.
PEDM solution grants just-in-time (JIT) access, ensuring users receive only the privileges they need, only when they need them. It reduces security risks by eliminating standing privileges and limiting exposure to administrative access. Instead of providing permanent high-level access, PEDM temporarily elevates permissions for specific tasks, then automatically revokes them.
PAM solution, on the other hand, is a broader security approach that manages privileged accounts, secures credentials, and monitors privileged sessions. It controls access to sensitive systems, often requiring users to log in with shared administrative accounts or request privileged session approval.
While PEDM minimizes risk by limiting how long privileges are available, PAM ensures that who has access and what they can do is tightly controlled. Together, they provide a comprehensive security strategy—PEDM for limiting privilege exposure and PAM for centralizing and securing privileged access.
How Does PEDM Work? PEDM Framework
Privilege Elevation and Delegation Management leverages granular access controls to manage individual users’ privileges. It allows privileges to be assigned according to a user’s role. Each user receives the minimum privileges required to do their job. These permissions do not extend to tasks beyond their daily job responsibilities. However, users who need access to critical systems can be granted just-in-time privilege elevation for a limited period.
With PEDM, users automatically gain privileged access through their own accounts upon entering their usual login credentials. Because users cannot access administrative accounts with root-level privileges, PEDM requires less monitoring, reduces the attack surface, and mitigates the risk of errors that could damage critical systems. And because there’s no need to request permission and wait for a manager’s approval, employees can be more productive.
PEDM Best Practices
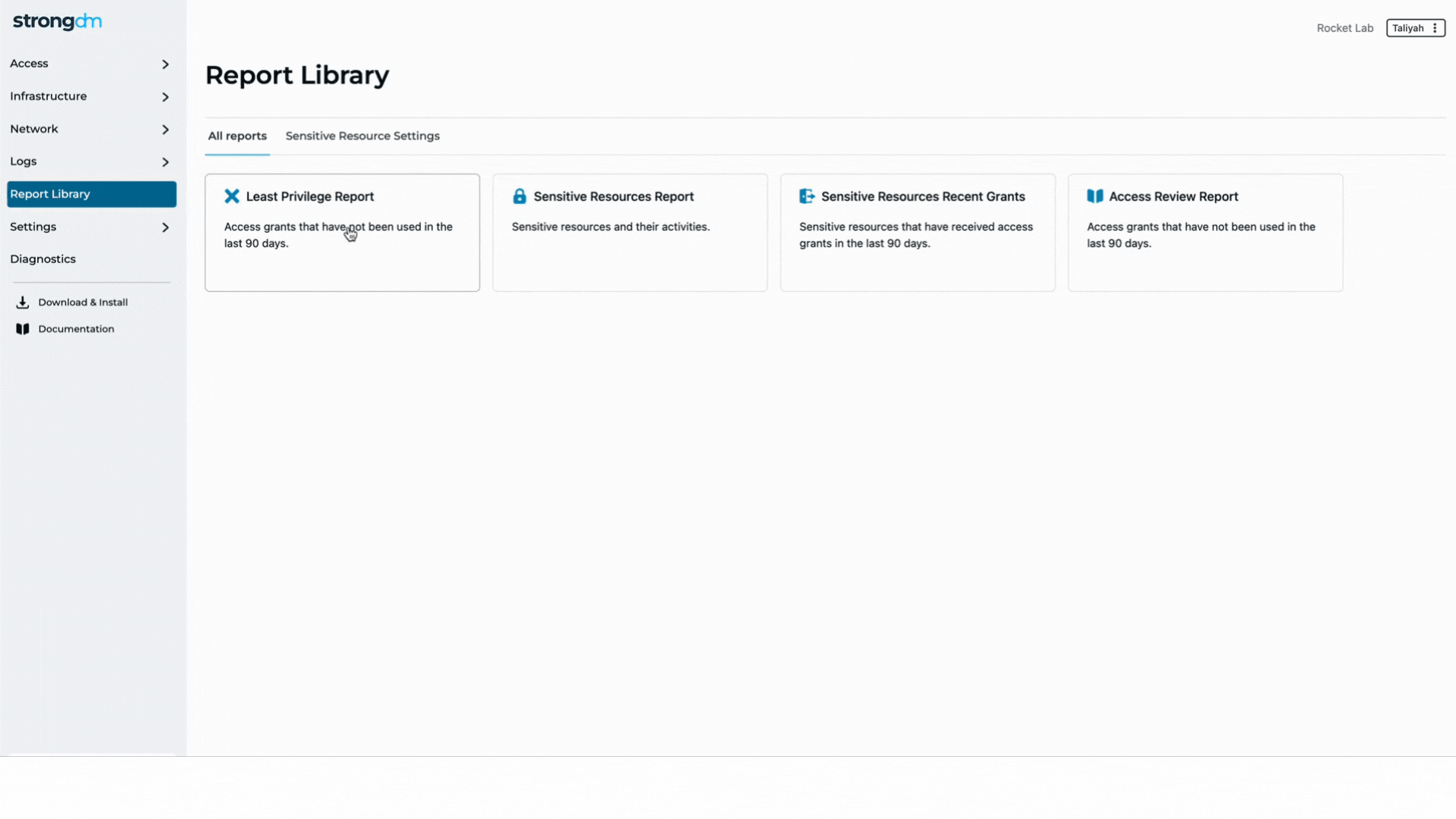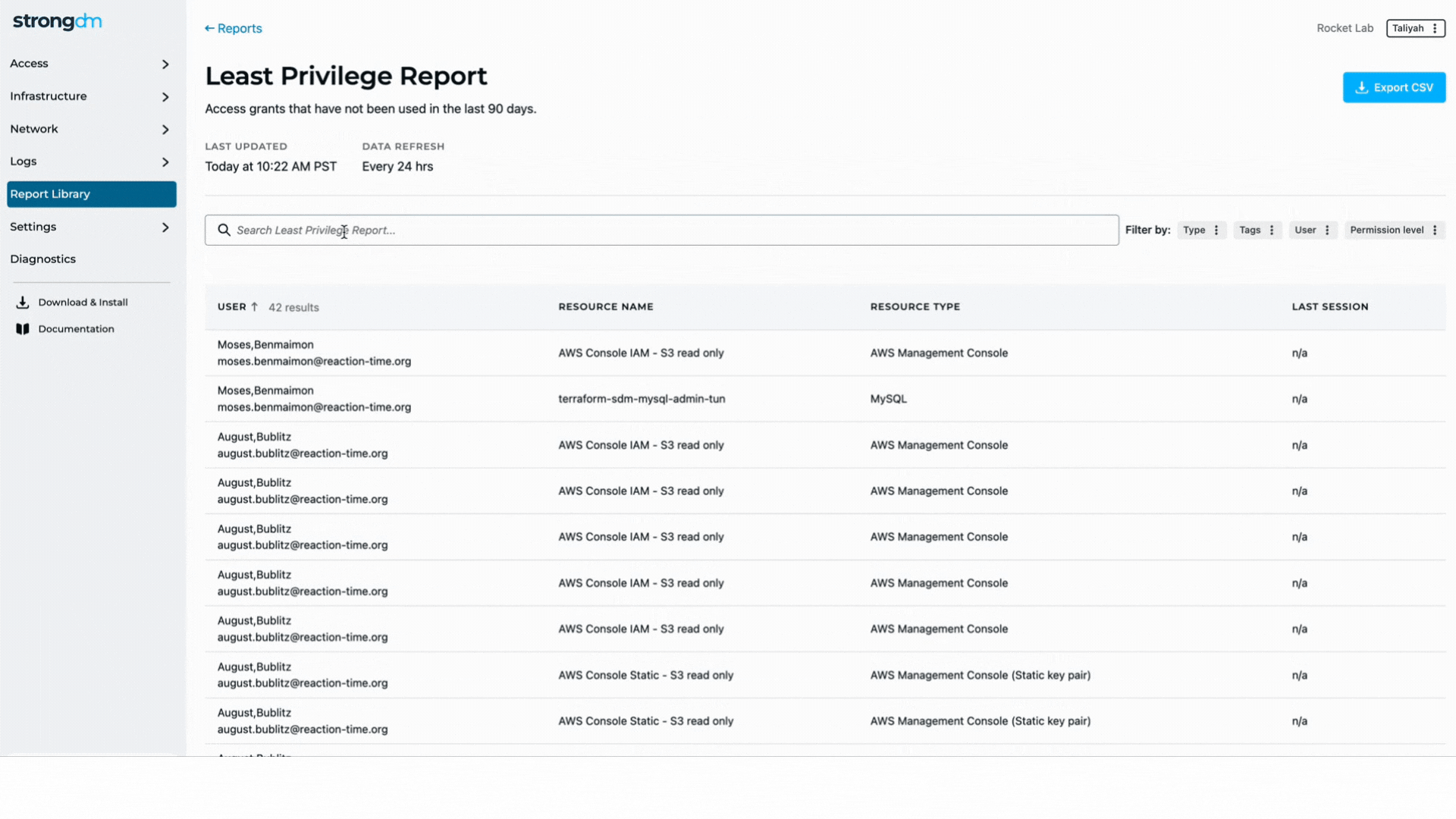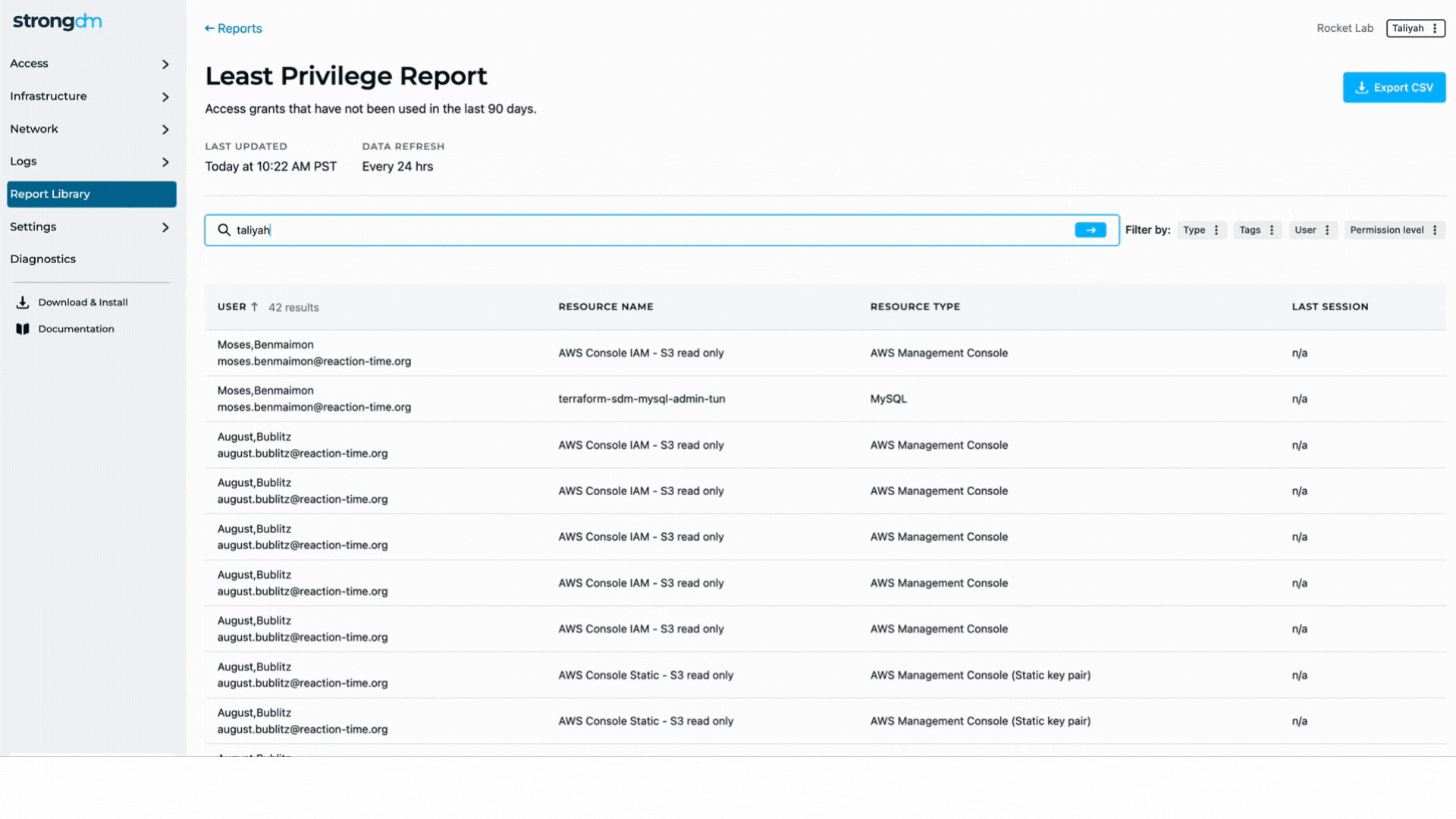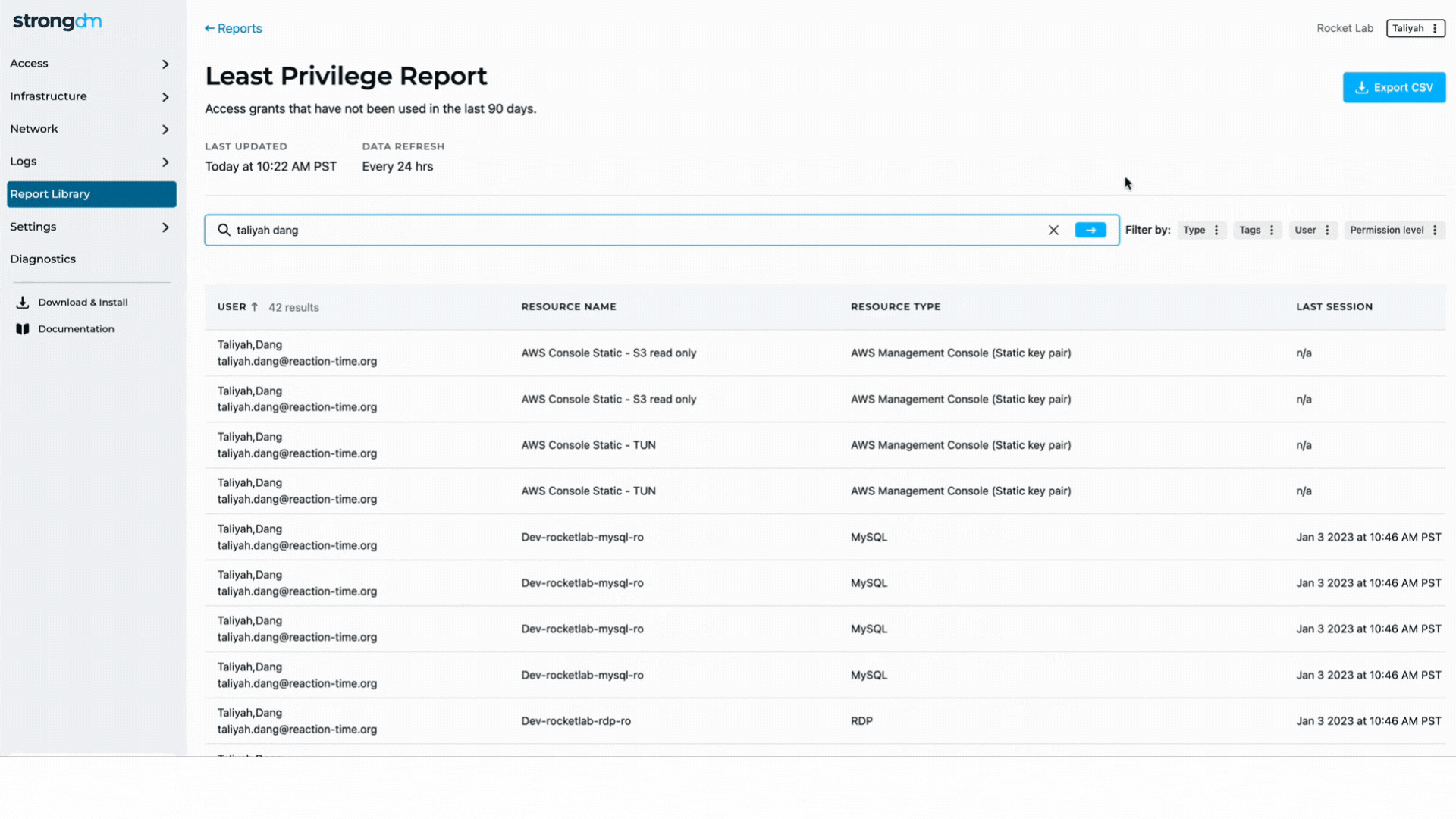
An effective PEDM strategy should begin with an audit to discover how many privileged accounts an organization has. First, separate the high-level system accounts and administrative accounts from end-user accounts. Then ensure the permissions for all accounts are set appropriately, revoking any unaccounted privileged access. End users should be given the minimum privileges needed to perform their tasks.
Assign default privileges to user accounts based on individual users’ roles. Implement control policies to allow temporary, just-in-time privilege elevation when needed. Establish processes to manage the lifecycles of privileged accounts and carefully track every privileged account and what it may access. Following these principles helps ensure older accounts do not become over-privileged as users advance in their careers or change roles.
Leverage best practices—such as single-use passwords, automated monitoring and logging, and auditing—to make users’ activity discoverable. Record privileged sessions and use Privilege Elevation and Delegation Management tools to detect anomalous activity.
How to Simplify PEDM Implementation with StrongDM
With StrongDM’s Zero Trust PAM platform, you can leverage PEDM to grant users frustration-free, just-in-time access and elevate account privileges automatically when the need arises.
StrongDM strengthens your organization’s security by reducing the need to rely on high-risk admin accounts and standing privileges. Employees can gain temporary administrative access to the resources they need when they need them. In addition, StrongDM automatically terminates privileged access when a task is complete.
Upgrade Your Cybersecurity Posture with StrongDM
You can significantly reduce your organization’s attack vector and mitigate the risk of threats by implementing a PEDM strategy that allows just-in-time privilege elevation automatically based on your company’s security policies.
Want to learn more? Get a demo of StrongDM.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.
You May Also Like