Enforce Access Continuously
Not Just at Login
Modern Privileged Access Management with real-time authorization and zero trust enforcement.
Not Just at Login
Across Cloud and Hybrid
With Instant Revoke

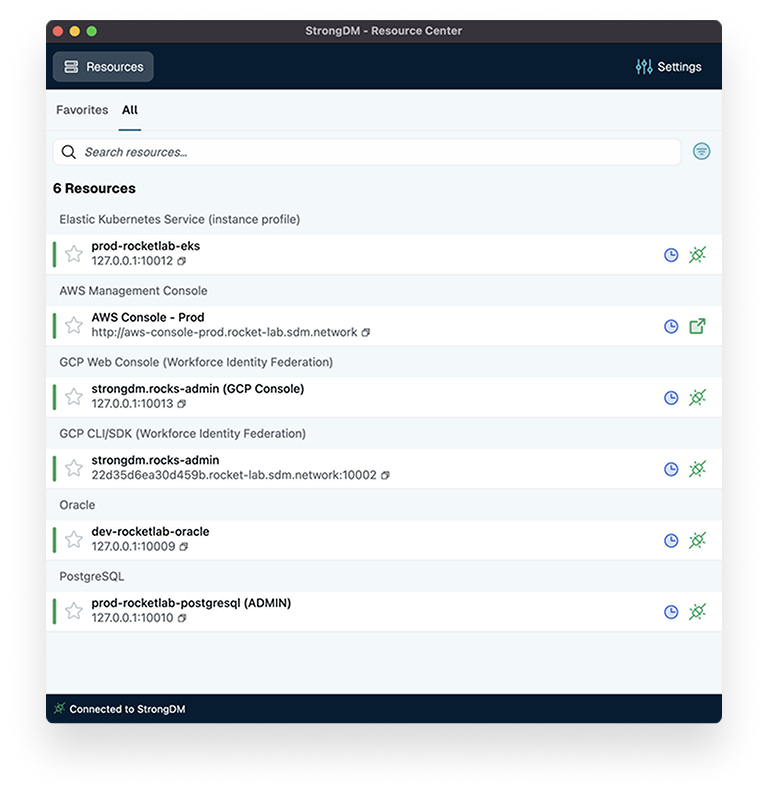
Before StrongDM
After StrongDM
With Legacy PAM |
With StrongDM Zero Trust PAM |
|
Lack of visibility, control, and audit trail for access events across your full tech stack. |
Full visibility, integrated control, and comprehensive audit trails across everything. |
|
Current PAM solutions have poor user experience leading them to circumvent controls. |
Frustration-free access leads to high adoption rate improving security & productivity. |
|
Cumbersome access policy enforcement and management |
Simple, agile, and contextual access policy management and enforcement, enabling granular control. |
|
No control over what people do with their access |
Precise, dynamic privileged action control for any infrastructure or application. |
Leading global brands rely on StrongDM

.png?width=163&height=92&name=Rectangle%204742%20(1).png)
.png?width=163&height=92&name=Rectangle%204743%20(1).png)

.png?width=163&height=92&name=Rectangle%204745%20(1).png)


_HighPerformer_Mid-Market_Americas_HighPerformer.png?width=155&height=178&name=IdentityandAccessManagement(IAM)_HighPerformer_Mid-Market_Americas_HighPerformer.png)
_HighPerformer_Americas_HighPerformer.png?width=155&height=178&name=IdentityandAccessManagement(IAM)_HighPerformer_Americas_HighPerformer.png)
_Leader_Leader.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_Leader_Leader.png)
_UsersMostLikelyToRecommend_Small-Business_Nps.png?width=155&height=179&name=PrivilegedAccessManagement(PAM)_UsersMostLikelyToRecommend_Small-Business_Nps.png)
_BestSupport_Small-Business_QualityOfSupport.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_BestSupport_Small-Business_QualityOfSupport.png)
_EasiestToUse_Small-Business_EaseOfUse.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_EasiestToUse_Small-Business_EaseOfUse.png)
_EasiestToDoBusinessWith_Small-Business_EaseOfDoingBusinessWith.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_EasiestToDoBusinessWith_Small-Business_EaseOfDoingBusinessWith.png)
_Leader_Mid-Market_Leader.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_Leader_Mid-Market_Leader.png)
