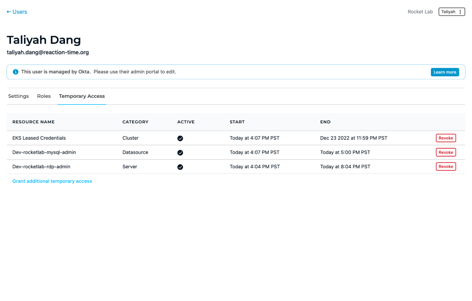
Don’t let vendor vulnerabilities provide a backdoor into your infrastructure. Control and monitor the access privileges of third-party users with just-in-time access to your organization’s systems, networks, and data–without revealing credentials or requiring a VPN.




_HighPerformer_Mid-Market_Americas_HighPerformer.png?width=155&height=178&name=IdentityandAccessManagement(IAM)_HighPerformer_Mid-Market_Americas_HighPerformer.png)
_HighPerformer_Americas_HighPerformer.png?width=155&height=178&name=IdentityandAccessManagement(IAM)_HighPerformer_Americas_HighPerformer.png)
_Leader_Leader.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_Leader_Leader.png)
_UsersMostLikelyToRecommend_Small-Business_Nps.png?width=155&height=179&name=PrivilegedAccessManagement(PAM)_UsersMostLikelyToRecommend_Small-Business_Nps.png)
_BestSupport_Small-Business_QualityOfSupport.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_BestSupport_Small-Business_QualityOfSupport.png)
_EasiestToUse_Small-Business_EaseOfUse.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_EasiestToUse_Small-Business_EaseOfUse.png)
_EasiestToDoBusinessWith_Small-Business_EaseOfDoingBusinessWith.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_EasiestToDoBusinessWith_Small-Business_EaseOfDoingBusinessWith.png)
_Leader_Mid-Market_Leader.png?width=155&height=178&name=PrivilegedAccessManagement(PAM)_Leader_Mid-Market_Leader.png)
