Written by
Maile McCarthyLast updated on:
November 9, 2022Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
The world has changed. Decentralized workforces are now the norm, with employees from across an organization requiring access to critical infrastructure—not just engineers but marketers, product managers, salespeople, and more. And these users need access to a broad range of infrastructure from an increasingly complex stack.
Our recent survey looked at the benefits and pitfalls of modern infrastructure access management. The key takeaway: Existing approaches, like Privileged Access Management (PAM), are too narrow and just aren’t working.
Access Challenges Persist
While the PAM market has existed for a while, those tools do not solve the complete access challenge. The same problems PAM tools claim to solve are still the primary challenges companies face.
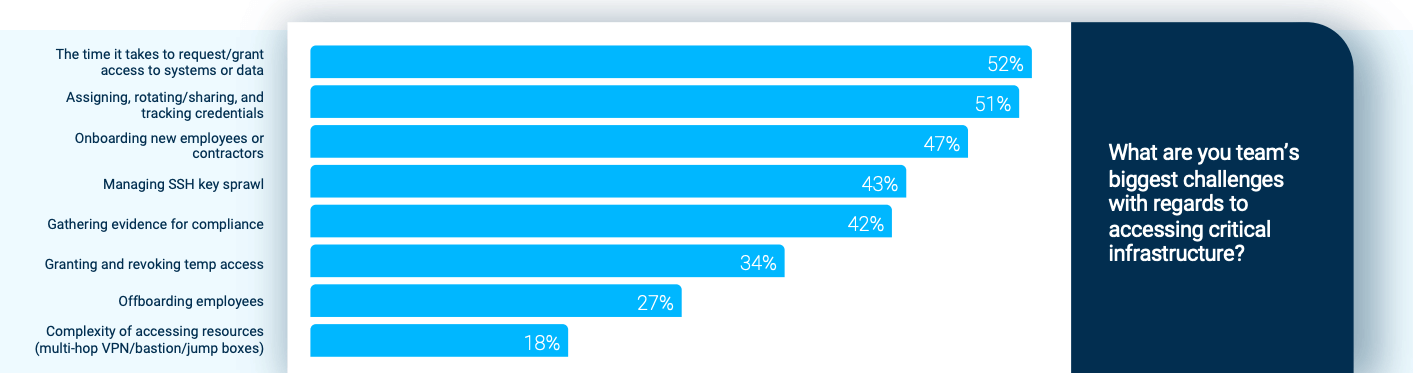
For example, 51% of the respondents in our survey want to improve their process of assigning, rotating/sharing, and tracking the credentials needed to access sensitive resources. And more than a third seek a better way to grant and revoke temporary access, even though these are the very solutions PAM tools claim to provide.
In reality, current PAM offerings tend to fall short when users need to manage access to a breadth of resources. These tools lack complete auditing ability and can be costly and difficult to deploy, often leading users to abandon them altogether.
PAM’s Scope is Too Small
Other challenges—such as onboarding and compliance—go well beyond privileged access.
Onboarding new employees or contractors is a significant pain point for nearly half of the tech professionals we surveyed. Getting new employees connected to the resources they need can take days, weeks, or even months. And that waiting adds more than just wasted time, money, and productivity. It also creates friction for new employees who are learning the ropes and trying to find their place within the team.
People who feel valued by and connected to their co-workers are more likely to stay in their jobs—and stay longer. In turn, better employee retention leads to greater productivity, more engaged employees, and (in many cases) longer-lasting customer relationships. So access frustration among new hires is a problem that merits attention.
Compliance is another area where PAM has room to grow. In theory, these tools should help you gather evidence for compliance with industry and government regulations like SOC 2, HIPAA, and ISO27001 by tracking access to critical infrastructure and either sending that data on to logging tools or generating reports that a human can read and understand. Unfortunately, the native reporting these tools offer is often limited and clunky, and integrating with third-party analytics platforms can require extensive training.
Our survey supports this finding. With 42% of DevOps professionals struggling to gather evidence for compliance, it’s clear that something needs to change.
Change is not a Four-letter Word
PAM tools are poorly adopted because they slow down developers and add complexity to administrative workflows. And that’s if you can get them to work at all! Our survey found that 80% of organizations list Access Management as a critical initiative, yet Gartner reports PAM market growth at a modest 12% from 2019 to 2020. It’s easy to see why.
Implementation can be problematic, requiring comprehensive, product-specific training to troubleshoot issues and upgrade systems. And once things are up and running, new challenges arise. Administrators and users must learn new workflows in which access to infrastructure often requires additional steps.
Change doesn’t need to be so hard. It’s time for PAM to evolve to better support complex environments in a way that puts people first. This evolution should be secure by default, simple to audit, and able to manage access to a breadth of resources without sacrificing user happiness. Who says you can’t have your infrastructure and access it too?
Want to learn more about the access challenges PAM users encounter in modern tech environments? Check out the full report, 2022: The Year of Access. Then schedule a free demo of StrongDM to see how you can upgrade your access management today.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial


About the Author
Maile McCarthy, Contributing Writer and Illustrator, has a passion for helping people bring their ideas to life through web and book illustration, writing, and animation. In recent years, her work has focused on researching the context and differentiation of technical products and relaying that understanding through appealing and vibrant language and images. She holds a B.A. in Philosophy from the University of California, Berkeley. To contact Maile, visit her on LinkedIn.
You May Also Like